Practice Free SOA-C02 Exam Online Questions
A company is using AWS to deploy a critical application on a fleet of Amazon EC2 instances The company is rewriting the application because the application failed a security review The application will take 12 months to rewrite While this rewrite happens, the company needs to rotate IAM access keys that the application uses.
A SysOps administrator must implement an automated solution that finds and rotates IAM access Keys that are at least 30 days old. The solution must then continue to rotate the IAM access Keys every 30 days.
Which solution will meet this requirement with the MOST operational efficiency?
- A . Use an AWS Config rule to identify IAM access Keys that are at least 30 days old. Configure AWS Config to invoKe an AWS Systems Manager Automation runbook to rotate the identified IAM access keys.
- B . Use AWS Trusted Advisor to identify IAM access Keys that are at least 30 days old. Configure Trusted Advisor to invoke an AWS Systems Manager Automation runbook to rotate the identified IAM access keys
- C . Create a script that checks the age of IAM access Keys and rotates them if they are at least 30 days old. Launch an EC2 instance. Schedule the script to run as a cron expression on the EC2 instance every day.
- D . Create an AWS Lambda function that checks the age of IAM access keys and rotates them if they are at least 30 days old Use an Amazon EventBridge rule to invoke the Lambda function every time a new IAM access key is created.
D
Explanation:
Lambda Function to Rotate IAM Access Keys:
A Lambda function can be used to automate the rotation of IAM access keys based on their age.
Steps:
Write a Lambda function that checks the age of IAM access keys.
The function should rotate keys that are at least 30 days old.
Deploy the Lambda function.
Amazon EventBridge Rule:
EventBridge can trigger the Lambda function periodically and when a new key is created.
Steps:
Create an EventBridge rule that triggers the Lambda function on a schedule (e.g., daily) and on IAM key creation events.
Reference: Rotating Access Keys for IAM Users, Amazon EventBridge
A SysOps administrator has set up a new Amazon EC2 instance as a web server in a public subnet.
The instance uses HTTP port 80 and HTTPS port 443.
The SysOps administrator has confirmed internet connectivity by downloading operating system updates and software from public repositories. However, the SysOps administrator cannot access the instance from a web browser on the internet.
Which combination of steps should the SysOps administrator take to troubleshoot this issue? (Select THREE.)
- A . Ensure that the inbound rules of the instance’s security group allow traffic on ports 80 and 443.
- B . Ensure that the outbound rules of the instance’s security group allow traffic on ports 80 and 443.
- C . Ensure that ephemeral ports 1024-65535 are allowed in the inbound rules of the network ACL that is associated with the instance’s subnet.
- D . Ensure that ephemeral ports 1024-65535 are allowed in the outbound rules of the network ACL that is associated with the instance’s subnet.
- E . Ensure that the filtering rules for any firewalls that are running on the instance allow inbound traffic on ports 80 and 443.
- F . Ensure that AWS WAF is turned on for the instance and is blocking web traffic.
A, D, E
Explanation:
When troubleshooting inability to access an EC2 instance from the internet, you should:
A: Verify that the security group rules allow inbound HTTP and HTTPS traffic on ports 80 and 443. Security groups act as a virtual firewall to control the traffic to instances.
D: Check that outbound rules in the network ACL allow traffic for ephemeral ports 1024-65535. This is crucial for return traffic from web requests, which typically use these higher port numbers for responses.
E: Confirm that any software-based firewalls on the instance (such as Windows Firewall or iptables in Linux) are configured to allow inbound traffic on HTTP and HTTPS. These steps will ensure that the web server is correctly configured to receive and respond to web traffic from the internet. AWS provides guidelines on these configurations in their documentation on security groups EC2 Security Groups and network ACLs Network ACLs.
A company wants to track its expenditures for Amazon EC2 and Amazon RDS within AWS. The company decides to implement more rigorous tagging requirements for resources in its AWS accounts. A SysOps administrator needs to identify all noncompliant resources.
What is the MOST operationally efficient solution that meets these requirements?
- A . Create a rule in Amazon EventBridge (Amazon CloudWatch Events) that invokes a custom AWS Lambda function that will evaluate all created or updated resources for the specified tags.
- B . Create a rule in AWS Config that invokes a custom AWS Lambda function that will evaluate all resources for the specified tags.
- C . Create a rule in AWS Config with the required-tags managed rule to evaluate all resources for the specified tags.
