Practice Free PT0-002 Exam Online Questions
A penetration tester writes the following script:
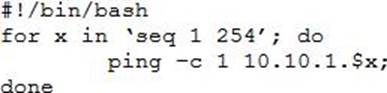
Which of the following objectives is the tester attempting to achieve?
- A . Determine active hosts on the network.
- B . Set the TTL of ping packets for stealth.
- C . Fill the ARP table of the networked devices.
- D . Scan the system on the most used ports.
The results of an Nmap scan are as follows:
Starting Nmap 7.80 ( https://nmap.org ) at 2021-01-24 01:10 EST
Nmap scan report for ( 10.2.1.22 )
Host is up (0.0102s latency).
Not shown: 998 filtered ports
Port State Service
80/tcp open http
|_http-title: 80F 22% RH 1009.1MB (text/html)
|_http-slowloris-check:
| VULNERABLE:
| Slowloris DoS Attack
| <..>
Device type: bridge|general purpose
Running (JUST GUESSING) : QEMU (95%)
OS CPE: cpe:/a:qemu:qemu
No exact OS matches found for host (test conditions non-ideal).
OS detection performed. Please report any incorrect results at https://nmap.org/submit/. Nmap done: 1 IP address (1 host up) scanned in 107.45 seconds
Which of the following device types will MOST likely have a similar response? (Choose two.)
- A . Network device
- B . Public-facing web server
- C . Active Directory domain controller
- D . IoT/embedded device
- E . Exposed RDP
- F . Print queue
B,D
Explanation:
https://www.netscout.com/what-is-ddos/slowloris-attacks
From the http-title in the output, this looks like an IoT device with RH implying Relative Humidity, that offers a web-based interface for visualizing the results.
A penetration tester is conducting an assessment for an e-commerce company and successfully copies the user database to the local machine. After a closer review, the penetration tester identifies several high-profile celebrities who have active user accounts with the online service.
Which of the following is the most appropriate next step?
- A . Contact the high-profile celebrities.
- B . Delete the high-profile accounts.
- C . Immediately contact the client.
- D . Record the findings in the penetration test report.
C
Explanation:
Upon discovering sensitive information, such as high-profile celebrities’ user accounts, the most appropriate and ethical next step is to immediately contact the client. This allows the client to take necessary actions to secure the data and mitigate any potential risks. It is important for a penetration tester to maintain confidentiality and integrity, and directly contacting the celebrities (option A), deleting the accounts (option B), or merely recording the findings without immediate notification (option D) would not be appropriate professional responses.
A penetration tester found several critical SQL injection vulnerabilities during an assessment of a client’s system. The tester would like to suggest mitigation to the client as soon as possible.
Which of the following remediation techniques would be the BEST to recommend? (Choose two.)
- A . Closing open services
- B . Encryption users’ passwords
- C . Randomizing users’ credentials
- D . Users’ input validation
- E . Parameterized queries
- F . Output encoding
Which of the following is the most important aspect to consider when calculating the price of a penetration test service for a client?
- A . Operating cost
- B . Required scope of work
- C . Non-disclosure agreement
- D . Client’s budget
B
Explanation:
When calculating the price of a penetration test service for a client, the most important aspect to consider is the required scope of work 1. The scope of work defines the objectives of the penetration test and the systems that will be tested. It is important to understand the scope of work to determine the resources required to complete the test and the time it will take to complete the test 2.
Reference: 2: CompTIA. (2021). CompTIA PenTest+ Certification Exam Objectives. Retrieved from https://www.comptia.org/content/dam/comptia/documents/certifications/Exam%20Objectives/Co mpTIA-PenTest%2B%20Exam%20Objectives%20PT0-002.pdf 1: O’Brien,
D. (2021). The Official CompTIA PenTest+ Study Guide (Exam PT0-002). John Wiley & Sons.
A penetration tester wrote the following script on a compromised system:
#!/bin/bash
network=’10.100.100′
ports=’22 23 80 443′
for x in {1 .. 254};
do (nc -zv $network.$x $ports );
done
Which of the following would explain using this script instead of another tool?
- A . The typical tools could not be used against Windows systems.
- B . The configuration required the penetration tester to not utilize additional files.
- C . The Bash script will provide more thorough output.
- D . The penetration tester wanted to persist this script to run on reboot.
A penetration tester has extracted password hashes from the lsass.exe memory process.
Which of the following should the tester perform NEXT to pass the hash and provide persistence with the newly acquired credentials?
- A . Use Patator to pass the hash and Responder for persistence.
- B . Use Hashcat to pass the hash and Empire for persistence.
- C . Use a bind shell to pass the hash and WMI for persistence.
- D . Use Mimikatz to pass the hash and PsExec for persistence.
D
Explanation:
Mimikatz is a credential hacking tool that can be used to extract logon passwords from the LSASS process and pass them to other systems. Once the tester has the hashes, they can then use PsExec, a command-line utility from Sysinternals, to pass the hash to the remote system and authenticate with the new credentials. This provides the tester with persistence on the system, allowing them to access it even after a reboot.
"A penetration tester who has extracted password hashes from the lsass.exe memory process can use various tools to pass the hash and gain access to other systems using the same credentials. One tool commonly used for this purpose is Mimikatz, which can extract plaintext passwords from memory or provide a pass-the-hash capability. After gaining access to a system, the tester can use various tools for persistence, such as PsExec or WMI." (CompTIA PenTest+ Study Guide, p. 186)
Which of the following is the MOST common vulnerability associated with IoT devices that are directly connected to the Internet?
- A . Unsupported operating systems
- B . Susceptibility to DDoS attacks
- C . Inability to network
- D . The existence of default passwords
A penetration testing team has gained access to an organization’s data center, but the team requires more time to test the attack strategy.
Which of the following wireless attack techniques would be the most successful in preventing unintended interruptions?
- A . Captive portal
- B . Evil twin
- C . Bluejacking
- D . Jamming
B
Explanation:
An evil twin attack involves setting up a rogue wireless access point that mimics a legitimate one.
This type of attack can be highly effective in a penetration testing scenario because it can intercept and capture data transmitted over the network without causing noticeable interruptions to the normal operation of the wireless network. Users are tricked into connecting to the evil twin instead of the legitimate access point, allowing the penetration testers to capture sensitive information. Unlike jamming, which disrupts the network, or bluejacking, which is limited to sending unsolicited messages, the evil twin can facilitate man-in-the-middle attacks seamlessly.
Reference: OWASP Wireless Evil Twin Attack
Kali Linux Evil Twin Tutorial
A tester who is performing a penetration test on a website receives the following output:
Warning: mysql_fetch_array() expects parameter 1 to be resource, boolean given in /var/www/search.php on line 62
Which of the following commands can be used to further attack the website?
- A . <script>var adr= ‘../evil.php?test=’ + escape(document.cookie);</script>
- B . ../../../../../../../../../../etc/passwd
- C . /var/www/html/index.php;whoami
- D . 1 UNION SELECT 1, DATABASE(),3–
