Practice Free PT0-002 Exam Online Questions
During a security assessment, a penetration tester decides to implement a simple TCP port scanner to check the open ports from 1000 to 2000.
Which of the following Python scripts would achieve this task?
- A . for i in range(1000, 2001): s = socket(AF_INET, SOCK_STREAM)
conn = s.connect_ex((host_IP, i))
if (conn == 0):
print(fPort {i} OPEN’)
s.close () - B . for i in range(1001, 2000): s = socket(AF_INET, SOCK_STREAM)
conn = s.connect_ex((host_IP, i))
if (conn == 0):
print (f’Port {i} OPEN’)
s.close () - C . for i in range(1000, 2001): s = socket(AF―INET, SOCK_DGRAM)
conn = s.connect―
ex((host_IP, i))
if (conn == 0):
print(f’Port {i} OPEN’)
s.close () - D . for i in range (1000, 2000): s = socket(SOCK_STREAM, AF_INET)
conn = s.connect―
ex((host―IP, i))
if (conn == 0):
print (f’Port {i} OPEN’)
s.close()
A
Explanation:
The correct Python script for implementing a simple TCP port scanner that checks for open ports from 1000 to 2000 is option A. This script uses a for loop to iterate through the range of ports, creates a socket object for each port using the socket.AF_INET address family (indicating IPv4) and socket.SOCK_STREAM socket type (indicating TCP), and attempts to connect to each port. If the connection attempt (connect_ex) returns 0, it indicates the port is open, and the script prints a message stating that the port is open before closing the socket. The other options contain syntax errors, use incorrect socket types, or have incorrect ranges that do not fully cover the specified ports.
Company.com has hired a penetration tester to conduct a phishing test. The tester wants to set up a fake log-in page and harvest credentials when target employees click on links in a phishing email.
Which of the following commands would best help the tester determine which cloud email provider
