Practice Free SC-100 Exam Online Questions
You have a Microsoft 365 subscription that syncs with Active Directory Domain Services (AD DS). You need to define the recovery steps for a ransomware attack that encrypted data in the subscription The solution must follow Microsoft Security Best Practices.
What is the first step in the recovery plan?
- A . Disable Microsoft OneDnve sync and Exchange ActiveSync.
- B . Recover files to a cleaned computer or device.
- C . Contact law enforcement.
- D . From Microsoft Defender for Endpoint perform a security scan.
You receive a security alert in Microsoft Defender for Cloud as shown in the exhibit. (Click the Exhibit tab.)
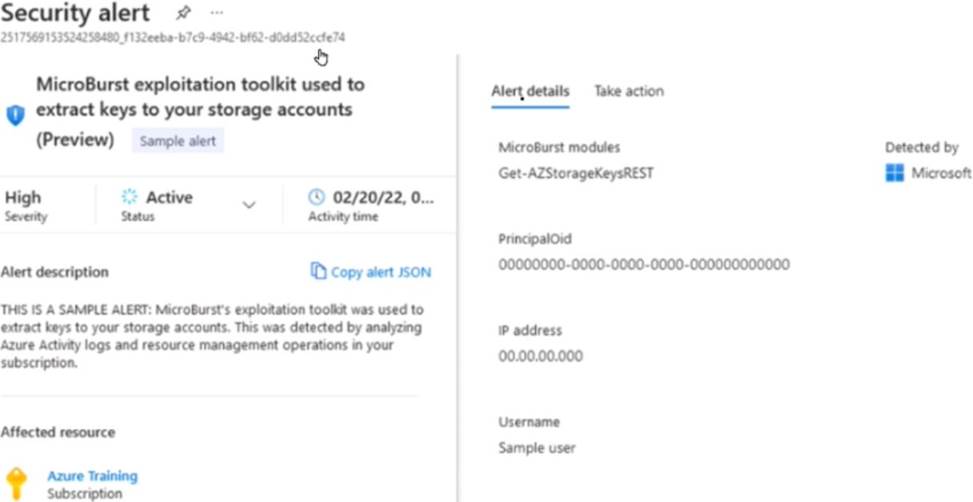
After remediating the threat which policy definition should you assign to prevent the threat from reoccurring?
- A . Storage account public access should be disallowed
- B . Azure Key Vault Managed HSM should have purge protection enabled
- C . Storage accounts should prevent shared key access
- D . Storage account keys should not be expired
A
Explanation:
https://docs.microsoft.com/en-us/azure/storage/blobs/anonymous-read-access-prevent
You need to recommend a solution to resolve the virtual machine issue.
What should you include in the recommendation? (Choose Two)
- A . Onboard the virtual machines to Microsoft Defender for Endpoint.
- B . Onboard the virtual machines to Azure Arc.
- C . Create a device compliance policy in Microsoft Endpoint Manager.
- D . Enable the Qualys scanner in Defender for Cloud.
A, D
Explanation:
https://docs.microsoft.com/en-us/microsoft-365/security/defender-endpoint/switch-to-mde-phase-3?view=o365-worldwide
Your company has an Azure subscription that has enhanced security enabled for Microsoft Defender for Cloud.
The company signs a contract with the United States government.
You need to review the current subscription for NIST 800-53 compliance.
What should you do first?
- A . From Defender for Cloud, review the secure score recommendations.
- B . From Microsoft Sentinel, configure the Microsoft Defender for Cloud data connector.
- C . From Defender for Cloud, review the Azure security baseline for audit report.
- D . From Defender for Cloud, add a regulatory compliance standard.
D
Explanation:
https://docs.microsoft.com/en-us/azure/defender-for-cloud/update-regulatory-compliance-packages#what-regulatory-compliance-standards-are-available-in-defender-for-cloud
Your on-premises network contains an e-commerce web app that was developed in Angular and
Nodejs. The web app uses a MongoDB database. You plan to migrate the web app to Azure. The solution architecture team proposes the following architecture as an Azure landing zone.
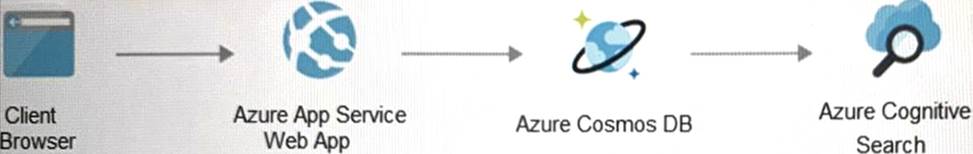
You need to provide recommendations to secure the connection between the web app and the database. The solution must follow the Zero Trust model.