- D . Create a rule in Amazon EventBridge (Amazon CloudWatch Events) with a managed rule to evaluate all created or updated resources for the specified tags.
C
Explanation:
To efficiently monitor and identify noncompliant resources in terms of tagging within AWS, using
AWS Config with a managed rule for required tagging is most appropriate:
AWS Config Setup: Configure AWS Config to monitor and record configurations of AWS resources within your environment.
Managed Rule for Required Tags: Utilize the "required-tags" managed rule in AWS Config, which checks whether your resources have the specific tags you define as mandatory. This rule can be customized to specify which tags are required and can automatically evaluate all existing and new resources in your environment.
Compliance Reporting: AWS Config provides detailed compliance reporting that helps you identify resources that do not meet the tagging requirements, facilitating easy remediation.
This approach leverages AWS Config’s capabilities for continuous monitoring and evaluation without needing to write custom code or manage additional services, providing an operationally efficient solution for compliance management.
A company has a secure website running on Amazon EC2 instances behind an Application Load Balancer (ALB). An SSL certificate from AWS Certificate Manager (ACM) is used on the ALB. Users with legacy web browsers are experiencing issues with the website.
How should the SysOps administrator resolve these issues in the MOST operationally efficient manner?
- A . Create a new SSL certificate in ACM and install the new certificate on the ALB to support legacy web browsers.
- B . Create a second ALB and install a custom SSL certificate with a different domain name on the second ALB to support legacy web browsers.
- C . Remove the ALB from the configuration and install a custom SSL certificate on each web server.
- D . Update the SSL negotiation configuration of the ALB with a security policy that contains ciphers for legacy web browsers.
D
Explanation:
The issues experienced by users with legacy browsers typically stem from the SSL/TLS ciphers that are supported or enforced by the ALB. Modern security policies may exclude older ciphers that are necessary for compatibility with older browsers. Here’s how to resolve it:
Access the ALB Settings: Go to the AWS Management Console, navigate to the ALB settings, and locate the SSL negotiation configurations.
Modify Security Policy: Update the SSL/TLS security policy on the ALB to include ciphers that are compatible with legacy browsers. AWS provides predefined security policies, and some of these policies are designed to support older ciphers while still maintaining a level of security that complies with general best practices.
Apply Changes: Once the security policy is updated, the ALB will start using this new configuration, which should resolve compatibility issues with legacy browsers without needing to replace the SSL certificate or alter the infrastructure.
This solution maintains the operational efficiency of the setup and avoids the need for additional resources like a second ALB or new certificates.
A company has attached the following policy to an IAM user:
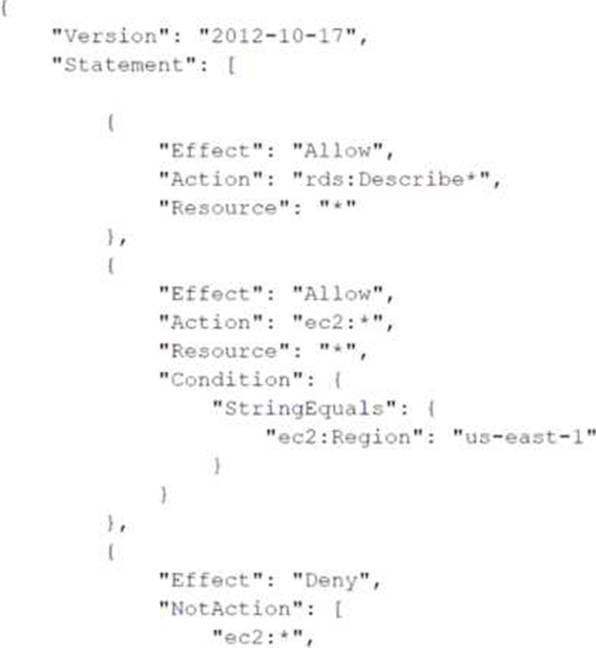
Which of the following actions are allowed for the IAM user?
- A . Amazon RDS DescribeDBInstances action in the us-east-1 Region
- B . Amazon S3 Putobject operation in a bucket named testbucket
- C . Amazon EC2 Describe Instances action in the us-east-1 Region
- D . Amazon EC2 AttachNetworkinterf ace action in the eu-west-1 Region
A
Explanation:
Based on the attached policy, the following actions are allowed for the IAM user:
Allow Amazon RDS DescribeDBInstances Action:
The policy allows rds:Describe* actions on all resources without any condition, so the user can describe RDS instances in any region.
