Practice Free SC-100 Exam Online Questions
Your company plans to follow DevSecOps best practices of the Microsoft Cloud Adoption Framework for Azure.
You need to perform threat modeling by using a top-down approach based on the Microsoft Cloud Adoption Framework for Azure.
What should you use to start the threat modeling process?
- A . the STRIDE model
- B . the DREAD model
- C . OWASP threat modeling
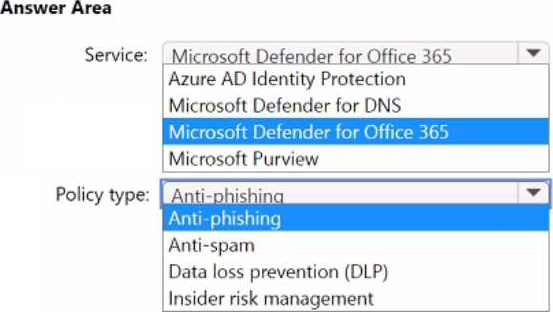
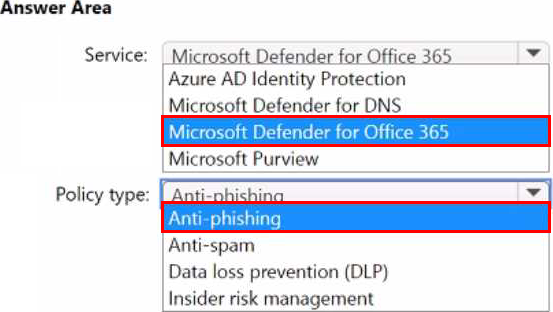
HOTSPOT
You have a Microsoft 365 E5 subscription that uses Microsoft Exchange Online.
You need to recommend a solution to prevent malicious actors from impersonating the email addresses of internal senders.
What should you include in the recommendation? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
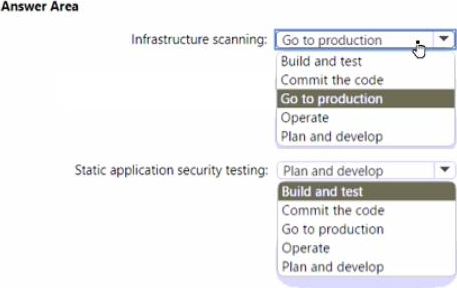
HOTSPOT
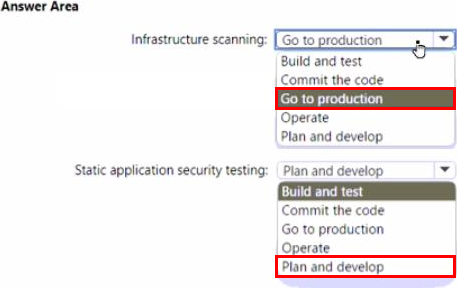
Your company plans to follow DevSecOps best practices of the Microsoft Cloud Adoption Framework for Azure to integrate DevSecOps processes into continuous integration and continuous deployment (Cl/CD) DevOps pipelines
You need to recommend which security-related tasks to integrate into each stage of the DevOps pipelines.
What should recommend? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You are designing the security standards for a new Azure environment.
You need to design a privileged identity strategy based on the Zero Trust model.
Which framework should you follow to create the design?
- A . Enhanced Security Admin Environment (ESAE)
- B . Microsoft Security Development Lifecycle (SDL)
- C . Rapid Modernization Plan (RaMP)
- D . Microsoft Operational Security Assurance (OSA)
C
Explanation:
https://docs.microsoft.com/en-us/security/compass/security-rapid-modernization-plan
This rapid modernization plan (RAMP) will help you quickly adopt Microsoft’s recommended privileged access strategy.
DRAG DROP
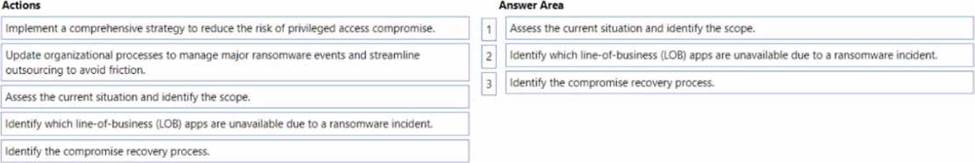
Your company wants to optimize ransomware incident investigations.
You need to recommend a plan to investigate ransomware incidents based on the Microsoft Detection and Response Team (DART) approach.
Which three actions should you recommend performing in sequence in the plan? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
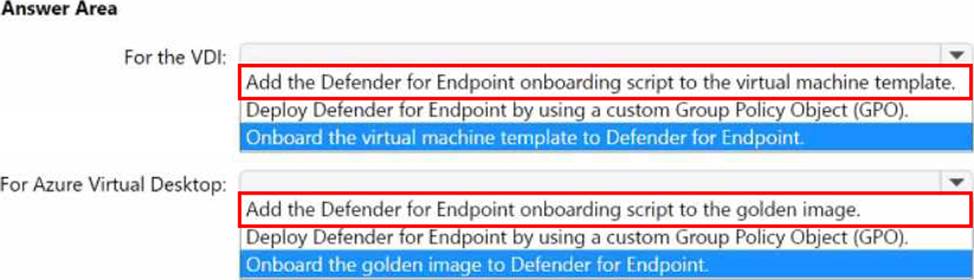
HOTSPOT
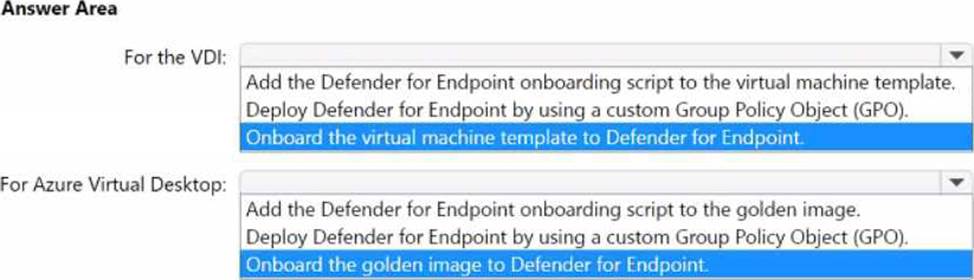
You have an Active Directory Domain Services (AD DS) domain that contains a virtual desktop infrastructure (VDI). The VDI uses non-persistent images and cloned virtual machine templates. VDI devices are members of the domain.
