Practice Free SC-100 Exam Online Questions
HOTSPOT
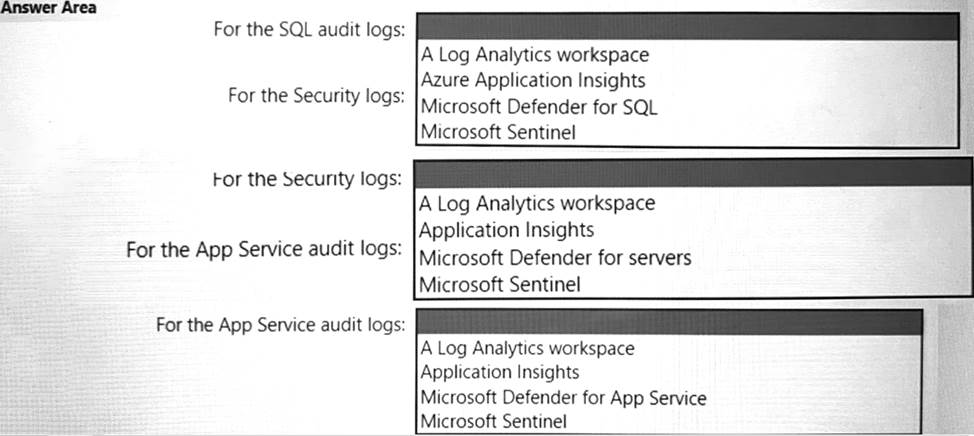
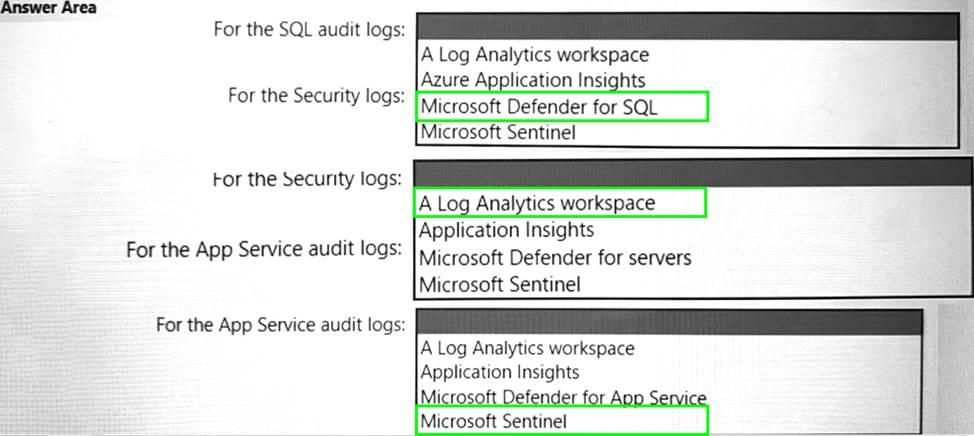
You are designing an auditing solution for Azure landing zones that will contain the following components:
• SQL audit logs for Azure SQL databases
• Windows Security logs from Azure virtual machines
• Azure App Service audit logs from App Service web apps
You need to recommend a centralized logging solution for the landing zones.
The solution must meet the following requirements:
• Log all privileged access.
• Retain logs for at least 365 days.
• Minimize costs.
What should you include in the recommendation? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
Your company finalizes the adoption of Azure and is implementing Microsoft Defender for Cloud.
You receive the following recommendations in Defender for Cloud
• Access to storage accounts with firewall and virtual network configurations should be restricted,
• Storage accounts should restrict network access using virtual network rules.
• Storage account should use a private link connection.
• Storage account public access should be disallowed.
You need to recommend a service to mitigate identified risks that relate to the recommendations.
What should you recommend?
- A . Azure Storage Analytics
- B . Azure Network Watcher
- C . Microsoft Sentinel
- D . Azure Policy
D
Explanation:
https://docs.microsoft.com/en-us/azure/defender-for-cloud/security-policy-concept
https://docs.microsoft.com/en-us/security/benchmark/azure/baselines/storage-security-baseline
HOTSPOT
You need to recommend a multi-tenant and hybrid security solution that meets to the business requirements and the hybrid requirements.
What should you recommend? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.


You are designing a security strategy for providing access to Azure App Service web apps through an Azure Front Door instance.
You need to recommend a solution to ensure that the web apps only allow access through the Front Door instance.
Solution: You recommend access restrictions to allow traffic from the backend IP address of the Front Door instance.
Does this meet the goal?
