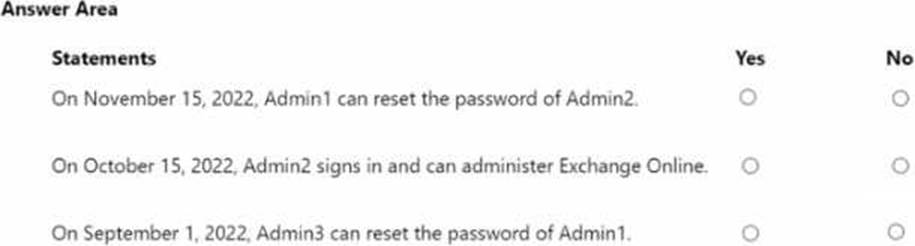
Practice Free SC-300 Exam Online Questions
HOTSPOT
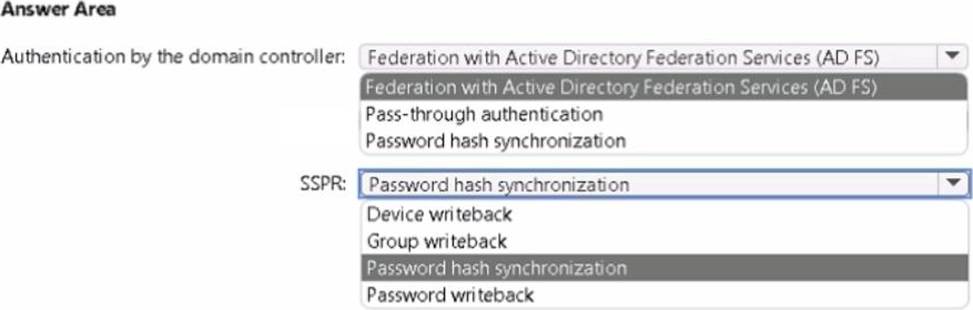
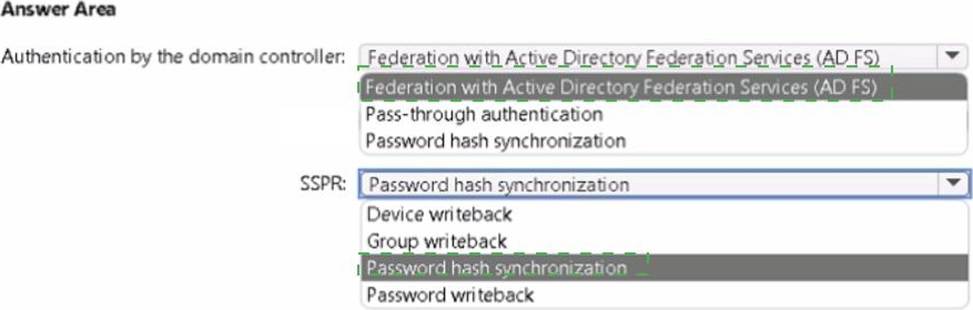
Your on-premises network contains an Active Directory domain that uses Azure AD Connect to sync with an Azure AD tenant.
You need to configure Azure AD Connect to meet the following requirements:
• User sign-ins to Azure AD must be authenticated by an Active Directory domain controller.
• Active Directory domain users must be able to use Azure AD self-service password reset (SSPR).
What should you use for each requirement? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You have a Microsoft 365 tenant.
All users must use the Microsoft Authenticator app for multi-factor authentication (MFA) when accessing Microsoft 365 services.
Some users report that they received an MFA prompt on their Microsoft Authenticator app without initiating a sign-in request.
You need to block the users automatically when they report an MFA request that they did not Initiate.
Solution: From the Azure portal, you configure the Block/unblock users settings for multi-factor authentication (MFA).
Does this meet the goal?
- A . Yes
- B . No
B
Explanation:
You need to configure the fraud alert settings.
Reference: https://docs.microsoft.com/en-us/azure/active-directory/authentication/howto-mfa-mfasettings
You configure a new Microsoft 36S tenant to use a default domain name of contosso.com.
You need to ensure that you can control access to Microsoft 365 resource-, by using conditional access policy.
What should you do first?
- A . Disable the User consent settings.
- B . Disable Security defaults.
- C . Configure a multi-factor authentication (Ml A) registration policy1.