Solution: You recommend creating private endpoints for the web app and the database layer.
Does this meet the goal?
- A . Yes
- B . No
A
Explanation:
When using Azure-provided PaaS services (e.g., Azure Storage, Azure Cosmos DB, or Azure Web App, use the PrivateLink connectivity option to ensure all data exchanges are over the private IP space and the traffic never leaves the Microsoft network.
https://docs.microsoft.com/en-us/azure/cosmos-db/how-to-configure-private-endpoints
You have a Microsoft 365 subscription and an Azure subscription. Microsoft 365 Defender and Microsoft Defender for Cloud are enabled.
The Azure subscription contains 50 virtual machines. Each virtual machine runs different applications on Windows Server 2019.
You need to recommend a solution to ensure that only authorized applications can run on the virtual machines. If an unauthorized application attempts to run or be installed, the application must be blocked automatically until an administrator authorizes the application.
Which security control should you recommend?
- A . Azure Active Directory (Azure AD) Conditional Access App Control policies
- B . OAuth app policies in Microsoft Defender for Cloud Apps
- C . app protection policies in Microsoft Endpoint Manager
- D . application control policies in Microsoft Defender for Endpoint
D
Explanation:
https://docs.microsoft.com/en-us/windows/security/threat-protection/windows-defender-application-control/select-types-of-rules-to-create#windows-defender-application-control-policy-rules
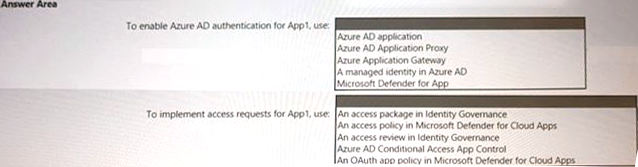
HOTSPOT
You are creating the security recommendations for an Azure App Service web app named App1.
App1 has the following specifications:
• Users will request access to App1 through the My Apps portal. A human resources manager will approve the requests.
• Users will authenticate by using Azure Active Directory (Azure AD) user accounts.
You need to recommend an access security architecture for App1.
What should you include in the recommendation? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
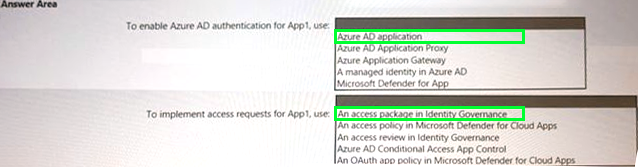
Explanation:
Box 1 is the Azure AD Application https://docs.microsoft.com/en-us/azure/active-directory/develop/quickstart-register-app
Box 2 is Access Package in Identity Governance
https://docs.microsoft.com/en-us/azure/active-directory/governance/entitlement-management-
access-package-create
A customer has a hybrid cloud infrastructure that contains a Microsoft 365 E5 subscription and an
Azure subscription.
All the on-premises servers in the perimeter network are prevented from connecting directly to the internet.
The customer recently recovered from a ransomware attack.
The customer plans to deploy Microsoft Sentinel.
You need to recommend configurations to meet the following requirements:
• Ensure that the security operations team can access the security logs and the operation logs.
• Ensure that the IT operations team can access only the operations logs, including the event logs of the servers in the perimeter network.
Which two configurations can you include in the recommendation? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point.
- A . Azure Active Directory (Azure AD) Conditional Access policies
- B . a custom collector that uses the Log Analytics agent
- C . resource-based role-based access control (RBAC)
- D . the Azure Monitor agent
C, D
Explanation:
https://docs.microsoft.com/en-us/azure/azure-monitor/agents/log-analytics-agent
You have an operational model based on the Microsoft Cloud Adoption framework for Azure.
You need to recommend a solution that focuses on cloud-centric control areas to protect resources such as endpoints, database, files, and storage accounts.
What should you include in the recommendation?
- A . security baselines in the Microsoft Cloud Security Benchmark
- B . modern access control
- C . business resilience
- D . network isolation
What strategy should be employed to enforce least privilege access when configuring Azure services?
- A . Use Azure Policy
- B . Enable Azure MultiFactor Authentication
- C . Implement Azure AD Privileged Identity Management
- D . Use Azure Service Health alerts
