Practice Free SY0-701 Exam Online Questions
During an investigation, an incident response team attempts to understand the source of an incident.
Which of the following incident response activities describes this process?
- A . Analysis
- B . Lessons learned
- C . Detection
- D . Containment
A
Explanation:
Analysis is the incident response activity that describes the process of understanding the source of an incident. Analysis involves collecting and examining evidence, identifying the root cause, determining the scope and impact, and assessing the threat actor’s motives and capabilities. Analysis helps the incident response team to formulate an appropriate response strategy, as well as to prevent or mitigate future incidents. Analysis is usually performed after detection and before containment, eradication, recovery, and lessons learned.
Reference: CompTIA Security+ Study Guide with over 500 Practice Test Questions: Exam SY0-701, 9th Edition, Chapter 6, page 223. CompTIA Security+ SY0-701 Exam Objectives, Domain 4.2, page 13.
An organization implemented cloud-managed IP cameras to monitor building entry points and sensitive areas. The service provider enables direct TCP/IP connection to stream live video footage from each camera. The organization wants to ensure this stream is encrypted and authenticated.
Which of the following protocols should be implemented to best meet this objective?
- A . SSH
- B . SRTP
- C . S/MIME
- D . PPTP
A spoofed identity was detected for a digital certificate.
Which of the following are the type of unidentified key and the certificate mat could be in use on the company domain?
- A . Private key and root certificate
- B . Public key and expired certificate
- C . Private key and self-signed certificate
- D . Public key and wildcard certificate
A company needs to provide administrative access to internal resources while minimizing the traffic allowed through the security boundary.
Which of the following methods is most secure?
- A . Implementing a bastion host
- B . Deploying a perimeter network
- C . Installing a WAF
- D . Utilizing single sign-on
A
Explanation:
A bastion host is a special-purpose server that is designed to withstand attacks and provide secure access to internal resources. A bastion host is usually placed on the edge of a network, acting as a gateway or proxy to the internal network. A bastion host can be configured to allow only certain types of traffic, such as SSH or HTTP, and block all other traffic. A bastion host can also run security software such as firewalls, intrusion detection systems, and antivirus programs to monitor and filter incoming and outgoing traffic. A bastion host can provide administrative access to internal resources by requiring strong authentication and encryption, and by logging all activities for auditing purposes12.
A bastion host is the most secure method among the given options because it minimizes the traffic allowed through the security boundary and provides a single point of control and defense. A bastion host can also isolate the internal network from direct exposure to the internet or other untrusted networks, reducing the attack surface and the risk of compromise3.
Deploying a perimeter network is not the correct answer, because a perimeter network is a network segment that separates the internal network from the external network. A perimeter network usually hosts public-facing services such as web servers, email servers, or DNS servers that need to be accessible from the internet. A perimeter network does not provide administrative access to internal resources, but rather protects them from unauthorized access. A perimeter network can also increase the complexity and cost of network management and security4.
Installing a WAF is not the correct answer, because a WAF is a security tool that protects web applications from common web-based attacks by monitoring, filtering, and blocking HTTP traffic. A WAF can prevent attacks such as cross-site scripting, SQL injection, or file inclusion, among others. A WAF does not provide administrative access to internal resources, but rather protects them from web application vulnerabilities. A WAF is also not a comprehensive solution for network security, as it only operates at the application layer and does not protect against other types of attacks or threats5.
Utilizing single sign-on is not the correct answer, because single sign-on is a method of authentication that allows users to access multiple sites, services, or applications with one username and password. Single sign-on can simplify the sign-in process for users and reduce the number of passwords they have to remember and manage. Single sign-on does not provide administrative access to internal resources, but rather enables access to various resources that the user is authorized to use. Single sign-on can also introduce security risks if the user’s credentials are compromised or if the single sign-on provider is breached6. Reference 1: Bastion host – Wikipedia, 2: 14 Best Practices to Secure SSH Bastion Host – goteleport.com, 3: The Importance Of Bastion Hosts In Network Security, 4: What is the network perimeter? | Cloudflare, 5: What is a WAF? | Web Application Firewall explained, 6: [What is single sign-on (SSO)? – Definition from WhatIs.com]
Which of the following are the best security controls for controlling on-premises access? (Select two.)
- A . Swipe card
- B . Picture ID
- C . Phone authentication application
- D . Biometric scanner
- E . Camera
- F . Memorable QUESTIO N N O:
A, D
Explanation:
Swipe cards and biometric scanners are commonly used to control on-premises access due to their reliability and ability to restrict unauthorized entry. Swipe cards provide physical access control, while biometric scanners ensure identity verification.
Reference: CompTIA Security+ SY0-701 Study Guide, Domain 1: General Security Concepts, Section: "Physical Security Controls".
HOTSPOT
You are security administrator investigating a potential infection on a network.
Click on each host and firewall. Review all logs to determine which host originated the Infecton and then deny each remaining hosts clean or infected.







