Practice Free SC-100 Exam Online Questions
Your company has an office in Seattle.
The company has two Azure virtual machine scale sets hosted on different virtual networks.
The company plans to contract developers in India.
You need to recommend a solution provide the developers with the ability to connect to the virtual machines over SSL from the Azure portal.
The solution must meet the following requirements:
• Prevent exposing the public IP addresses of the virtual machines.
• Provide the ability to connect without using a VPN.
• Minimize costs.
Which two actions should you perform? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
- A . Deploy Azure Bastion to one virtual network.
- B . Deploy Azure Bastion to each virtual network.
- C . Enable just-in-time VM access on the virtual machines.
- D . Create a hub and spoke network by using virtual network peering.
- E . Create NAT rules and network rules in Azure Firewall.
AD
Explanation:
https://docs.microsoft.com/en-us/learn/modules/connect-vm-with-azure-bastion/2-what-is-azure-bastion
HOTSPOT
You have an Azure SQL database named DB1 that contains customer information.
A team of database administrators has full access to DB1.
To address customer inquiries, operators in the customer service department use a custom web app named App1 to view the customer information.
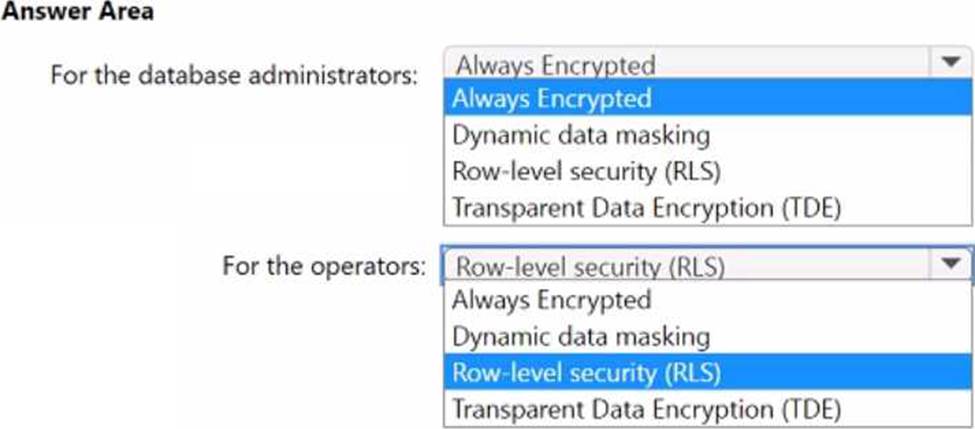
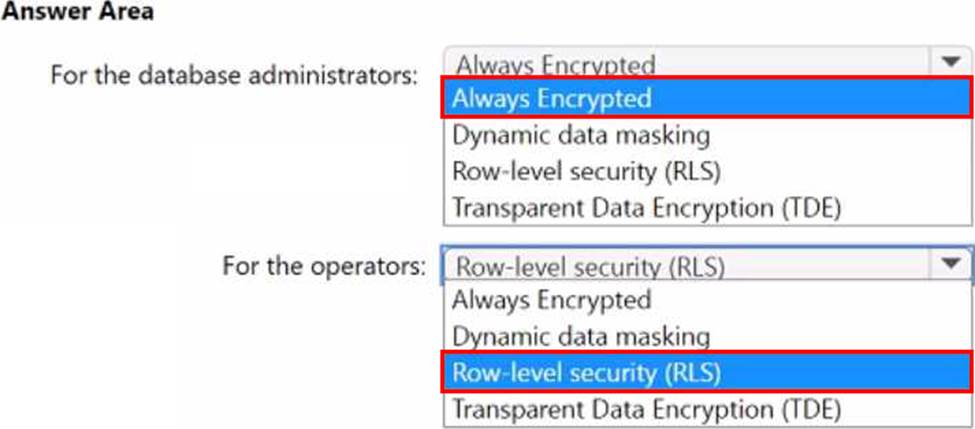
You need to design a security strategy for D81.
The solution must meet the following requirements:
• When the database administrators access DB1 by using SQL management tools, they must be prevented from viewing the content of the Credit Card attribute of each customer record.
• When the operators view customer records in App1, they must view only the last four digits of the Credit Card attribute.
What should you include in the design? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
Your on-premises network contains an e-commerce web app that was developed in Angular and Node.js. The web app uses a MongoDB database. You plan to migrate the web app to Azure. The
solution architecture team proposes the following architecture as an Azure landing zone.
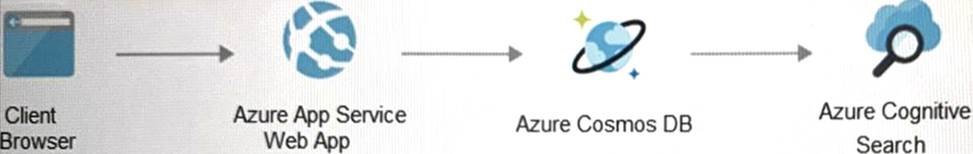
You need to provide recommendations to secure the connection between the web app and the database. The solution must follow the Zero Trust model.
