Practice Free PEGACPLSA88V1 Exam Online Questions
Identify two important points to follow while designing enterprise applications. (Choose Two)
- A . Implement a modular architecture that minimizes the effect of changes made between applications.
- B . Build an application focused on the required communication channels to boost the productivity of consumers.
- C . Define the architecture first and then make an application fit within that architecture.
- D . Iteratively focus on the short-term goals based on the evaluation of the outcomes to achieve the business objectives.
A, B
Explanation:
Important points to follow while designing enterprise applications include:
Modular Architecture (A):
Implementing a modular architecture allows different parts of the application to be developed, maintained, and scaled independently. This minimizes the impact of changes, making the system more resilient and easier to manage.
Communication Channels (B):
Focusing on required communication channels ensures that the application meets the needs of its users, enhancing user productivity and satisfaction. This involves integrating the necessary communication tools and channels directly into the application workflow.
Reference: Pega Best Practices for Application Design
Enterprise Architecture Principles
A System Architect wants to save the results from running a data page as an automated test. The System Architect reports that the system cannot save the test definition.
What is the reason?
- A . The Pega-AutoTest agent is configured, but not running.
- B . The data page is checked out or in private edit mode.
- C . A ruleset to store test cases is not configured.
- D . The System Architect lacks the automated unit test privilege.
C
Explanation:
Test Cases Ruleset Configuration:
If the system cannot save the test definition, it is likely due to a ruleset for storing test cases not being configured. Test cases need to be stored in a specific ruleset that is configured for this purpose.
Reference: Pega documentation on automated testing and unit test cases emphasizes the need for configuring a ruleset to store test cases.
Therefore, the correct answer is:
C. A ruleset to store test cases is not configured.
A developer has set the Rule security mode on the access group to Deny. Select the reason for this setting.
- A . Require Access of Role to Object rules be specified for each layer in the class hierarchy and not inherited from parent classes.
- B . Deny access to a rule if the privilege of the user is not defined in an Access of Role to Object.
- C . Disable standard privileges providing administrator access to the application (for example AllFlows and AllFllowActions).
- D . Ensure that all rules with the option of specifying a privilege have a privilege. Only users with the privilege can execute the rules.
D
Explanation:
Setting the Rule security mode on the access group to Deny ensures that:
Privileged Access Only: It enforces that all rules which can specify a privilege must have a privilege assigned. This ensures that only users with the appropriate privileges can execute these rules. Security Compliance: This setting helps in maintaining strict security compliance by not allowing default access to rules without explicit privilege checks.
Reference: Pega Rule Security Mode
If an Operator ID in an application is associated with the work queues in the following figure, how will the system behave?
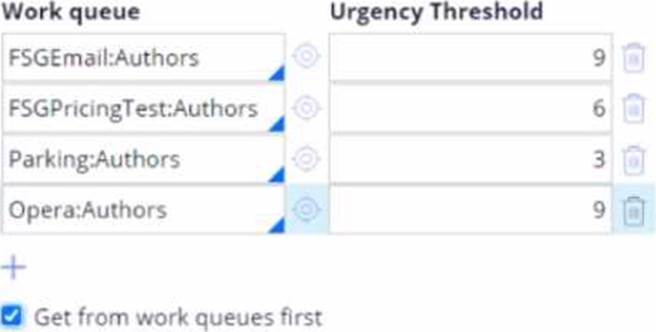
- A . The system will consider the assignments with urgency value equal to and greater than the specified value in the Operator rule, and will ignore all assignments with lower urgency value.
- B . The system will process work queues from top to bottom by ignoring urgency threshold, because the Get from work queues first option is selected, and because the system ignores all assignments with lower urgency value.
- C . The system will process work queues from top to bottom by ignoring urgency threshold, because the Get from work queues first option is selected.
- D . The system will consider the assignments with urgency value equal to and greater than the specified value in the Operator rule. Once all assignments are processed from the work queue based on the threshold urgency value, the lower urgency assignments are then considered.
D
Explanation:
The system will consider the assignments with urgency value equal to and greater than the specified value in the Operator rule. Once all assignments are processed from the work queue based on the threshold urgency value, the lower urgency assignments are then considered.
Urgency Thresholds: The system checks the urgency of assignments in each work queue.
Assignments with an urgency equal to or greater than the threshold are considered first.
Get from Work Queues First: With this option selected, the system prioritizes processing work queues before considering individual workbaskets.
Lower Urgency Assignments: After processing assignments meeting the urgency thresholds, the system will then consider lower urgency assignments if there are no higher urgency tasks left.
Reference: Pega Platform documentation on routing and assignment handling.
Pega Academy resources on urgency thresholds and work queue configurations.
DRAG DROP
Select each task on the left and drag it to the corresponding Application Development Studio on the right, where the task can be completed.
you want to expose a set of services for your application. Each service should be exposed as a separate WSDL.