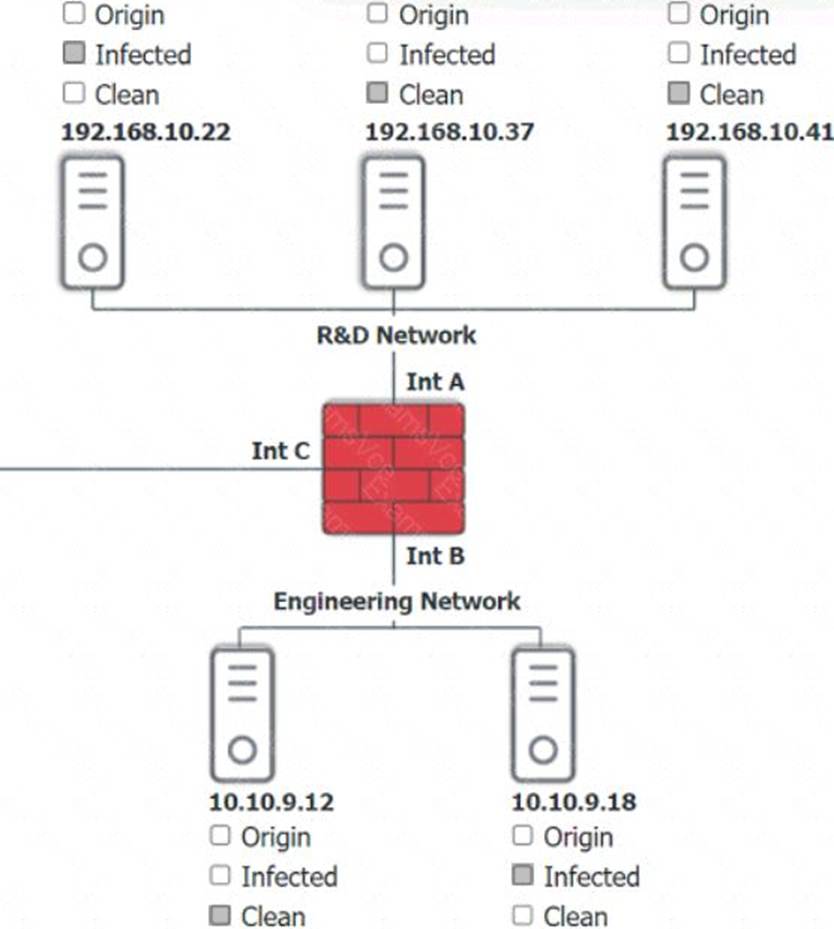
Explanation:
Based on the logs, it seems that the host that originated the infection is 192.168.10.22. This host has a suspicious process named svchost.exe running on port 443, which is unusual for a Windows service. It also has a large number of outbound connections to different IP addresses on port 443, indicating that it is part of a botnet.
The firewall log shows that this host has been communicating with 10.10.9.18, which is another infected host on the engineering network. This host also has a suspicious process named svchost.exe running on port 443, and a large number of outbound connections to different IP addresses on port 443.
The other hosts on the R&D network (192.168.10.37 and 192.168.10.41) are clean, as they do not have any suspicious processes or connections.
An IT security team is concerned about the confidentiality of documents left unattended in MFPs.
Which of the following should the security team do to mitigate the situation?
- A . Educate users about the importance of paper shredder devices.
- B . Deploy an authentication factor that requires ln-person action before printing.
- C . Install a software client m every computer authorized to use the MFPs.
- D . Update the management software to utilize encryption.
A security engineer is implementing FDE for all laptops in an organization.
Which of the following are the most important for the engineer to consider as part of the planning process? (Select two).
- A . Key escrow
- B . TPM presence
- C . Digital signatures
- D . Data tokenization
- E . Public key management
- F . Certificate authority linking
AB
Explanation:
Key escrow is a method of storing encryption keys in a secure location, such as a trusted third party or a hardware security module (HSM). Key escrow is important for FDE because it allows the recovery of encrypted data in case of lost or forgotten passwords, device theft, or hardware failure. Key escrow also enables authorized access to encrypted data for legal or forensic purposes.
TPM presence is a feature of some laptops that have a dedicated chip for storing encryption keys and other security information. TPM presence is important for FDE because it enhances the security and performance of encryption by generating and protecting the keys within the chip, rather than relying on software or external devices. TPM presence also enables features such as secure boot, remote attestation, and device authentication.
Which of the following factors are the most important to address when formulating a training curriculum plan for a security awareness program? (Select two).
- A . Channels by which the organization communicates with customers
- B . The reporting mechanisms for ethics violations
- C . Threat vectors based on the industry in which the organization operates
- D . Secure software development training for all personnel
- E . Cadence and duration of training events
- F . Retraining requirements for individuals who fail phishing simulations
CE
Explanation:
A training curriculum plan for a security awareness program should address the following factors: The threat vectors based on the industry in which the organization operates. This will help the employees to understand the specific risks and challenges that their organization faces, and how to protect themselves and the organization from cyberattacks. For example, a healthcare organization may face different threat vectors than a financial organization, such as ransomware, data breaches, or medical device hacking1.
The cadence and duration of training events. This will help the employees to retain the information
and skills they learn, and to keep up with the changing security landscape. The training events should be frequent enough to reinforce the key concepts and behaviors, but not too long or too short to lose the attention or interest of the employees. For example, a security awareness program may include monthly newsletters, quarterly webinars, annual workshops, or periodic quizzes2.
Reference: CompTIA Security+ Study Guide: Exam SY0-701, 9th Edition, Chapter 2, page 34; CompTIA
Security+ Certification Kit: Exam SY0-701, 7th Edition, Chapter 2, page 55.
Which of the following alert types is the most likely to be ignored over time?
- A . True positive
- B . True negative
- C . False positive
- D . False negative
C
Explanation:
A false positive is an alert that incorrectly identifies benign activity as malicious. Over time, if an alerting system generates too many false positives, security teams are likely to ignore these alerts, resulting in "alert fatigue." This increases the risk of missing genuine threats. True positives and true negatives are accurate and should be acted upon.
False negatives are more dangerous because they fail to identify real threats, but they are not "ignored" since they do not trigger alerts.