Example action:
rds:DescribeDBInstances
Reference: Amazon RDS IAM Policies
Allow Amazon EC2 Actions in us-east-1 with Condition:
The policy allows ec2:* actions in the us-east-1 region based on the condition StringEquals for ec2:Region.
Example action:
ec2:DescribeInstances (only in us-east-1)
Reference: Amazon EC2 IAM Policies
Deny All Other EC2 Actions Globally:
The policy explicitly denies all actions that are not ec2:*, which means it blocks any other EC2 actions that don’t match the allow rule above.
Reference: IAM JSON Policy Elements: NotAction
Given these details, the only valid action among the options is:
A company recently acquired another corporation and all of that corporation’s AWS accounts. A financial analyst needs the cost data from these accounts. A SysOps administrator uses Cost Explorer to generate cost and usage reports. The SysOps administrator notices that "No Tagkey" represents 20% of the monthly cost.
What should the SysOps administrator do to tag the "No Tagkey" resources?
- A . Add the accounts to AWS Organizations. Use a service control policy (SCP) to tag all the untagged resources.
- B . Use an AWS Config rule to find the untagged resources. Set the remediation action to terminate the resources.
- C . Use Cost Explorer to find and tag all the untagged resources.
- D . Use Tag Editor to find and taq all the untaqqed resources.
D
Explanation:
"You can add tags to resources when you create the resource. You can use the resource’s service console or API to add, change, or remove those tags one resource at a time. To add tags to―or edit or delete tags of―multiple resources at once, use Tag Editor. With Tag Editor, you search for the resources that you want to tag, and then manage tags for the resources in your search results." https://docs.aws.amazon.com/ARG/latest/userguide/tag-editor.html
A company has an application that customers use to search for records on a website. The application’s data is stored in an Amazon Aurora DB cluster. The application’s usage varies by season and by day of the week.
The website’s popularity is increasing, and the website is experiencing slower performance because of increased load on the DB cluster during periods of peak activity. The application logs show that the performance issues occur when users are searching for information. The same search is rarely performed multiple times.
A SysOps administrator must improve the performance of the platform by using a solution that maximizes resource efficiency.
Which solution will meet these requirements?
- A . Deploy an Amazon ElastiCache for Redis cluster in front of the DB cluster. Modify the application to check the cache before the application issues new queries to the database. Add the results of any queries to the cache.
- B . Deploy an Aurora Replica for the DB cluster. Modify the application to use the reader endpoint for
search operations. Use Aurora Auto Scaling to scale the number of replicas based on load. Most Voted - C . Use Provisioned IOPS on the storage volumes that support the DB cluster to improve performance sufficiently to support the peak load on the application.
- D . Increase the instance size in the DB cluster to a size that is sufficient to support the peak load on the application. Use Aurora Auto Scaling to scale the instance size based on load.
A
Explanation:
Step-by-Step
Understand the Problem:
The application experiences slower performance during peak activity due to increased load on the Amazon Aurora DB cluster.
Performance issues occur primarily during search operations.
The goal is to improve performance and maximize resource efficiency.
Analyze the Requirements:
The solution should improve the performance of the platform.
It should maximize resource efficiency, which implies cost-effective and scalable options.
Evaluate the Options:
Option A: Deploy an Amazon ElastiCache for Redis cluster.
ElastiCache for Redis is a managed in-memory caching service that can significantly reduce the load on the database by caching frequently accessed data.
By modifying the application to check the cache before querying the database, repeated searches for the same information will be served from the cache, reducing the number of database reads.
This is efficient and cost-effective as it reduces database load and improves response times.
Option B: Deploy an Aurora Replica and use Auto Scaling.
Adding Aurora Replicas can help distribute read traffic and improve performance.
Aurora Auto Scaling can adjust the number of replicas based on the load.
However, this option may not be as efficient in terms of resource usage compared to caching because it still involves querying the database.
Option C: Use Provisioned IOPS.
Provisioned IOPS can improve performance by providing fast and consistent I/O.
This option focuses on improving the underlying storage performance but doesn’t address the inefficiency of handling repeated searches directly.
Option D: Increase the instance size and use Auto Scaling.
Increasing the instance size can provide more resources to handle peak loads.
Aurora Auto Scaling can adjust instance sizes based on the load.
This option can be costly and may not be as efficient as caching in handling repeated searches.
Select the Best Solution:
Option A is the best solution because it leverages caching to reduce the load on the database, which directly addresses the issue of repeated searches causing performance problems. Caching is generally more resource-efficient and cost-effective compared to scaling database instances or storage.