You have an Azure subscription that contains an Azure Virtual Desktop environment. The environment contains host pools that use a custom golden image. All the Azure Virtual Desktop deployments are members of a single Azure Active Directory Domain Services (Azure AD DS) domain. You need to recommend a solution to deploy Microsoft Defender for Endpoint to the hosts.
The solution must meet the following requirements:
• Ensure that the hosts are onboarded to Defender for Endpoint during the first startup sequence.
• Ensure that the Microsoft Defender 365 portal contains a single entry for each deployed VDI host.
• Minimize administrative effort.
What should you recommend? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You have an on-premises network and a Microsoft 365 subscription.
You are designing a Zero Trust security strategy.
Which two security controls should you include as part of the Zero Trust solution? Each correct answer part of the solution. NOTE: Each correct answer is worth one point.
- A . Block sign-attempts from unknown location.
- B . Always allow connections from the on-premises network.
- C . Disable passwordless sign-in for sensitive account.
- D . Block sign-in attempts from noncompliant devices.
You need to recommend a solution to secure the MedicalHistory data in the ClaimsDetail table. The solution must meet the Contoso developer requirements.
What should you include in the recommendation?
- A . Transparent Data Encryption (TDE)
- B . Always Encrypted
- C . row-level security (RLS)
- D . dynamic data masking
- E . data classification
D
Explanation:
https://docs.microsoft.com/en-us/learn/modules/protect-data-transit-rest/4-explain-object-encryption-secure-enclaves
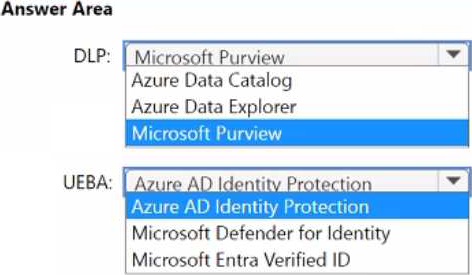
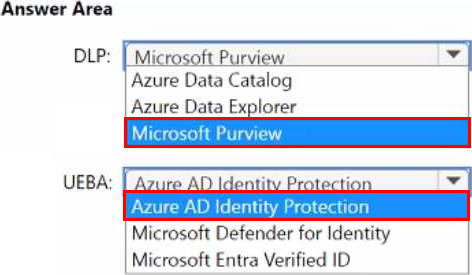
HOTSPOT
You are designing the security architecture for a cloud-only environment.
You are reviewing the integration point between Microsoft 365 Defender and other Microsoft cloud services based on Microsoft Cybersecurity Reference Architectures (MCRA).
You need to recommend which Microsoft cloud services integrate directly with Microsoft 365
Defender and meet the following requirements:
• Enforce data loss prevention (DLP) policies that can be managed directly from the Microsoft 365 Defender portal.
• Detect and respond to security threats based on User and Entity Behavior Analytics (UEBA) with unified alerting.
What should you include in the recommendation for each requirement? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
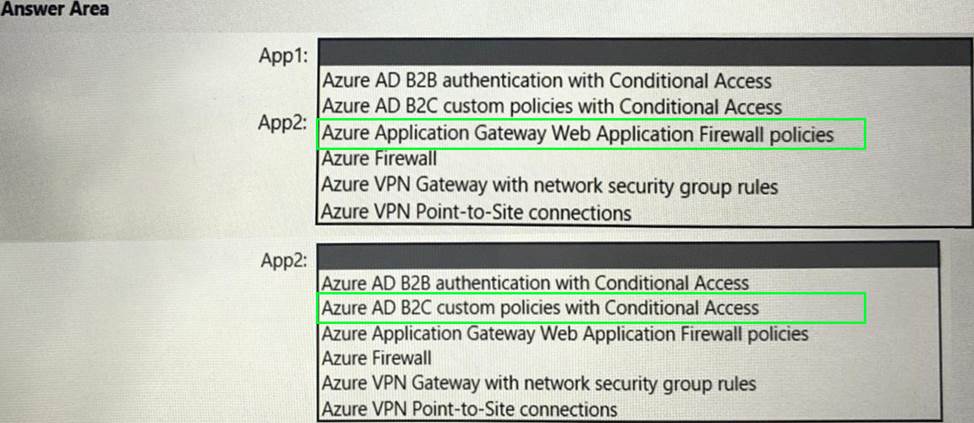
HOTSPOT
You have a hybrid cloud infrastructure.
You plan to deploy the Azure applications shown in the following table.
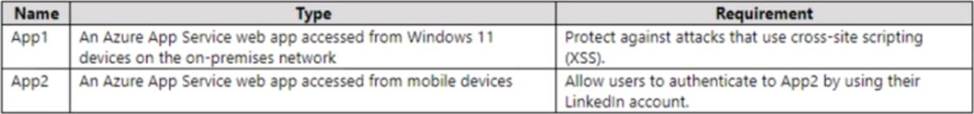
What should you use to meet the requirement of each app? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.