Practice Free PT0-002 Exam Online Questions
A penetration tester is conducting an assessment against a group of publicly available web servers and notices a number of TCP resets returning from one of the web servers.
Which of the following is MOST likely causing the TCP resets to occur during the assessment?
- A . The web server is using a WAF.
- B . The web server is behind a load balancer.
- C . The web server is redirecting the requests.
- D . The local antivirus on the web server Is rejecting the connection.
A
Explanation:
A Web Application Firewall (WAF) is designed to monitor, filter or block traffic to a web application. A WAF will monitor incoming and outgoing traffic from a web application and is often used to protect web servers from attacks such as SQL Injection, Cross-Site Scripting (XSS), and other forms of attacks. If a WAF detects an attack, it will often reset the TCP connection, causing the connection to be terminated. As a result, a penetration tester may see TCP resets when a WAF is present. Therefore, the most likely reason for the TCP resets returning from the web server is that the web server is using a WAF.
During a security assessment of a web application, a penetration tester was able to generate the following application response:
Unclosed quotation mark after the character string Incorrect syntax near ".
Which of the following is the most probable finding?
- A . SQL injection
- B . Cross-site scripting
- C . Business logic flaw
- D . Race condition
A
Explanation:
The error message "Unclosed quotation mark after the character string Incorrect syntax near ‘." suggests that the application is vulnerable to SQL Injection (A). This type of vulnerability occurs when an attacker is able to inject malicious SQL queries into an application’s database query. The error message indicates that the application’s input handling allows for the manipulation of the underlying SQL queries, which can lead to unauthorized data access, data modification, and other database-related attacks.
Which of the following tools would be best suited to perform a cloud security assessment?
- A . OpenVAS
- B . Scout Suite
- C . Nmap
- D . ZAP
- E . Nessus
B
Explanation:
The tool that would be best suited to perform a cloud security assessment is Scout Suite, which is an open-source multi-cloud security auditing tool that can evaluate the security posture of cloud environments, such as AWS, Azure, GCP, or Alibaba Cloud. Scout Suite can collect configuration data from cloud providers using APIs and assess them against security best practices or benchmarks, such as CIS Foundations. Scout Suite can generate reports that highlight security issues, risks, or gaps in the cloud environment, and provide recommendations for remediation or improvement. The other options are not tools that are specifically designed for cloud security assessment. OpenVAS is an open-source vulnerability scanner that can scan hosts and networks for vulnerabilities and generate reports with findings and recommendations. Nmap is an open-source network scanner and enumerator that can scan hosts and networks for ports, services, versions, OS, or other information1. ZAP is an open-source web application scanner and proxy that can scan web applications for vulnerabilities and perform attacks such as SQL injection or XSS. Nessus is a commercial vulnerability scanner that can scan hosts and networks for vulnerabilities and generate reports with findings and recommendations.
A large client wants a penetration tester to scan for devices within its network that are Internet facing. The client is specifically looking for Cisco devices with no authentication requirements.
Which of the following settings in Shodan would meet the client’s requirements?
- A . “cisco-ios” “admin+1234”
- B . “cisco-ios” “no-password”
- C . “cisco-ios” “default-passwords”
- D . “cisco-ios” “last-modified”
A penetration tester ran an Nmap scan on an Internet-facing network device with the CF option and found a few open ports. To further enumerate, the tester ran another scan using the following command:
nmap CO CA CsS Cp- 100.100.100.50
Nmap returned that all 65,535 ports were filtered.
Which of the following MOST likely occurred on the second scan?
- A . A firewall or IPS blocked the scan.
- B . The penetration tester used unsupported flags.
- C . The edge network device was disconnected.
- D . The scan returned ICMP echo replies.
A
Explanation:
Reference: https://phoenixnap.com/kb/nmap-scan-open-ports
A penetration tester is looking for a vulnerability that enables attackers to open doors via a specialized TCP service that is used for a physical access control system. The service exists on more than 100 different hosts, so the tester would like to automate the assessment.
Identification requires the penetration tester to:
✑ Have a full TCP connection
✑ Send a “hello” payload
✑ Walt for a response
✑ Send a string of characters longer than 16 bytes
Which of the following approaches would BEST support the objective?
- A . Run nmap CPn CsV Cscript vuln <IP address>.
- B . Employ an OpenVAS simple scan against the TCP port of the host.
- C . Create a script in the Lua language and use it with NSE.
- D . Perform a credentialed scan with Nessus.
C
Explanation:
The Nmap Scripting Engine (NSE) is one of Nmap’s most powerful and flexible features. It allows users to write (and share) simple scripts (using the Lua programming language) to automate a wide variety of networking tasks. https://nmap.org
A penetration tester runs a reconnaissance script and would like the output in a standardized machine-readable format in order to pass the data to another application.
Which of the following is the best for the tester to use?
- A . JSON
- B . Lists
- C . XLS
- D . Trees
A
Explanation:
JSON (JavaScript Object Notation) is the best format for a penetration tester to use when they need the output of a reconnaissance script in a standardized machine-readable format to pass data to another application. JSON is widely supported across different programming languages and platforms, making it an ideal choice for data interchange. It allows for the hierarchical organization of data, is easy to read and write, and can be parsed and generated by numerous tools and libraries. This makes JSON a versatile and practical choice for a variety of applications in penetration testing and beyond.
Reference: RFC 8259 – The JavaScript Object Notation (JSON) Data Interchange Format OWASP – JSON Security
SIMULATION
A penetration tester performs several Nmap scans against the web application for a client.
INSTRUCTIONS
Click on the WAF and servers to review the results of the Nmap scans. Then click on each tab to select the appropriate vulnerability and remediation options.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.