Solution: You recommend implementing Azure Front Door with Azure Web Application Firewall (WAF).
Does this meet the goal?
- A . Yes
- B . No
B
Explanation:
https://www.varonis.com/blog/securing-access-azure-webapps
Your company has an on-premise network in Seattle and an Azure subscription. The on-premises network contains a Remote Desktop server.
The company contracts a third-party development firm from France to develop and deploy resources to the virtual machines hosted in the Azure subscription.
Currently, the firm establishes an RDP connection to the Remote Desktop server. From the Remote Desktop connection, the firm can access the virtual machines hosted in Azure by using custom administrative tools installed on the Remote Desktop server. All the traffic to the Remote Desktop server is captured by a firewall, and the firewall only allows specific connections from France to the server.
You need to recommend a modern security solution based on the Zero Trust model. The solution must minimize latency tor developers.
Which three actions should you recommend? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
- A . Configure network security groups (NSGs) to allow access from only specific logical groupings of IP address ranges.
- B . Implement Azure Firewall to restrict host pool outbound access.
- C . Configure Azure Active Directory (Azure AD) Conditional Access with multi-factor authentication (MFA) and named locations.
- D . Migrate from the Remote Desktop server to Azure Virtual Desktop.
- E . Deploy a Remote Desktop server to an Azure region located in France.
BCD
Explanation:
https://docs.microsoft.com/en-us/azure/firewall/protect-azure-virtual-desktop
Your company has a Microsoft 365 E5 subscription.
The Chief Compliance Officer plans to enhance privacy management in the working environment. You need to recommend a solution to enhance the privacy management.
The solution must meet the following requirements:
• Identify unused personal data and empower users to make smart data handling decisions.
• Provide users with notifications and guidance when a user sends personal data in Microsoft Teams.
• Provide users with recommendations to mitigate privacy risks.
What should you include in the recommendation?
- A . Microsoft Viva Insights
- B . Advanced eDiscovery
- C . Privacy Risk Management in Microsoft Priva
- D . communication compliance in insider risk management
C
Explanation:
Privacy Risk Management in Microsoft Priva gives you the capability to set up policies that identify privacy risks in your Microsoft 365 environment and enable easy remediation. Privacy Risk Management policies are meant to be internal guides and can help you: Detect overexposed personal data so that users can secure it.
Spot and limit transfers of personal data across departments or regional borders. Help users identify and reduce the amount of unused personal data that you store. https://www.microsoft.com/en-us/security/business/privacy/microsoft-priva-risk-management
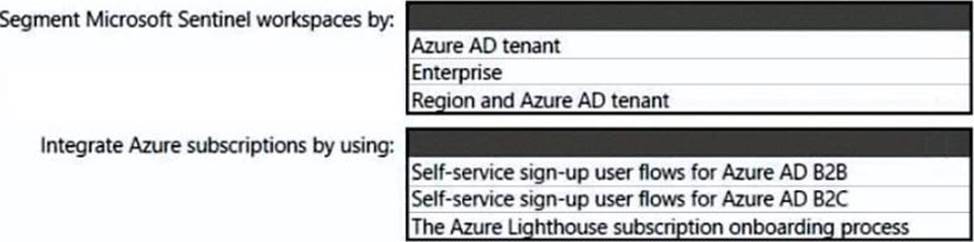
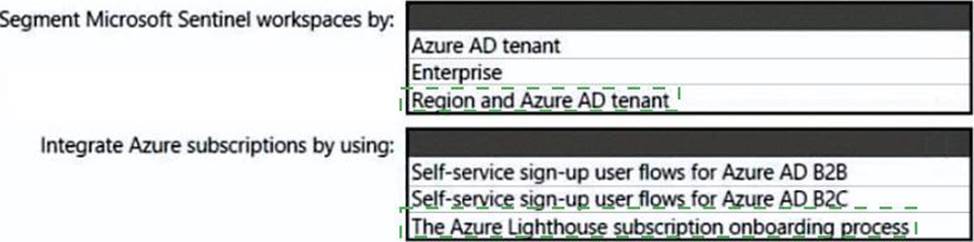
HOTSPOT
You need to recommend a SIEM and SOAR strategy that meets the hybrid requirements, the Microsoft Sentinel requirements, and the regulatory compliance requirements.
What should you recommend? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
Explanation:
Segment Microsoft Sentinel workspaces by: Region and Azure AD tenant Lighthouse subscription
HOTSPOT
You need to recommend a strategy for App Service web app connectivity. The solution must meet the landing zone requirements.
What should you recommend? To answer, select the appropriate options in the answer area. NOTE Each correct selection is worth one point.
