Practice Free PT0-002 Exam Online Questions
In an unprotected network file repository, a penetration tester discovers a text file containing usernames and passwords in cleartext and a spreadsheet containing data for 50 employees, including full names, roles, and serial numbers. The tester realizes some of the passwords in the text file follow the format: <name- serial_number>.
Which of the following would be the best action for the tester to take NEXT with this information?
- A . Create a custom password dictionary as preparation for password spray testing.
- B . Recommend using a password manage/vault instead of text files to store passwords securely.
- C . Recommend configuring password complexity rules in all the systems and applications.
- D . Document the unprotected file repository as a finding in the penetration-testing report.
After gaining access to a previous system, a penetration tester runs an Nmap scan against a network with the following results:
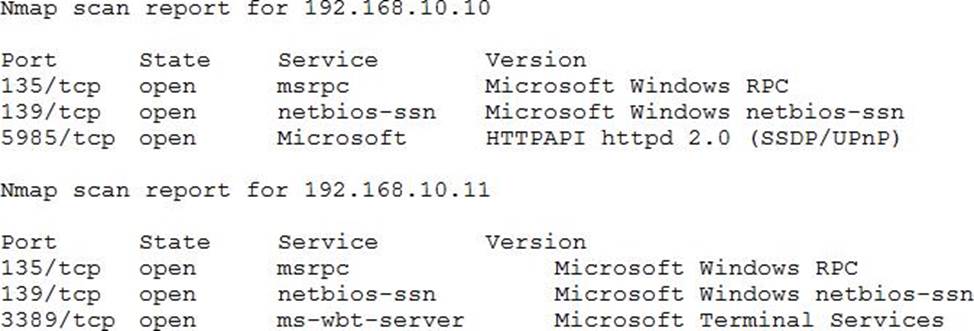
The tester then runs the following command from the previous exploited system, which fails:
Which of the following explains the reason why the command failed?
- A . The tester input the incorrect IP address.
- B . The command requires the -port 135 option.
- C . An account for RDP does not exist on the server.
- D . PowerShell requires administrative privilege.
A red team completed an engagement and provided the following example in the report to describe how the team gained access to a web server:
x’ OR role LIKE ‘%admin%
Which of the following should be recommended to remediate this vulnerability?
- A . Multifactor authentication
- B . Encrypted communications
- C . Secure software development life cycle
- D . Parameterized queries
A penetration tester ran the following commands on a Windows server:
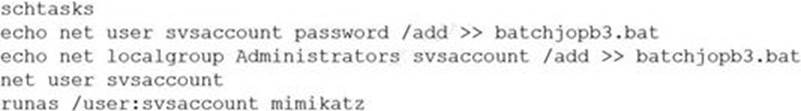
Which of the following should the tester do AFTER delivering the final report?
- A . Delete the scheduled batch job.
- B . Close the reverse shell connection.
- C . Downgrade the svsaccount permissions.
- D . Remove the tester-created credentials.
A penetration testing firm performs an assessment every six months for the same customer. While performing network scanning for the latest assessment, the penetration tester observes that several of the target hosts appear to be residential connections associated with a major television and ISP in the area.
Which of the following is the most likely reason for the observation?
- A . The penetration tester misconfigured the network scanner.
- B . The network scanning tooling is not functioning properly.
- C . The IP ranges changed ownership.
- D . The network scanning activity is being blocked by a firewall.
C
Explanation:
When a penetration tester notices several target hosts appearing to be residential connections associated with a major television and ISP, it’s likely that the IP ranges initially assigned to the target organization have changed ownership and are now allocated to the ISP for residential use. This can happen due to reallocation of IP addresses by regional internet registries. Misconfiguration of the scanner (option A), malfunctioning of scanning tools (option B), or firewall blocking (option D) would not typically result in the discovery of residential connections in place of expected organizational targets.
Which of the following would a company’s hunt team be MOST interested in seeing in a final report?
- A . Executive summary
- B . Attack TTPs
- C . Methodology
- D . Scope details
A penetration tester will be performing a vulnerability scan as part of the penetration test on a client’s website. The tester plans to run several Nmap scripts that probe for vulnerabilities while avoiding detection.
Which of the following Nmap options will the penetration tester MOST likely utilize?
- A . -8 -T0
- B . –script "http*vuln*"
- C . -sn
- D . -O -A
Which of the following BEST explains why a penetration tester cannot scan a server that was previously scanned successfully?
- A . The IP address is wrong.
- B . The server is unreachable.
- C . The IP address is on the blocklist.
- D . The IP address is on the allow list.
B
Explanation:
A server may be unreachable for a variety of reasons, such as network outages, changes in firewall rules, the server being offline or otherwise unavailable. This would prevent a penetration tester from scanning the server, even if it was previously scanned successfully.
A) While a wrong IP address would prevent successful scanning, it doesn’t explain why a server that was previously scanned successfully cannot be scanned now.
C) While a blocklist would prevent a server from being scanned, it’s less likely to be the reason in this case, as a blocklist would likely have prevented the original successful scan as well.
D) Being on an allow list would not prevent a server from being scanned. Instead, it would more likely enable it to be scanned, since allow lists typically contain IP addresses that are permitted to perform certain actions.
A penetration tester is working to enumerate the PLC devices on the 10.88.88.76/24 network.
Which of the following commands should the tester use to achieve the objective in a way that minimizes the risk of affecting the PLCs?
- A . nmap ―script=s7-info -p 102 10.88.88.76/24 -T3
- B . nmap ―script=wsdd-discover -p 3702 -sUlO.88.88.76/24
- C . nmap –script=iax2-version -p 4569 -sU -V 10.88.88.76/24 -T2
- D . nmap –script=xll-access -p 6000-6009 10.88.88.76/24
A
Explanation:
The nmap command with the ―script=s7-info is specifically designed to interact with Siemens S7 PLCs, which are common industrial control systems. The -p 102 specifies the port associated with Siemens S7 communications. The -T3 timing option is chosen to minimize the risk of impacting the PLCs by not being overly aggressive in the scan timing, which is important in operational technology environments where PLCs can be sensitive to high network traffic. The other options listed do not specifically target PLC devices or use appropriate timing to minimize risk.
A penetration tester is conducting an assessment of an organization that has both a web and mobile application. While testing the user profile page, the penetration tester notices that additional data is returned in the API response, which is not displayed in the web user interface.
Which of the following is the most effective technique to extract sensitive user data?
- A . Compare PI I from data leaks to publicly exposed user profiles.
- B . Target the user profile page with a denial-of-service attack.
- C . Target the user profile page with a reflected XSS attack.
- D . Compare the API response fields to GUI fields looking for PH.
D
Explanation:
When additional data is returned in the API response that is not displayed in the web user interface, it indicates that there might be sensitive data being transmitted that is not intended for user display. By comparing the fields returned in the API response to those that are visible in the GUI, a penetration tester can identify any Personally Identifiable Information (PII) or other sensitive data that might be exposed unintentionally. This method is direct and does not involve attacking the system but rather analyzing the data being transmitted. The other options do not directly address the identification of sensitive data in API responses.