- D . Configure password protection for Windows Server Active Directory.
You have an Azure subscription.
You need to use Microsoft Entra Permissions Management to automatically monitor permissions and create and implement right-size roles. The solution must follow the principle of least privilege.
Which role should you assign to the service principal of Permissions Management?
- A . Reader
- B . Contributor
- C . Owner
- D . User Access Administrator
Your company purchases 2 new Microsoft 365 ES subscription and an app named App.
You need to create a Microsoft Defender for Cloud Apps access policy for App1.
What should you do you first? (Choose Correct Answer based on Microsoft Identity and Access Administrator at microsoft.com)
- A . Configure a Token configuration for App1.
- B . Add an API permission for App.
- C . Configure a Conditional Access policy to use app-enforced restrictions.
- D . Configure a Conditional Access policy to use Conditional Access App Control.
C
Explanation:
https://learn.microsoft.com/en-us/defender-cloud-apps/access-policy-aad
To create a Microsoft Defender for Cloud Apps access policy for App1, you should configure a Conditional Access policy to use app-enforced restrictions. This will allow you to control access to your cloud apps based on conditions such as user, device, location, and app state. You can also use app-enforced restrictions to control access to your cloud apps based on the state of the app, such as whether it’s running on a managed or unmanaged device.
You have a Microsoft 365 tenant.
All users must use the Microsoft Authenticator app for multi-factor authentication (MFA) when accessing Microsoft 365 services.
Some users report that they received an MFA prompt on their Microsoft Authenticator app without initiating a sign-in request.
You need to block the users automatically when they report an MFA request that they did not Initiate.
Solution: From the Azure portal, you configure the Fraud alert settings for multi-factor authentication (MFA).
Does this meet the goal?
- A . Yes
- B . No
A
Explanation:
The fraud alert feature lets users report fraudulent attempts to access their resources. When an unknown and suspicious MFA prompt is received, users can report the fraud attempt using the Microsoft Authenticator app or through their phone.
The following fraud alert configuration options are available:
Automatically block users who report fraud.
Code to report fraud during initial greeting.
Reference: https://docs.microsoft.com/en-us/azure/active-directory/authentication/howto-mfa-mfasettings
HOTSPOT
You have an Azure Active Directory (Azure AD) tenant named contoso.com that contains a user named User1.
User1 has the devices shown in the following table.
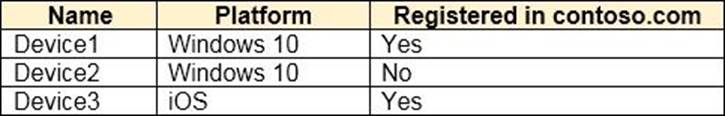
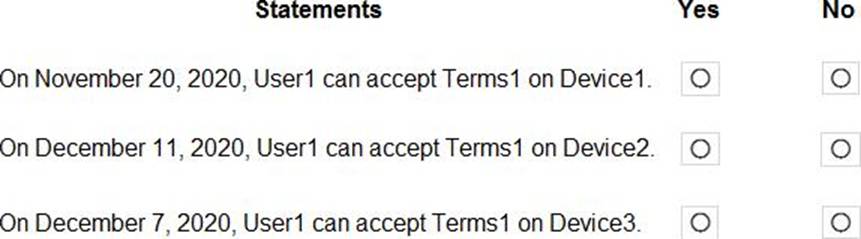
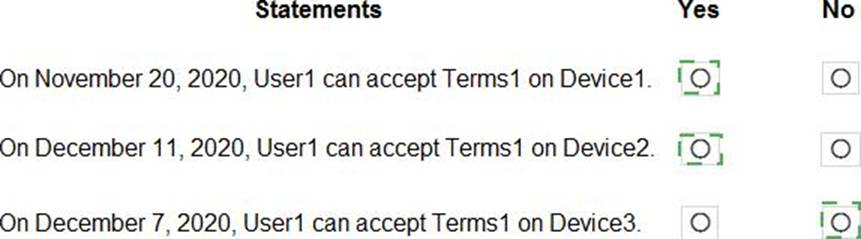
On November 5, 2020, you create and enforce terms of use in contoso.com that has the following settings:
✑ Name: Terms1
✑ Display name: Contoso terms of use
✑ Require users to expand the terms of use: On
✑ Require users to consent on every device: On
✑ Expire consents: On
✑ Expire starting on: December 10, 2020
✑ Frequency: Monthly
On November 15, 2020, User1 accepts Terms1 on Device3.