Reference: Amazon ElastiCache for Redis Documentation
Amazon Aurora Documentation
AWS Auto Scaling
Using ElastiCache for Redis aligns with best practices for improving application performance by offloading repetitive read queries from the database, leading to faster response times and more efficient resource usage.
A company deploys a new application on three Amazon EC2 instances across three Availability Zones The company uses a Network Load Balancer (NLB) to route traffic lo the EC2 instances. A SysOps administrator must implement a solution so that the EC2 instances allow traffic from only the NLB.
What should the SysOps administrator do to meet these requirements with the LEAST operational overhead?
- A . Configure the security group that is associated with the EC2 instances to allow traffic from only the security group that is associated with the NLB.
- B . Configure the security group that is associated with the EC2 instances to allow traffic from only the elastic network interfaces that are associated with the NLB.
- C . Create a network ACL. Associate the network ACL with the application subnets. Configure the network ACL to allow inbound traffic from only the CIDR ranges of the NLB.
- D . Use a third-party firewall solution that is installed on a separate EC2 instance. Configure a firewall rule that allows traffic to the application’s EC2 instances from only the subnets where the NLB is deployed
A
Explanation:
Configuring Security Groups:
Security groups act as virtual firewalls for your instances to control inbound and outbound traffic.
Steps:
Go to the AWS Management Console.
Navigate to EC2.
Select "Security Groups" from the left-hand menu.
Find and select the security group associated with your EC2 instances.
Choose the "Inbound rules" tab and click "Edit inbound rules."
Add a rule to allow traffic from the security group associated with the NLB. Type: Custom TCP (or the specific port your application uses) Source: Select "Custom" and enter the ID of the NLB’s security group.
This setup ensures that the EC2 instances accept traffic only from the NLB, enhancing security with minimal operational overhead.
Reference: AWS Security Groups
A company asks a SysOps administrator to ensure that AWS CloudTrail files are not tampered with after they are created. Currently, the company uses AWS Identity and Access Management (IAM) to restrict access to specific trails. The company’s security team needs the ability to trace the integrity of each file.
What is the MOST operationally efficient solution that meets these requirements?
- A . Create an Amazon EventBridge (Amazon CloudWatch Events) rule that invokes an AWS Lambda function when a new file is delivered. Configure the Lambda function to compute an MD5 hash check on the file and store the result in an Amazon DynamoDB table. The security team can use the values that are stored in DynamoDB to verify the integrity of the delivered files.
- B . Create an AWS Lambda function that is invoked each time a new file is delivered to the CloudTrail bucket. Configure the Lambda function to compute an MD5 hash check on the file and store the result as a tag in an Amazon S3 object. The security team can use the information in the tag to verify the integrity of the delivered files.
- C . Enable the CloudTrail file integrity feature on an Amazon S3 bucket. Create an IAM policy that grants the security team access to the file integrity logs that are stored in the S3 bucket.
- D . Enable the CloudTrail file integrity feature on the trail. The security team can use the digest file that is created by CloudTrail to verify the integrity of the delivered files.
D
Explanation:
https://docs.aws.amazon.com/awscloudtrail/latest/userguide/cloudtrail-log-file-validation-intro.html
"When you enable log file integrity validation, CloudTrail creates a hash for every log file that it delivers. Every hour, CloudTrail also creates and delivers a file that references the log files for the last hour and contains a hash of each. This file is called a digest file. Validated log files are invaluable in security and forensic investigations"
A company wants to store sensitive financial data within Amazon S3 buckets. The company has a corporate policy that does not allow public read or write access to the buckets. A SysOps administrator must create a solution to automatically remove S3 permissions that allow public read or write access.
Which AWS service should the SysOps administrator use to meet these requirements in the MOST operationally efficient manner?
- A . AWSConfig
- B . AWS Security Hub
- C . AWS Trusted Advisor
- D . Amazon Inspector
A
Explanation:
AWS Config is the best service to automatically manage and remediate S3 bucket permissions that violate corporate policies against public access. AWS Config continuously monitors and records AWS resource configurations and allows you to create rules that trigger automatic responses when public access configurations are detected. This approach is highly operationally efficient as it automates compliance and enforcement of security policies without manual intervention. Option A is correct. AWS Config can be used to assess, audit, and evaluate the configurations of AWS resources, including S3 buckets. Reference AWS Config.
