Practice Free SC-100 Exam Online Questions
HOTSPOT
You have an Azure subscription that contains a Microsoft Sentinel workspace named MSW1. MSW1 includes 50 scheduled analytics rules.
You need to design a security orchestration automated response (SOAR) solution by using Microsoft Sentinel playbooks.
The solution must meet the following requirements:
• Ensure that expiration dates can be configured when a playbook runs.
• Minimize the administrative effort required to configure individual analytics rules.
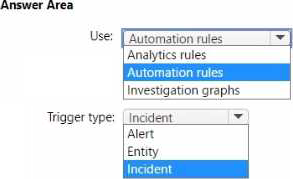
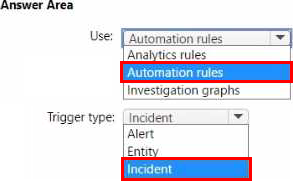
What should you use to invoke the playbooks, and which type of Microsoft Sentinel trigger should you use? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You have an Azure subscription. The subscription contains 50 virtual machines that run Windows Server and 50 virtual machines that run Linux. You need to perform vulnerability assessments on the virtual machines.
The solution must meet the following requirements:
• Identify missing updates and insecure configurations.
• Use the Qualys engine.
What should you use?
- A . Microsoft Defender for Servers
- B . Microsoft Defender Threat Intelligence (Defender Tl)
- C . Microsoft Defender for Endpoint
- D . Microsoft Defender External Attack Surface Management (Defender EASM)
A customer has a Microsoft 365 E5 subscription and an Azure subscription.
The customer wants to centrally manage security incidents, analyze log, audit activity, and search for potential threats across all deployed services.
You need to recommend a solution for the customer. The solution must minimize costs.
What should you include in the recommendation?
- A . Microsoft 365 Defender
- B . Microsoft Defender for Cloud
- C . Microsoft Defender for Cloud Apps
- D . Microsoft Sentinel
You have an Azure subscription that has Microsoft Defender for Cloud enabled.
You are evaluating the Azure Security Benchmark V3 report.
In the Secure management ports controls, you discover that you have 0 out of a potential 8 points. You need to recommend configurations to increase the score of the Secure management ports controls.
Solution: You recommend enabling just-in-time (JIT) VM access on all virtual machines.
Does this meet the goal?
- A . Yes
- B . No
A
Explanation:
https://docs.microsoft.com/en-us/security/benchmark/azure/security-controls-v3-privileged-access#pa-2-avoid-standing-access-for-user-accounts-and-permissions
Your company has an on-premises network, an Azure subscription, and a Microsoft 365 E5 subscription.
The company uses the following devices:
• Computers that run either Windows 10 or Windows 11
• Tablets and phones that run either Android or iOS
You need to recommend a solution to classify and encrypt sensitive Microsoft Office 365 data regardless of where the data is stored.
What should you include in the recommendation?
- A . eDiscovery
- B . retention policies
- C . Compliance Manager
- D . Microsoft Information Protection
D
Explanation:
https://docs.microsoft.com/en-us/microsoft-365/compliance/information-protection
https://docs.microsoft.com/en-us/microsoft-365/compliance/ediscovery?view=o365-worldwide
Your company is developing a new Azure App Service web app. You are providing design assistance to verify the security of the web app.
You need to recommend a solution to test the web app for vulnerabilities such as insecure server configurations, cross-site scripting (XSS), and SQL injection.
What should you include in the recommendation?
- A . interactive application security testing (IAST)
- B . static application security testing (SAST)
- C . runtime application se/f-protection (RASP)
- D . dynamic application security testing (DAST)
D
Explanation:
https://docs.microsoft.com/en-us/azure/security/develop/secure-develop#test-your-application-in-an-operating-state
You are designing a ransomware response plan that follows Microsoft Security Best Practices.
You need to recommend a solution to minimize the risk of a ransomware attack encrypting local user files.
What should you include in the recommendation?
- A . Microsoft Defender for Endpoint
- B . Windows Defender Device Guard
- C . protected folders
- D . Azure Files
- E . BitLocker Drive Encryption (BitLocker)
You are designing a ransomware response plan that follows Microsoft Security Best Practices.
You need to recommend a solution to minimize the risk of a ransomware attack encrypting local user files.
What should you include in the recommendation?
- A . Microsoft Defender for Endpoint
- B . Windows Defender Device Guard
- C . protected folders
- D . Azure Files
- E . BitLocker Drive Encryption (BitLocker)
You have a Microsoft 365 subscription.
You are designing a user access solution that follows the Zero Trust principles of the Microsoft Cybersecurity Reference Architectures (MCRA).
You need to recommend a solution that automatically restricts access to Microsoft Exchange Online.
SharePoint Online, and Teams m near-real-lime (NRT) in response to the following Azure AD events:
• A user account is disabled or deleted
• The password of a user is changed or reset.
• All the refresh tokens for a user are revoked
• Multi-factor authentication (MFA) is enabled for a user
Which two features should you include in the recommendation? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
- A . continuous access evaluation
- B . a sign-in risk policy
- C . Azure AD Privileged Identity Management (PIM)
- D . Conditional Access
- E . Azure AD Application Proxy
Your company plans to follow DevSecOps best practices of the Microsoft Cloud Adoption Framework for Azure.
You need to perform threat modeling by using a top-down approach based on the Microsoft Cloud Adoption Framework for Azure.
What should you use to start the threat modeling process?
- A . the STRIDE model
- B . the DREAD model
- C . OWASP threat modeling