How do you accomplish this?
- A . create a separate service package for each WSDL.
- B . create a service listener for each WSDL.
- C . Run the service wizard for each WSDL.
- D . place the service rules in separate classes, one class per WSDL
A
Explanation:
To expose a set of services for your application, with each service exposed as a separate WSDL:
Create a separate service package for each WSDL (Answer A):
Service packages in Pega allow you to group related services and generate WSDL files for them. By creating a separate service package for each WSDL, you can manage and expose each service independently.
Reference: Pega’s service package documentation provides details on how to configure and manage service packages to generate individual WSDL files for different services.
An application allows users to manage Account cases. You need to configure security so that users are allowed to view and update account only if they are the primary or secondary owner.
How do you implement this requirement?
- A . create a when rule that validate id the current user is either a primay or secondary owner of the account configure then when rule in the required conditions section on all flow actions that allow account updates.
- B . create a privilage and configure it to validate if the current user is either a primary or secondary owner of the account. Assign the privilege for read and write instances of the account class in the user’s access role.
- C . create an access when rule that validate if the current user is either a primary or secondary owner of the account. Assign the access when rule for read and write instances of the account class in the user’s vaccess role.
- D . create an access when rule that validate if the current user is either a primay or secondary owner of the ccount. Configure the access when rule on the Accouny case type to ensure authorized access
D
Explanation:
Create Access When Rule:
Go to Records Explorer > Security > Access When.
Create a new Access When rule that checks if the current user is either the primary or secondary owner of the account. Use conditions like current user = primary owner or current user = secondary owner.
Configure the Access When Rule:
Open the Account case type.
Go to the Security tab and in the Case Type rules, apply the created Access When rule to ensure that only users who meet the conditions (primary or secondary owners) can view or update the case. Apply Access Control:
In the Access Role configuration, apply the Access When rule for read and write instances of the Account class.
Ensure that the roles assigned to the users have the necessary permissions configured.
Testing and Validation:
Test the implementation by logging in with users who are primary or secondary owners and verifying access.
Try logging in with users who are not owners to ensure access is denied.
Reference: Pega Academy: Security and Access Control.
Pega Documentation: Access Control Policies and Access When Rules.
Pega Express*" is a light, design-focused delivery approach that uses Pega’s low-code experience, best practices, and Scrum to quickly deliver meaningful outcomes.
Which two of the following statements best describe the so-called three pillars of the Pega Express delivery approach? (Choose Three)
- A . The three pillars define Personas and Channels, as Personas represent the access roles and privileges that are required in the Microjourney"*, and the channels represent the technology that the personas use to interact with the application.
- B . The three pillars define Cases and strategies, as cases define how to process the data, and strategy is about design pattern to design case that processes the Microjourney
- C . The three pillars define the Data and Interface, as Data objects replace case objects in the process of the Microjourney, and an interface is about the technology used to interact with the application.
- D . The three pillars define the Data and Interface, as a Data object is required in the process of the Microjourney, and an interface is required for integration with external systems.
- E . The three pillars define the Cases and Strategies, as cases define how to process the Microjourney, and strategy is about design pattern to process the Microjourney
- F . The three pillars define Personas and Channels, as Personas represent the people that are involved in the Microjourney, and the channels represent how personas interact with the application.
F A
Explanation:
Personas and Channels:
Personas represent the people involved in the Microjourney, defining access roles and privileges.
Channels represent how personas interact with the application, defining the technology used for these interactions.
Reference: Pega Express delivery approach focuses on designing and delivering outcomes quickly by defining key personas and the channels they use to interact with the application. Therefore, the correct answers are:
F. The three pillars define Personas and Channels, as Personas represent the people that are involved in the Microjourney, and the channels represent how personas interact with the application. A. The three pillars define Personas and Channels, as Personas represent the access roles and privileges that are required in the Microjourney, and the channels represent the technology that the personas use to interact with the application.
You review and tune the agent configuration on a production system since some default agents____________ and ____________. (choose two)
- A . Are not necessary for every application.
- B . require an agent schedule record
- C . Should never run in a production environment.
- D . need to be registered with the master agent
A, C
Explanation:
When tuning the agent configuration on a production system, it is important to review and adjust default agents because:
Not Necessary for Every Application: Some default agents are not necessary for every application and can be disabled to improve performance.
Should Never Run in a Production Environment: Certain agents are intended for development or testing environments and should not be active in production to avoid unnecessary processing and potential security risks.
Reference: Pega Agent Configuration Guidelines: Agent Configuration
To access a property from an unconnected component, you use the______________.
- A . customer-dot-property construct
- B . property value
- C . dot-property value directly
- D . component-dot-property construct
D
Explanation:
In Pega, to access a property from an unconnected component within a decision strategy, you use the component-dot-property construct.
This construct allows you to reference properties of other components within the strategy, ensuring that all necessary data is accessible for decision-making.