the log-in page needs to mimic?
- A . dig company.com MX
- B . whois company.com
- C . cur1 www.company.com
- D . dig company.com A
A
Explanation:
The dig command is a tool that can be used to query DNS servers and obtain information about domain names, such as IP addresses, mail servers, name servers, or other records. The MX option specifies that the query is for mail exchange records, which are records that indicate the mail servers responsible for accepting email messages for a domain. Therefore, the command dig company.com MX would best help the tester determine which cloud email provider the log-in page needs to mimic by showing the mail servers for company.com. For example, if the output shows something like company-com.mail.protection.outlook.com, then it means that company.com uses Microsoft Outlook as its cloud email provider. The other commands are not as useful for determining the cloud email provider. The whois command is a tool that can be used to query domain name registration information, such as the owner, registrar, or expiration date of a domain. The curl command is a tool that can be used to transfer data from or to a server using various protocols, such as HTTP, FTP, or SMTP. The dig command with the A option specifies that the query is for address records, which are records that map domain names to IP addresses.
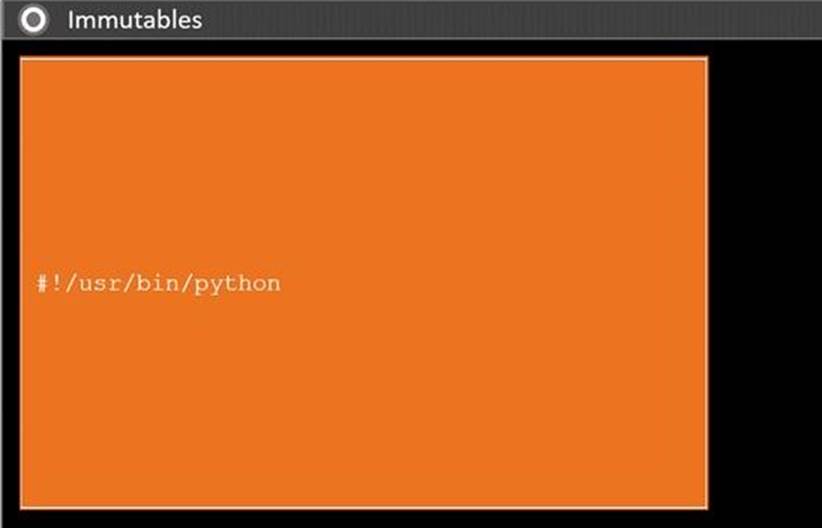
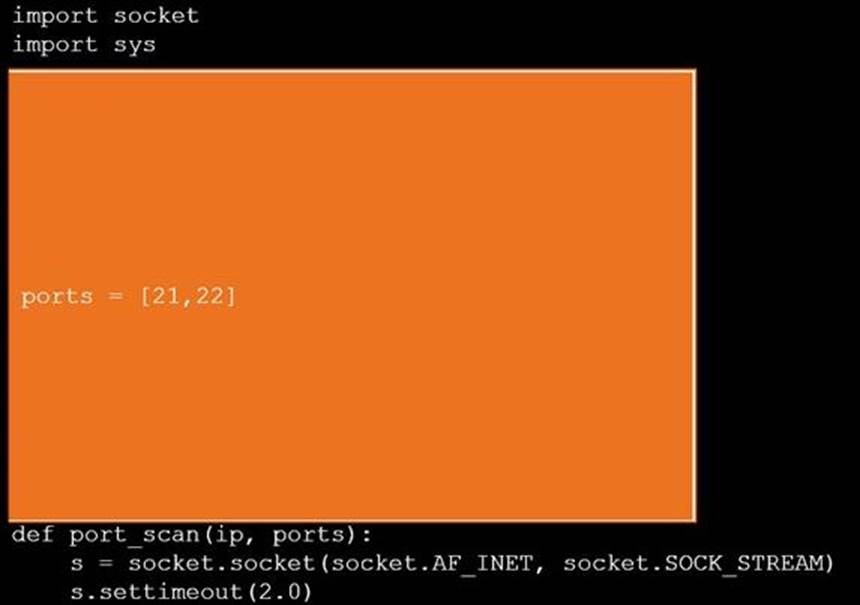
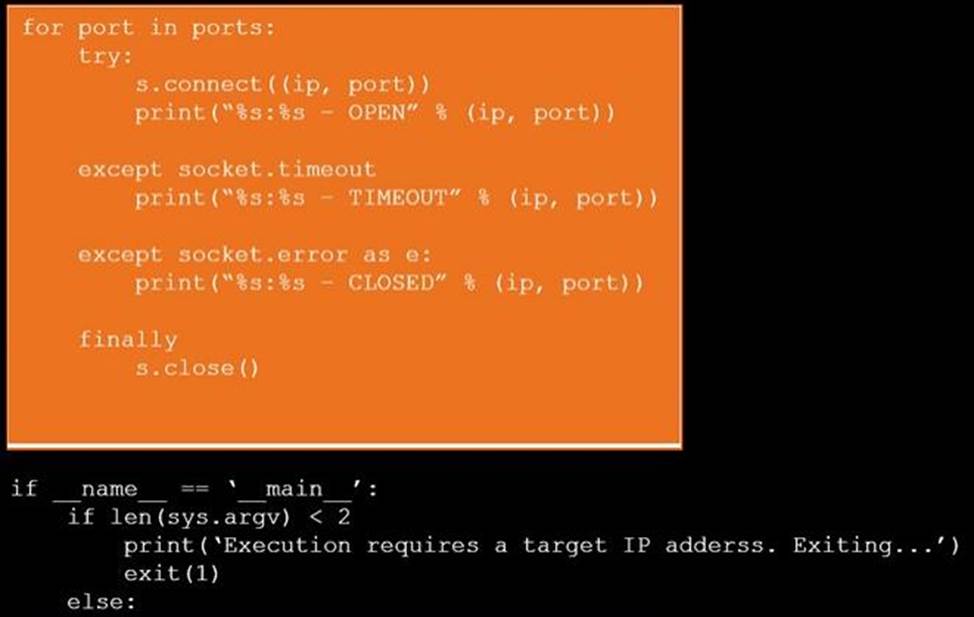
DRAG DROP
During a penetration test, you gain access to a system with a limited user interface. This
machine appears to have access to an isolated network that you would like to port scan.
INSTRUCTIONS
Analyze the code segments to determine which sections are needed to complete a port scanning script.
