Practice Free PT0-002 Exam Online Questions
A penetration tester is performing a vulnerability scan on a large ATM network. One of the organization’s requirements is that the scan does not affect legitimate clients’ usage of the ATMs.
Which of the following should the tester do to best meet the company’s vulnerability scan requirements?
- A . Use Nmap’s -T2 switch to run a slower scan and with less resources.
- B . Run the scans using multiple machines.
- C . Run the scans only during lunch hours.
- D . Use Nmap’s -host-timeout switch to skip unresponsive targets.
When accessing the URL http://192.168.0-1/validate/user.php, a penetration tester obtained the following output:
..d index: eid in /apache/www/validate/user.php line 12
..d index: uid in /apache/www/validate/user.php line 13
..d index: pw in /apache/www/validate/user.php line 14
..d index: acl in /apache/www/validate/user.php line 15
- A . Lack of code signing
- B . Incorrect command syntax
- C . Insufficient error handling
- D . Insecure data transmission
C
Explanation:
The most probable cause for this output is insufficient error handling, which is a coding flaw that occurs when a program does not handle errors or exceptions properly or gracefully. Insufficient error handling can result in unwanted or unexpected behavior, such as crashes, hangs, or leaks. In this case, the output shows that the program is displaying warning messages that indicate undefined indexes in the user.php file. These messages reveal the names of the variables and the file path that are used by the program, which can expose sensitive information or clues to an attacker. The program should have implemented error handling mechanisms, such as try-catch blocks, error logging, or sanitizing output, to prevent these messages from being displayed or to handle them appropriately. The other options are not plausible causes for this output. Lack of code signing is a security flaw that occurs when a program does not have a digital signature that verifies its authenticity and integrity. Incorrect command syntax is a user error that occurs when a command is entered with wrong or missing parameters or options. Insecure data transmission is a security flaw that occurs when data is sent over a network without encryption or protection.
Which of the following types of information should be included when writing the remediation section of a penetration test report to be viewed by the systems administrator and technical staff?
- A . A quick description of the vulnerability and a high-level control to fix it
- B . Information regarding the business impact if compromised
- C . The executive summary and information regarding the testing company
- D . The rules of engagement from the assessment
A
Explanation:
The systems administrator and the technical stuff would be more interested in the technical aspect of the findings
A penetration tester is preparing to perform activities for a client that requires minimal disruption to company operations.
Which of the following are considered passive reconnaissance tools? (Choose two.)
- A . Wireshark
- B . Nessus
- C . Retina
- D . Burp Suite
- E . Shodan
- F . Nikto
A,E
Explanation:
Reference: https://resources.infosecinstitute.com/topic/top-10-network-recon-tools/
Given the following code:
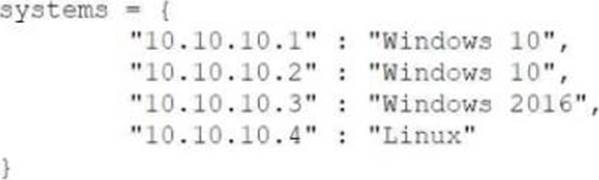
Which of the following data structures is systems?
- A . A tuple
- B . A tree
- C . An array
- D . A dictionary
A penetration tester runs a scan against a server and obtains the following output:
21/tcp open ftp Microsoft ftpd
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| 03-12-20 09:23AM 331 index.aspx
| ftp-syst:
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Microsoft Windows Server 2012 Std
3389/tcp open ssl/ms-wbt-server
| rdp-ntlm-info:
| Target Name: WEB3
| NetBIOS_Computer_Name: WEB3
| Product_Version: 6.3.9600
|_ System_Time: 2021-01-15T11:32:06+00:00
8443/tcp open http Microsoft IIS httpd 8.5
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/8.5
|_http-title: IIS Windows Server
Which of the following command sequences should the penetration tester try NEXT?
- A . ftp 192.168.53.23
- B . smbclient \\WEB3\IPC$ -I 192.168.53.23 CU guest
- C . ncrack Cu Administrator CP 15worst_passwords.txt Cp rdp 192.168.53.23
- D . curl CX TRACE https://192.168.53.23:8443/index.aspx
- E . nmap C-script vuln CsV 192.168.53.23
A new client hired a penetration-testing company for a month-long contract for various security assessments against the client’s new service. The client is expecting to make the new service publicly available shortly after the assessment is complete and is planning to fix any findings, except for critical issues, after the service is made public. The client wants a simple report structure and does not want to receive daily findings.
Which of the following is most important for the penetration tester to define FIRST?
- A . Establish the format required by the client.
- B . Establish the threshold of risk to escalate to the client immediately.
- C . Establish the method of potential false positives.
- D . Establish the preferred day of the week for reporting.
A penetration tester ran a ping CA command during an unknown environment test, and it returned a 128 TTL packet.
Which of the following OSs would MOST likely return a packet of this type?
- A . Windows
- B . Apple
- C . Linux
- D . Android
A
Explanation:
Reference: https://www.freecodecamp.org/news/how-to-identify-basic-internet-problems-with-ping/
A penetration tester gives the following command to a systems administrator to execute on one of the target servers:
rm -f /var/www/html/G679h32gYu.php
Which of the following BEST explains why the penetration tester wants this command executed?
- A . To trick the systems administrator into installing a rootkit
- B . To close down a reverse shell
- C . To remove a web shell after the penetration test
- D . To delete credentials the tester created
During an internal penetration test against a company, a penetration tester was able to navigate to another part of the network and locate a folder containing customer information such as addresses, phone numbers, and credit card numbers.
To be PCI compliant, which of the following should the company have implemented to BEST protect this data?
- A . Vulnerability scanning
- B . Network segmentation
- C . System hardening
- D . Intrusion detection