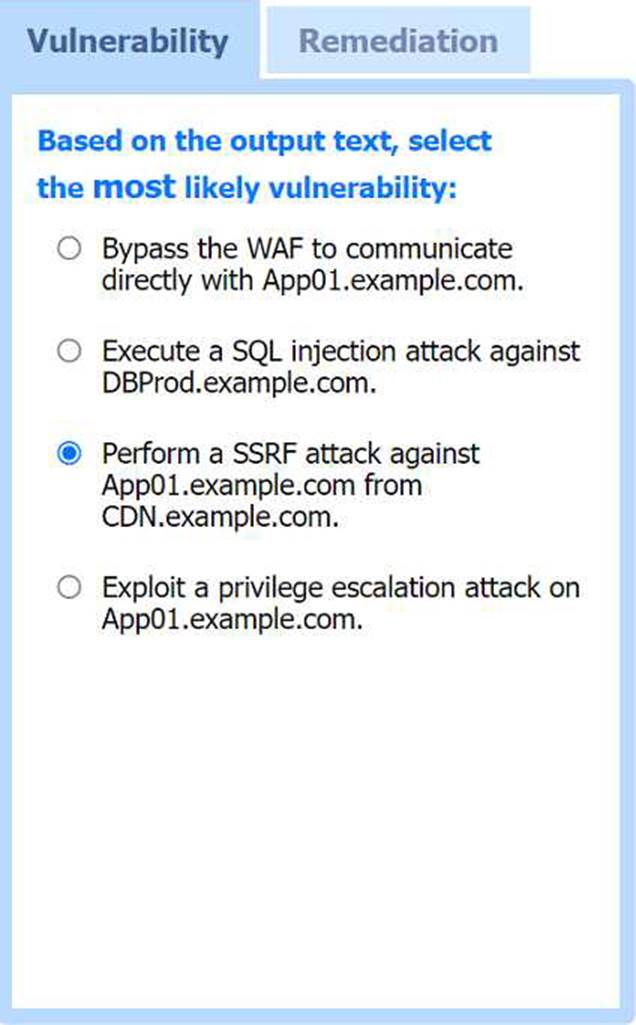

Most likely vulnerability: Perform a SSRF attack against App0 1. example.com from CDN.example.com.
The scenario suggests that the CDN network (with a WAF) can be used to perform a Server-Side Request Forgery (SSRF) attack. Since the penetration tester has the pentester workstation interacting through the CDN/WAF and the production network is behind it, the most plausible attack vector is to exploit SSRF to interact with the internal services like App0 1. example.com.
Two best remediation options:
Restrict direct communications to App0 1. example.com to only approved components.
Require an additional authentication header value between CDN.example.com and App0 1. example.com.
Restrict direct communications to App0 1. example.com to only approved components: This limits the exposure of the application server by ensuring that only specified, trusted entities can communicate with it.
Require an additional authentication header value between CDN.example.com and App0 1. example.com: Adding an authentication layer between the CDN and the app server helps ensure that requests are legitimate and originate from trusted sources, mitigating SSRF and other indirect attack vectors.
Nmap Scan Observations:
CDN/WAF shows open ports for HTTP and HTTPS but filtered for MySQL, indicating it acts as a filtering layer.
App Server has open ports for HTTP, HTTPS, and filtered for MySQL.
DB Server has all ports filtered, typical for a database server that should not be directly accessible.
These findings align with the SSRF vulnerability and the appropriate remediation steps to enhance the security of internal communications.
A penetration tester is conducting a penetration test and discovers a vulnerability on a web server that is owned by the client. Exploiting the vulnerability allows the tester to open a reverse shell. Enumerating the server for privilege escalation, the tester discovers the following:

Which of the following should the penetration tester do NEXT?
- A . Close the reverse shell the tester is using.
- B . Note this finding for inclusion in the final report.
- C . Investigate the high numbered port connections.
- D . Contact the client immediately.
A penetration tester is conducting a penetration test and discovers a vulnerability on a web server that is owned by the client. Exploiting the vulnerability allows the tester to open a reverse shell. Enumerating the server for privilege escalation, the tester discovers the following:

Which of the following should the penetration tester do NEXT?
- A . Close the reverse shell the tester is using.
- B . Note this finding for inclusion in the final report.
- C . Investigate the high numbered port connections.
- D . Contact the client immediately.