Drag the appropriate elements into the correct locations to complete the script.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
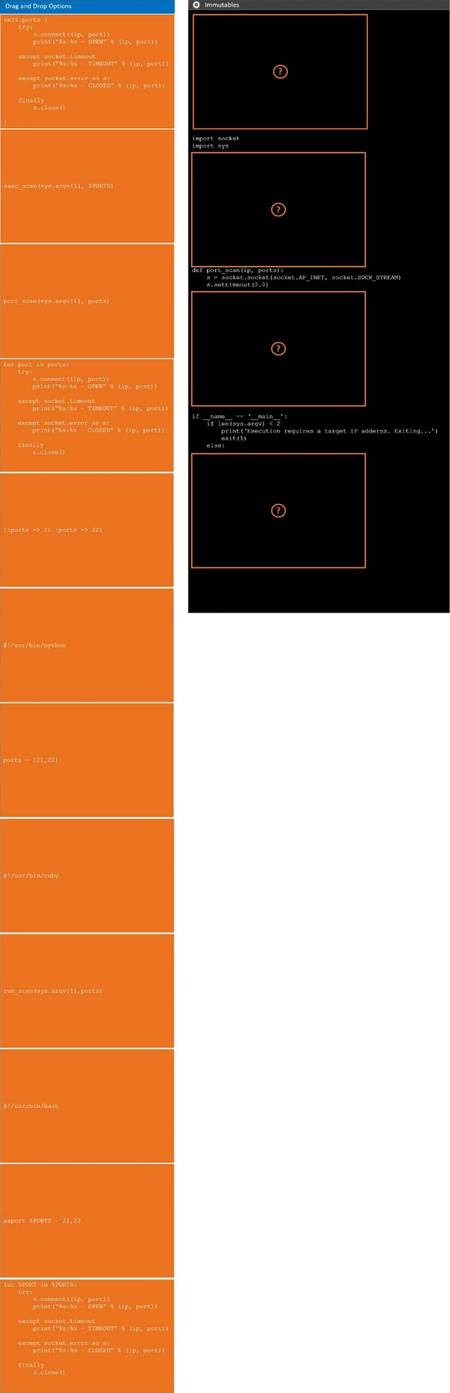

Explanation:
A picture
containing shape
Description automatically generated
A picture containing treemap chart
Description automatically generated
Text
Description automatically generated
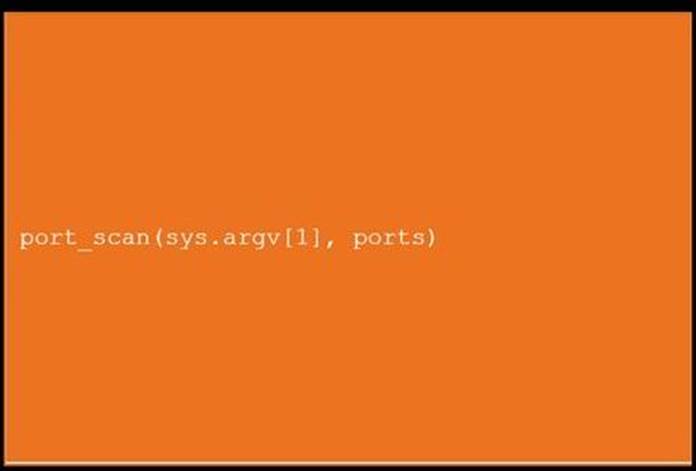
Graphical user interface
Description automatically generated
Which of the following is a rules engine for managing public cloud accounts and resources?
- A . Cloud Custodian
- B . Cloud Brute
- C . Pacu
- D . Scout Suite
A
Explanation:
Cloud Custodian is a rules engine for managing public cloud accounts and resources. It allows users to define policies to enable a well managed cloud infrastructure, that’s both secure and cost optimized. It consolidates many of the adhoc scripts organizations have into a lightweight and flexible tool, with unified metrics and reporting.
A penetration tester developed the following script to be used during an engagement:
#!/usr/bin/python
import socket, sys
ports = [21, 22, 23, 25, 80, 139, 443, 445, 3306, 3389]
if len(sys.argv) > 1:
target = socket.gethostbyname (sys. argv [0])
else:
print ("Few arguments.")
print ("Syntax: python {} <target ip>". format (sys. argv [0]))
sys.exit ()
try:
for port in ports:
s = socket. socket (socket. AF_INET, socket. SOCK_STREAM)
s.settimeout (2)
result = s.connect_ex ((target, port) ) if result == 0:
print ("Port {} is opened". format (port))
except KeyboardInterrupt:
print ("nExiting … ")
sys.exit ()
However, when the penetration tester ran the script, the tester received the following message:
socket.gaierror: [Errno -2] Name or service not known
Which of the following changes should the penetration tester implement to fix the script?
