Practice Free SC-100 Exam Online Questions
A customer uses Azure to develop a mobile app that will be consumed by external users as shown in the following exhibit.
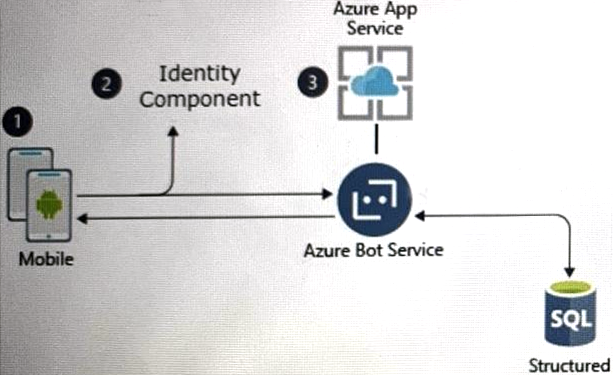
You need to design an identity strategy for the app.
The solution must meet the following requirements:
• Enable the usage of external IDs such as Google, Facebook, and Microsoft accounts.
• Be managed separately from the identity store of the customer.
• Support fully customizable branding for each app.
Which service should you recommend to complete the design?
- A . Azure Active Directory (Azure AD) B2C
- B . Azure Active Directory (Azure AD) B2B
- C . Azure AD Connect
- D . Azure Active Directory Domain Services (Azure AD DS)
A
Explanation:
https://docs.microsoft.com/en-us/azure/active-directory-b2c/identity-provider-facebook?pivots=b2c-user-flow
https://docs.microsoft.com/en-us/azure/active-directory-b2c/customize-ui-with-html?pivots=b2c-user-flow
You have an Azure subscription that has Microsoft Defender for Cloud enabled.
You need to enforce ISO 27001:2013 standards for new resources deployed to the subscription. The solution must ensure that noncompliant resources are automatically detected.
What should you use?
- A . Azure Blueprints
- B . the regulatory compliance dashboard in Defender for Cloud
- C . Azure role-based access control (Azure RBAC)
- D . Azure Policy
HOTSPOT
You have a Microsoft 365 tenant.
You need to recommend a Microsoft 365 Defender solution to enhance security for the tenant.
The solution must meet the following requirements:
• Identify users that are downloading an unusually high number of files from Microsoft SharePoint Online sites and are possibly involved in a data exfiltration attempt.
• Block Microsoft Teams messages that contain potentially malicious content by using zero-hour auto purge (ZAP).
What should you recommend for each requirement? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
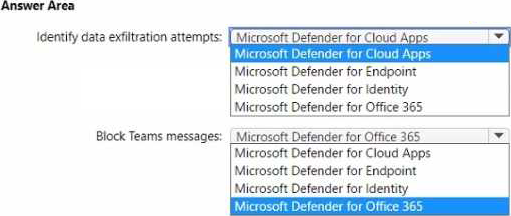
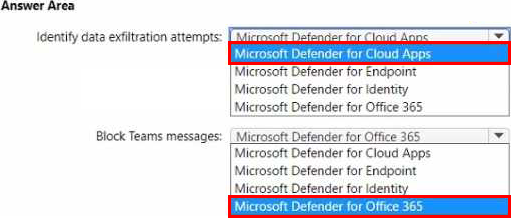
Your company has a Microsoft 365 subscription and uses Microsoft Defender for Identity. You are informed about incidents that relate to compromised identities.
You need to recommend a solution to expose several accounts for attackers to exploit. When the attackers attempt to exploit the accounts, an alert must be triggered.
Which Defender for Identity feature should you include in the recommendation?
