Practice Free PT0-002 Exam Online Questions
A penetration tester wrote the following script to be used in one engagement:
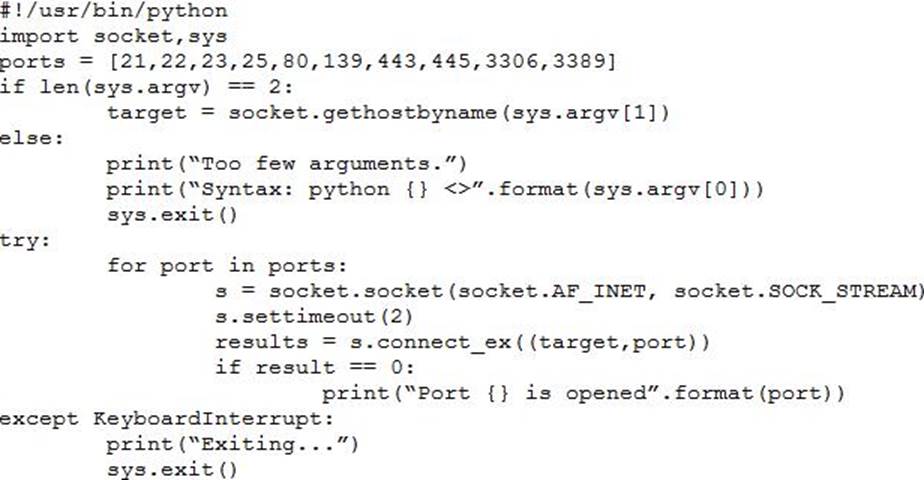
Which of the following actions will this script perform?
- A . Look for open ports.
- B . Listen for a reverse shell.
- C . Attempt to flood open ports.
- D . Create an encrypted tunnel.
A penetration tester wrote the following script to be used in one engagement:

Which of the following actions will this script perform?
- A . Look for open ports.
- B . Listen for a reverse shell.
- C . Attempt to flood open ports.
- D . Create an encrypted tunnel.
A penetration tester successfully performed an exploit on a host and was able to hop from VLAN 100 to VLAN 200. VLAN 200 contains servers that perform financial transactions, and the penetration tester now wants the local interface of the attacker machine to have a static ARP entry in the local cache.
The attacker machine has the following:
IP Address: 192.168.1.63
Physical Address: 60-36-dd-a6-c5-33
Which of the following commands would the penetration tester MOST likely use in order to establish a static ARP entry successfully?
- A . tcpdump -i eth01 arp and arp[6:2] == 2
- B . arp -s 192.168.1.63 60-36-DD-A6-C5-33
- C . ipconfig /all findstr /v 00-00-00 | findstr Physical
- D . route add 192.168.1.63 mask 255.255.255.255.0 192.168.1.1
A penetration tester who is working remotely is conducting a penetration test using a wireless connection.
Which of the following is the BEST way to provide confidentiality for the client while using this connection?
- A . Configure wireless access to use a AAA server.
- B . Use random MAC addresses on the penetration testing distribution.
- C . Install a host-based firewall on the penetration testing distribution.
- D . Connect to the penetration testing company’s VPS using a VPN.
Which of the following assessment methods is MOST likely to cause harm to an ICS environment?
- A . Active scanning
- B . Ping sweep
- C . Protocol reversing
- D . Packet analysis
A company’s Chief Executive Officer has created a secondary home office and is concerned that the WiFi service being used is vulnerable to an attack. A penetration tester is hired to test the security of the WiFi’s router.
Which of the following is MOST vulnerable to a brute-force attack?
- A . WPS
- B . WPA2-EAP
- C . WPA-TKIP
- D . WPA2-PSK
A
Explanation:
Reference: https://us-cert.cisa.gov/ncas/alerts/TA12-006A
A final penetration test report has been submitted to the board for review and accepted. The report has three findings rated high.
Which of the following should be the NEXT step?
- A . Perform a new penetration test.
- B . Remediate the findings.
- C . Provide the list of common vulnerabilities and exposures.
- D . Broaden the scope of the penetration test.
A company conducted a simulated phishing attack by sending its employees emails that included a link to a site that mimicked the corporate SSO portal. Eighty percent of the employees who received the email clicked the link and provided their corporate credentials on the fake site.
Which of the following recommendations would BEST address this situation?
- A . Implement a recurring cybersecurity awareness education program for all users.
- B . Implement multifactor authentication on all corporate applications.
- C . Restrict employees from web navigation by defining a list of unapproved sites in the corporate proxy.
- D . Implement an email security gateway to block spam and malware from email communications.
A
Explanation:
Reference: https://resources.infosecinstitute.com/topic/top-9-free-phishing-simulators/
A client wants a security assessment company to perform a penetration test against its hot site. The purpose of the test is to determine the effectiveness of the defenses that protect against disruptions to business continuity.
Which of the following is the MOST important action to take before starting this type of assessment?
- A . Ensure the client has signed the SOW.
- B . Verify the client has granted network access to the hot site.
- C . Determine if the failover environment relies on resources not owned by the client.
- D . Establish communication and escalation procedures with the client.
Penetration tester has discovered an unknown Linux 64-bit executable binary.
Which of the following tools would be BEST to use to analyze this issue?
- A . Peach
- B . WinDbg
- C . GDB
- D . OllyDbg
C
Explanation:
OLLYDBG, WinDBG, and IDA are all debugging tools that support Windows environments. GDB is a Linuxspecific debugging tool.