- A . From:
target = socket.gethostbyname (sys. argv [0])
To:
target = socket.gethostbyname (sys.argv[1]) - B . From:
s = socket. socket (socket. AF_INET, socket. SOCK_STREAM)
To:
s = socket.socket (socket.AF_INET, socket. SOCK_DGRAM) - C . From:
import socket, sys
To:
import socket
import sys - D . From:
result = s.connect_ex ((target, port) )
To:
result = s.connect ( (target, port) )
A
Explanation:
The socket.gaierror: [Errno -2] Name or service not known is an error that occurs when the socket module cannot resolve the hostname or IP address given as an argument. In this case, the script is using sys.argv[0] as the argument for socket.gethostbyname, which is the name of the script itself, not the target IP address. The target IP address should be the first command-line argument after the script name, which is sys.argv1. Therefore, changing the script to use sys.argv1 as the argument for socket.gethostbyname will fix the error and allow the script to scan the ports of the target IP address.
Reference: • The Official CompTIA PenTest+ Study Guide (Exam PT0-002), Chapter 5: Attacks and Exploits, page 262-263.
• socket.gaierror: [Errno -2] Name or service not known | Python1
• How do I fix the error socket.gaierror: [Errno -2] Name or service not known on debian/testing?2
A penetration tester is trying to restrict searches on Google to a specific domain.
Which of the following commands should the penetration tester consider?
- A . inurl:
- B . link:
- C . site:
- D . intitle:
Which of the following is a regulatory compliance standard that focuses on user privacy by implementing the right to be forgotten?
- A . NIST SP 800-53
- B . ISO 27001
- C . GDPR
C
Explanation:
GDPR is a regulatory compliance standard that focuses on user privacy by implementing the right to be forgotten. GDPR stands for General Data Protection Regulation, and it is a law that applies to the European Union and the United Kingdom. GDPR gives individuals the right to request their personal data be deleted by data controllers and processors under certain circumstances, such as when the data is no longer necessary, when the consent is withdrawn, or when the data was unlawfully processed. GDPR also imposes other obligations and rights related to data protection, such as data minimization, data portability, data breach notification, and consent management. The other options are not regulatory compliance standards that focus on user privacy by implementing the right to be forgotten. NIST SP 800-53 is a set of security and privacy controls for federal information systems and organizations in the United States. ISO 27001 is an international standard that specifies the requirements for an information security management system.
During an assessment, a penetration tester needs to perform a cloud asset discovery of an organization.
Which of the following tools would most likely provide more accurate results in this situation?
- A . Pacu
- B . Scout Suite
- C . Shodan
- D . TruffleHog
B
Explanation:
Scout Suite is an open-source multi-cloud security-auditing tool that enables security posture assessment of cloud environments. It is designed to provide a comprehensive and accurate analysis of cloud assets by using the APIs of cloud service providers. Scout Suite supports major cloud platforms, including AWS, Azure, and GCP, making it suitable for performing cloud asset discovery.
Other tools listed, such as Pacu, Shodan, and TruffleHog, serve different purposes. Pacu is a cloud exploitation framework for AWS, Shodan is a search engine for internet-connected devices, and TruffleHog is a tool for searching for secrets in files. While they are valuable tools, Scout Suite is specifically tailored for comprehensive cloud asset discovery.
Reference: Scout Suite GitHub page: Scout Suite
Cloud security auditing examples from penetration testing reports and best practices.
A company obtained permission for a vulnerability scan from its cloud service provider and now wants to test the security of its hosted data.
Which of the following should the tester verify FIRST to assess this risk?
- A . Whether sensitive client data is publicly accessible
- B . Whether the connection between the cloud and the client is secure
- C . Whether the client’s employees are trained properly to use the platform
- D . Whether the cloud applications were developed using a secure SDLC
Which of the following factors would a penetration tester most likely consider when testing at a location?
- A . Determine if visas are required.
- B . Ensure all testers can access all sites.
- C . Verify the tools being used are legal for use at all sites.
- D . Establish the time of the day when a test can occur.
C
Explanation:
When conducting a penetration test, especially in locations that may be under different legal jurisdictions, it is crucial to ensure that the tools and methods used are compliant with local laws. Penetration testing can sometimes involve tools or techniques that are restricted or illegal in certain areas, so verifying the legality of the tools for each site is a key consideration to avoid legal complications.