- A . Yes
- B . No
HOTSPOT
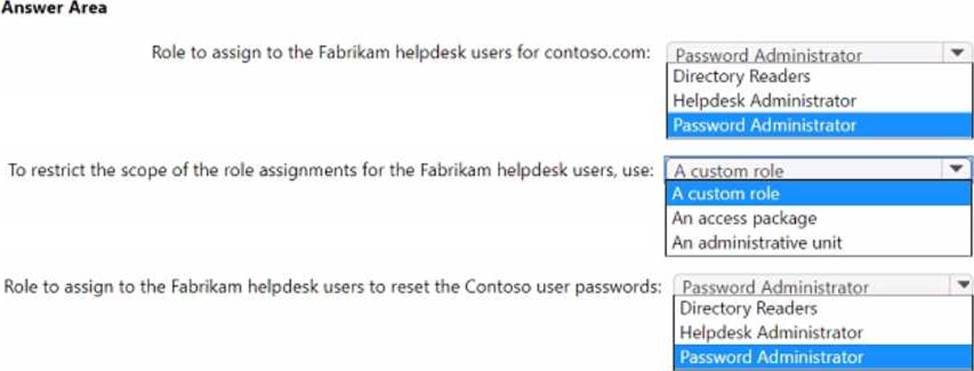
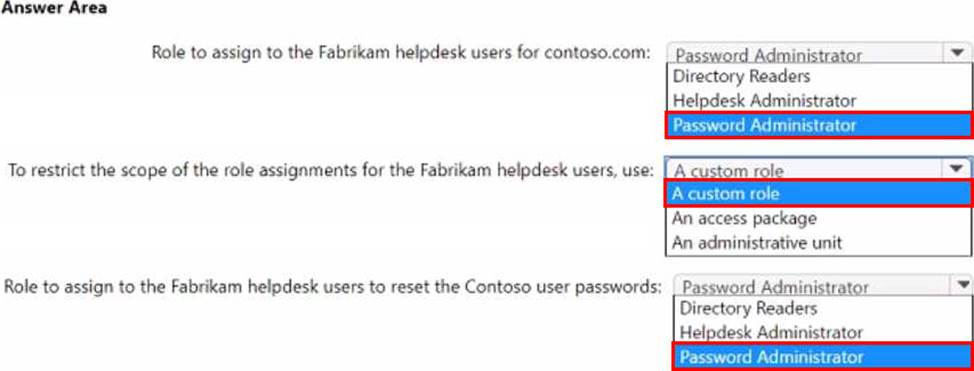
Your company, named Contoso. Ltd… has an Azure AD tenant namedcontoso.com. Contoso has a partner company named Fabrikam. Inc. that has an Azure AD tenant named fabrikam.com. You need to ensure that helpdesk users at Fabrikam can reset passwords for specific users at Contoso.
The solution must meet the following requirements:
• Follow the principle of least privilege.
• Minimize administrative effort.
What should you do? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You need to recommend a solution to scan the application code. The solution must meet the application development requirements.
What should you include in the recommendation?
- A . Azure Key Vault
- B . GitHub Advanced Security
- C . Application Insights in Azure Monitor
- D . Azure DevTest Labs
B
Explanation:
https://docs.microsoft.com/en-us/learn/modules/introduction-github-advanced-security/2-what-is-github-advanced-security
You design cloud-based software as a service (SaaS) solutions.
You need to recommend ransomware attacks. The solution must follow Microsoft Security Best Practices.
What should you recommend doing first?
- A . Implement data protection.
- B . Develop a privileged access strategy.
- C . Prepare a recovery plan.
- D . Develop a privileged identity strategy.
You have an Azure subscription that has Microsoft Defender for Cloud enabled.
You are evaluating the Azure Security Benchmark V3 report as shown in the following exhibit.
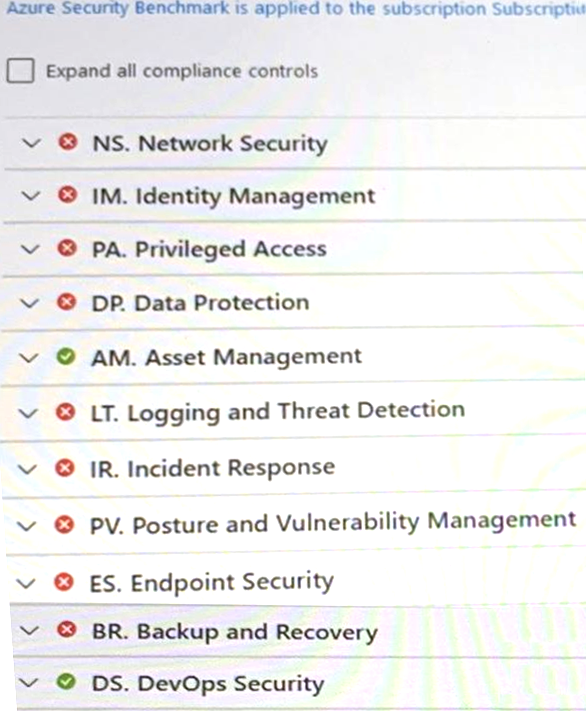
You need to verify whether Microsoft Defender for servers is installed on all the virtual machines that run Windows.
Which compliance control should you evaluate?
- A . Data Protection
- B . Incident Response
- C . Posture and Vulnerability Management
- D . Asset Management
- E . Endpoint Security
E
Explanation:
https://docs.microsoft.com/en-us/security/benchmark/azure/security-controls-v3-endpoint-security
You have an Azure subscription that has Microsoft Defender for Cloud enabled. You need to enforce ISO 2700V2013 standards for the subscription. The solution must ensure that noncompliant resources are remediated automatically
What should you use?
- A . the regulatory compliance dashboard in Defender for Cloud
- B . Azure Policy
- C . Azure Blueprints
- D . Azure role-based access control (Azure RBAC)
B
Explanation:
https://azure.microsoft.com/en-us/blog/simplifying-your-environment-setup-while-meeting-compliance-needs-with-built-in-azure-blueprints/
Your company plans to provision blob storage by using an Azure Storage account The blob storage will be accessible from 20 application sewers on the internet. You need to recommend a solution to ensure that only the application servers can access the storage account.
What should you recommend using to secure the blob storage?
- A . service tags in network security groups (NSGs)
- B . managed rule sets in Azure Web Application Firewall (WAF) policies
- C . inbound rules in network security groups (NSGs)
- D . firewall rules for the storage account
- E . inbound rules in Azure Firewall