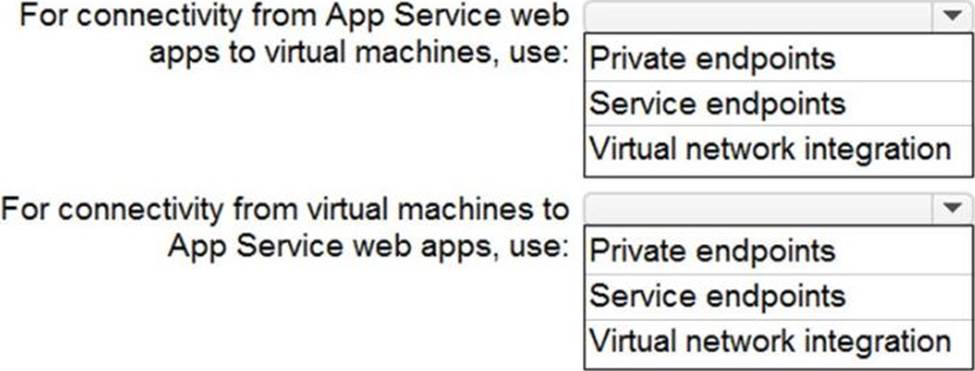
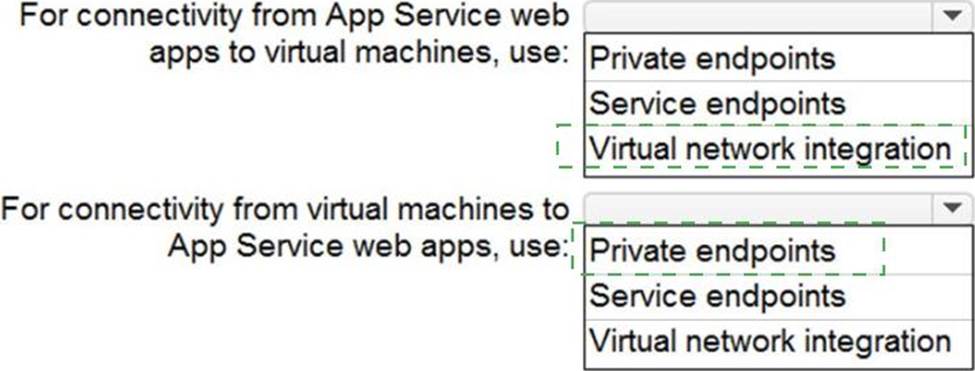
Explanation:
Box 1: Virtual Network Integration – correct
Virtual network integration gives your app access to resources in your virtual network, but it doesn’t grant inbound private access to your app from the virtual network.
Box 2: Private Endpoints. – correct
You can use Private Endpoint for your Azure Web App to allow clients located in your private network to securely access the app over Private Link.
You have a Microsoft 365 E5 subscription and an Azure subscription. You are designing a Microsoft Sentinel deployment.
You need to recommend a solution for the security operations team. The solution must include custom views and a dashboard for analyzing security events.
What should you recommend using in Microsoft Sentinel?
- A . playbooks
- B . workbooks
- C . notebooks
- D . threat intelligence
B
Explanation:
https://docs.microsoft.com/en-us/azure/azure-monitor/visualize/workbooks-overview
You use Azure Pipelines with Azure Repos to implement continuous integration and continuous deployment (O/CD) workflows for the deployment of applications to Azure. You need to recommend what to include in dynamic application security testing (DAST) based on the principles of the Microsoft Cloud Adoption Framework for Azure.
What should you recommend?
- A . unit testing
- B . penetration testing
- C . dependency testing
- D . threat modeling
HOTSPOT
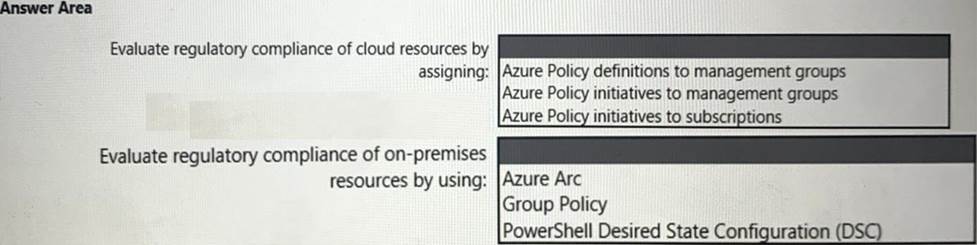
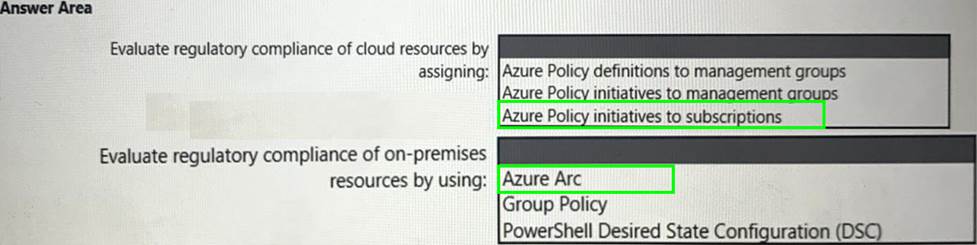
You need to recommend a solution to evaluate regulatory compliance across the entire managed environment. The solution must meet the regulatory compliance requirements and the business requirements.
What should you recommend? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.