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
HOTSPOT
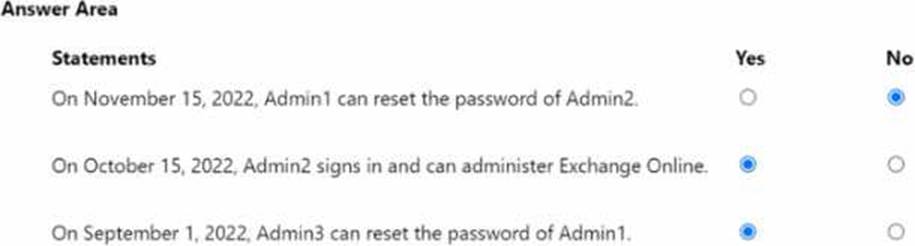
You have a Microsoft Entra tenant that contains the users shown in the following table.
You add the following assignment for the User Administrator role:
• Scope type: Directory
• Selected members: Group1
• Assignment type: Active
• Assignments starts August 15. 2022
• Assignment ends: December 15, 2022
You add the following assignment for the Exchange Administrator role:
• Scope type: Directory
• Selected members: Group2
• Assignment type: Eligible
• Assignments starts: October 15, 2022
• Assignment ends: January 15. 2023
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
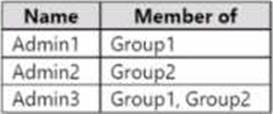
You have an Azure subscription that contains the users shown in the following table.
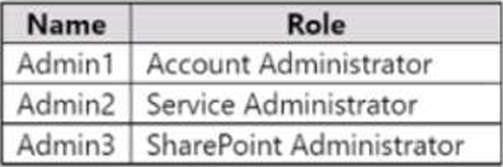
You need to implement Azure AD Privileged Identity Management (PIM).
Which users can use PIM to activate their role permissions?
- A . Admin! only
- B . Admin2 only
- C . Admin3 only
- D . Admin1 and Admin2 only
- E . Admin2 and Admin3 only
- F . Admin1, Admin2, and Admin3
HOTSPOT
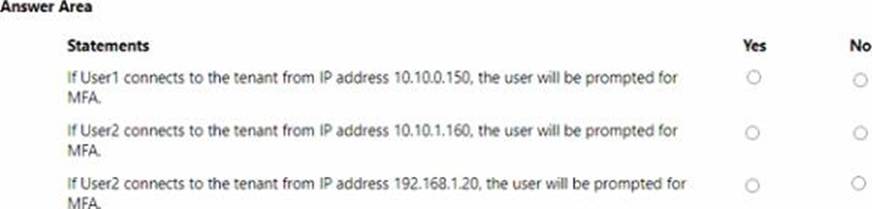
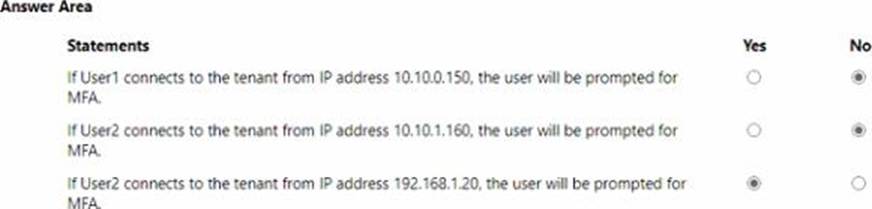
You have an Azure AD tenant that contains the users shown in the following table.
![]()
You have the locations shown in the following table.
![]()
The tenant contains a named location that Das the following configurations:
• Name: location1
• Mark as trusted location: Enabled
• IPv4 range: 10.10.0.0/16
MFA has a trusted iPad dress range of 193.17.17.0/24.
You have a Conditional Access policy that has the following settings:
• Name: CAPolicy1
• Assignments
o Users or workload identities: Group 1
o Cloud apps or actions: All cloud apps
* Conditions
* Locations All trusted locations
• Access controls
o Gant
• Grant access: Require multi-factor authentication
© Session: 0 controls selected
• Enable policy: On
For each of the following statements select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.