Practice Free PT0-002 Exam Online Questions
Which of the following tools should a penetration tester use to crawl a website and build a wordlist using the data recovered to crack the password on the website?
- A . DirBuster
- B . CeWL
- C . w3af
- D . Patator
B
Explanation:
CeWL, the Custom Word List Generator, is a Ruby application that allows you to spider a website based on a URL and depth setting and then generate a wordlist from the files and web pages it finds. Running CeWL against a target organization’s sites can help generate a custom word list, but you will typically want to add words manually based on your own OSINT gathering efforts.
https://esgeeks.com/como-utilizar-cewl/
Which of the following situations would require a penetration test er to notify the emergency contact for the engagement?
- A . The team exploits a critical server within the organization.
- B . The team exfiltrates PII or credit card data from the organization.
- C . The team loses access to the network remotely.
- D . The team discovers another actor on a system on the network.
Which of the following situations would require a penetration test er to notify the emergency contact for the engagement?
- A . The team exploits a critical server within the organization.
- B . The team exfiltrates PII or credit card data from the organization.
- C . The team loses access to the network remotely.
- D . The team discovers another actor on a system on the network.
A penetration tester is enumerating shares and receives the following output:
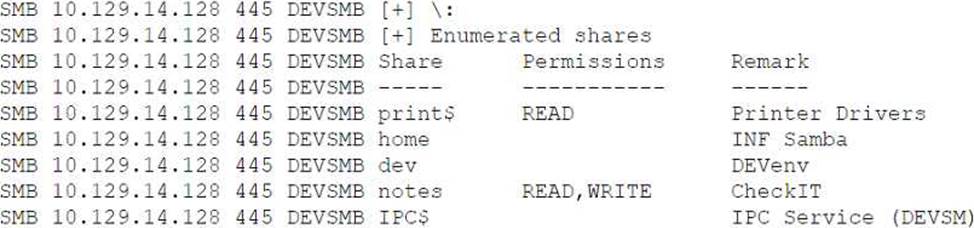
Which of the following should the penetration tester enumerate next?
- A . dev
- B . print$
- C . home
- D . notes
D
Explanation:
Given the output, which indicates that the "notes" share has READ, WRITE permissions, this could be the most interesting from a penetration testing perspective. Having write access to a share means that a tester could potentially upload files to it, which could be used to exploit further vulnerabilities, such as uploading a malicious payload.
A penetration tester obtained the following results after scanning a web server using the dirb utility:
…
GENERATED WORDS: 4612
—- Scanning URL: http://10.2.10.13/ —-
+ http://10.2.10.13/about (CODE:200|SIZE:1520)
+ http://10.2.10.13/home.html (CODE:200|SIZE:214)
+ http://10.2.10.13/index.html (CODE:200|SIZE:214)
+ http://10.2.10.13/info (CODE:200|SIZE:214)
…
DOWNLOADED: 4612 C FOUND: 4
Which of the following elements is MOST likely to contain useful information for the penetration tester?
- A . index.html
- B . about
- C . info
- D . home.html
A client has requested that the penetration test scan include the following UDP services:
SNMP, NetBIOS, and DNS.
Which of the following Nmap commands will perform the scan?
- A . nmap Cvv sUV Cp 53, 123-159 10.10.1.20/24 CoA udpscan
- B . nmap Cvv sUV Cp 53,123,161-162 10.10.1.20/24 CoA udpscan
- C . nmap Cvv sUV Cp 53,137-139,161-162 10.10.1.20/24 CoA udpscan
- D . nmap Cvv sUV Cp 53, 122-123, 160-161 10.10.1.20/24 CoA udpscan
A penetration tester runs an Nmap scan and obtains the following output:
Starting Nmap 7.80 (https://nmap.org) at 2023-02-12 18:53 GMT
Nmap scan report for 10.22.2.2
Host is up (0.0011s latency).
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Microsoft Windows Server 2019
1433/tcp open ms-sql-s Microsoft SQL Server 2019
3389/tcp open ms-wbt-server Microsoft Terminal Services
8080/tcp open http Microsoft IIS 9.0
Which of the following commands should the penetration tester try next to explore this server?
- A . nikto -host http://10.22.2-2
- B . hydra -1 administrator -P passwords.txt ftp://10.22.2.2
- C . nmap -p 3389 ―script vnc-info.nse 10.22.2.2
- D . medusa -h 10.22.2.2 -n 1433 -u sa -P passwords.txt -M mssql
A
Explanation:
Given the Nmap scan results showing an open HTTP service on port 8080 running Microsoft IIS 9.0, the next logical step for the penetration tester would be to further explore the web server. Nikto is a web server scanner that can identify known vulnerabilities, configuration issues, and other security problems.
Using the command nikto -host http://10.22.2.2 will initiate a scan against the HTTP service on the target server, helping the tester to identify potential weaknesses that could be exploited.
Reference: Nikto official documentation: Nikto Documentation
Examples of web server vulnerability scanning in penetration testing: Writeup.
A company hired a penetration-testing team to review the cyber-physical systems in a manufacturing plant. The team immediately discovered the supervisory systems and PLCs are both connected to the company intranet.
Which of the following assumptions, if made by the penetration-testing team, is MOST likely to be valid?
- A . PLCs will not act upon commands injected over the network.
- B . Supervisors and controllers are on a separate virtual network by default.
- C . Controllers will not validate the origin of commands.
- D . Supervisory systems will detect a malicious injection of code/commands.
A new security firm is onboarding its first client. The client only allowed testing over the weekend and needed the results Monday morning. However, the assessment team was not able to access the environment as expected until Monday.
Which of the following should the security company have acquired BEFORE the start of the assessment?
- A . A signed statement of work
- B . The correct user accounts and associated passwords
- C . The expected time frame of the assessment
- D . The proper emergency contacts for the client
During an engagement, a penetration tester found the following list of strings inside a file:
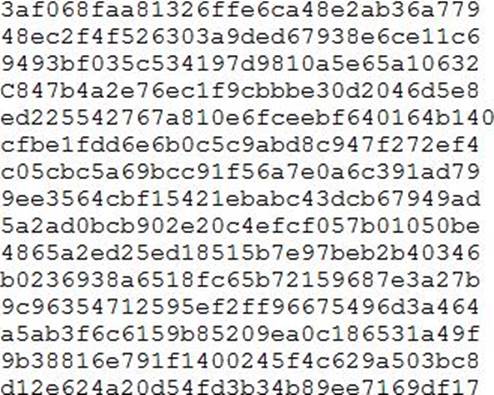
Which of the following is the BEST technique to determine the known plaintext of the strings?
- A . Dictionary attack
- B . Rainbow table attack
- C . Brute-force attack
- D . Credential-stuffing attack