- A . standalone sensors
- B . honeytoken entity tags
- C . sensitivity labels
- D . custom user tags
B
Explanation:
https://docs.microsoft.com/en-us/advanced-threat-analytics/suspicious-activity-guide#honeytoken-activity
The Sensitive tag is used to identify high value assets.(user / devices / groups)Honeytoken entities are used as traps for malicious actors. Any authentication associated with these honeytoken entities triggers an alert. and Defender for Identity considers Exchange servers as high-value assets and automatically tags them as Sensitive
HOTSPOT
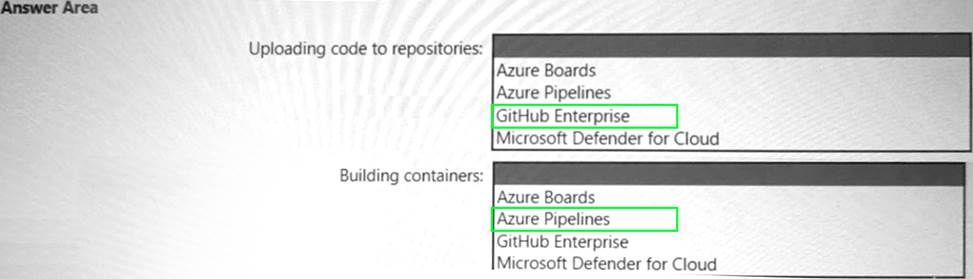
Your company has an Azure App Service plan that is used to deploy containerized web apps. You are designing a secure DevOps strategy for deploying the web apps to the App Service plan. You need to recommend a strategy to integrate code scanning tools into a secure software development lifecycle. The code must be scanned during the following two phases: Uploading the code to repositories Building containers
Where should you integrate code scanning for each phase? To answer, select the appropriate options in the answer area.
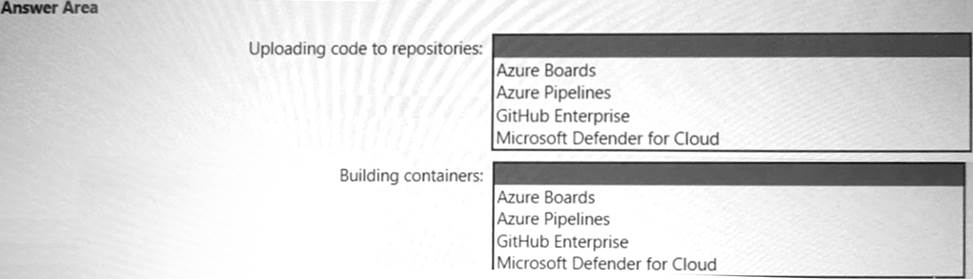
Explanation:
https://docs.github.com/en/enterprise-cloud@latest/get-started/learning-about-github/about-github-advanced-security
https://microsoft.github.io/code-with-engineering-playbook/automated-testing/tech-specific-samples/azdo-container-dev-test-release/
HOTSPOT
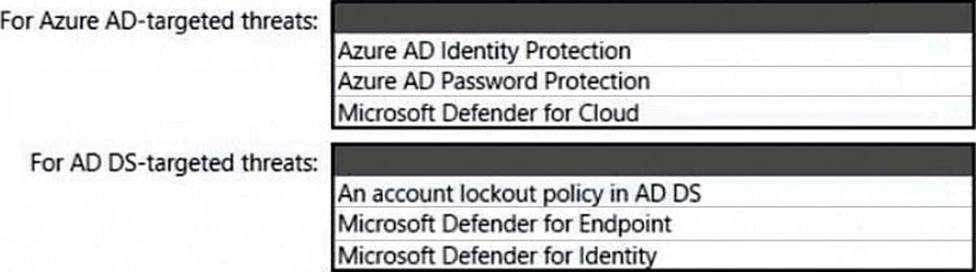
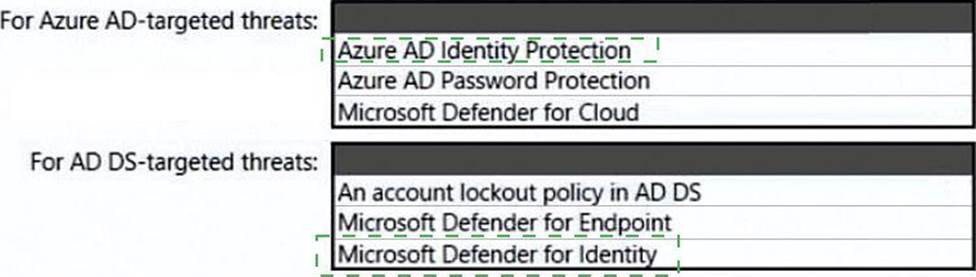
You need to recommend a strategy for securing the litware.com forest. The solution must meet the identity requirements.
What should you include in the recommendation? To answer, select the appropriate options in the answer area. NOTE; Each correct selection is worth one point.
Explanation:
