Practice Free NSE8_812 Exam Online Questions
Refer to the exhibit showing the history logs from a FortiMail device.
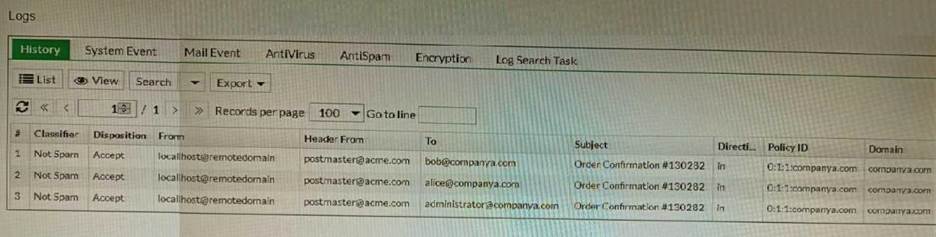
Which FortiMail email security feature can an administrator enable to treat these emails as spam?
- A . DKIM validation in a session profile
- B . Sender domain validation in a session profile
- C . Impersonation analysis in an antispam profile
- D . Soft fail SPF validation in an antispam profile
Refer to the exhibit containing the configuration snippets from the FortiGate.
Customer requirements:
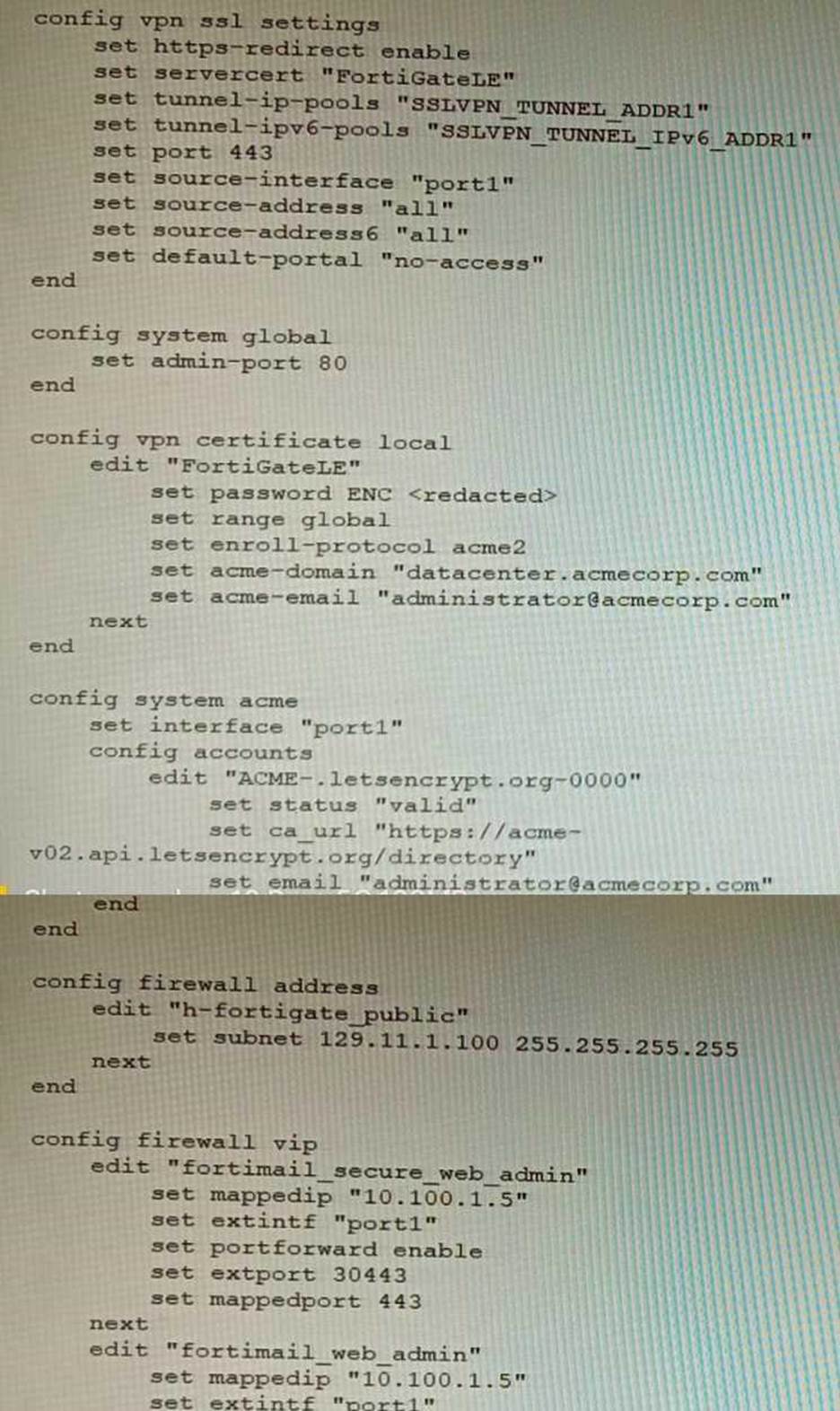
• SSLVPN Portal must be accessible on standard HTTPS port (TCP/443)
• Public IP address (129.11.1.100) is assigned to portl
• Datacenter.acmecorp.com resolves to the public IP address assigned to portl
The customer has a Let’s Encrypt certificate that is going to expire soon and it reports that subsequent attempts to renew that certificate are failing.
Reviewing the requirement and the exhibit, which configuration change below will resolve this issue?
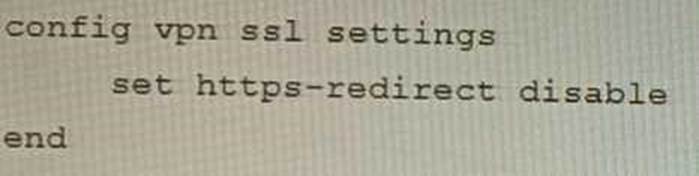
A)
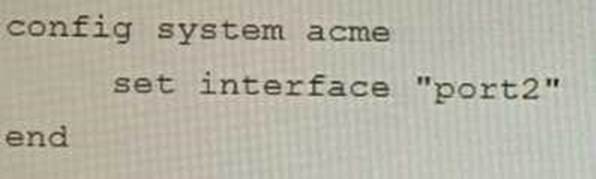
B)
C)
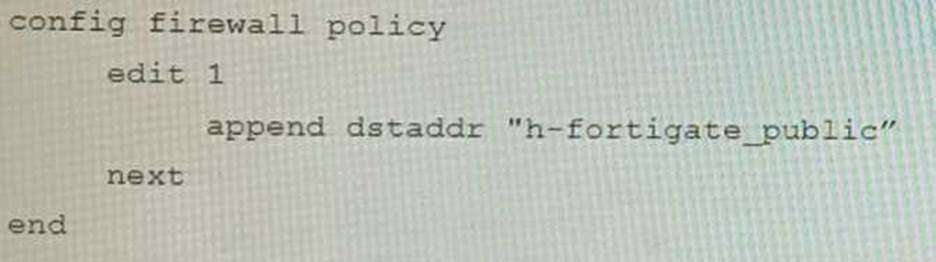
D)
- A . Option A
- B . Option B
- C . Option C
- D . Option D
Refer to the exhibit.
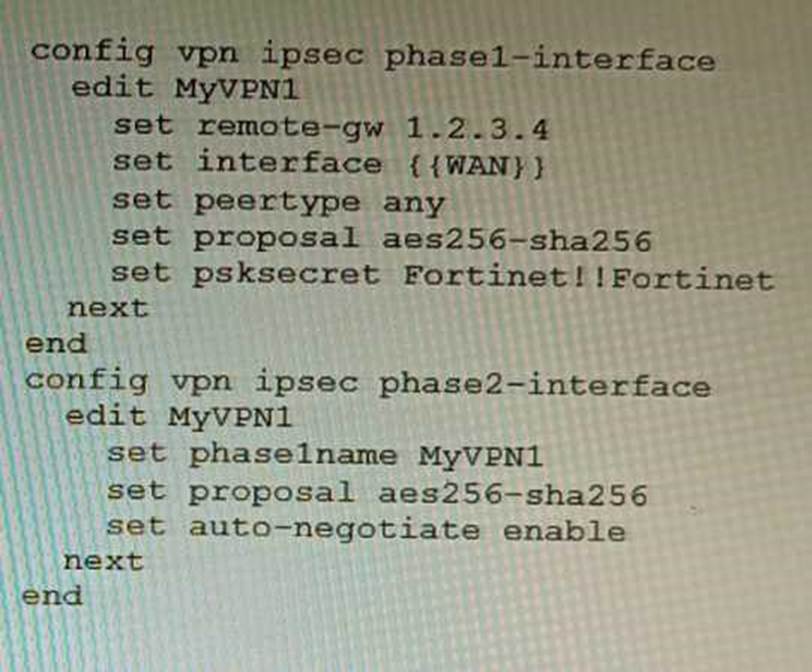
FortiManager is configured with the Jinja Script under CLI Templates shown in the exhibit.
Which two statements correctly describe the expected behavior when running this template? (Choose two.)
- A . The Jinja template will automatically map the interface with "WAN" role on the managed FortiGate.
- B . The template will work if you change the variable format to $(WAN).
- C . The template will work if you change the variable format to {{ WAN }}.
- D . The administrator must first manually map the interface for each device with a meta field.
- E . The template will fail because this configuration can only be applied with a CLI or TCL script.
Refer to the exhibit.

FortiManager is configured with the Jinja Script under CLI Templates shown in the exhibit.
Which two statements correctly describe the expected behavior when running this template? (Choose two.)
- A . The Jinja template will automatically map the interface with "WAN" role on the managed FortiGate.
- B . The template will work if you change the variable format to $(WAN).
- C . The template will work if you change the variable format to {{ WAN }}.
- D . The administrator must first manually map the interface for each device with a meta field.
- E . The template will fail because this configuration can only be applied with a CLI or TCL script.
A customer is planning on moving their secondary data center to a cloud-based laaS. They want to place all the Oracle-based systems Oracle Cloud, while the other systems will be on Microsoft Azure with ExpressRoute service to their main data center.
They have about 200 branches with two internet services as their only WAN connections. As a security consultant you are asked to design an architecture using Fortinet products with security, redundancy and performance as a priority.
Which two design options are true based on these requirements? (Choose two.)
- A . Systems running on Azure will need to go through the main data center to access the services on Oracle Cloud.
- B . Use FortiGate VM for IPSEC over ExpressRoute, as traffic is not encrypted by Azure.
- C . Branch FortiGate devices must be configured as VPN clients for the branches’ internal network to be able to access Oracle services without using public IPs.
- D . Two ExpressRoute services to the main data center are required to implement SD-WAN between a FortiGate VM in Azure and a FortiGate device at the data center edge
You are running a diagnose command continuously as traffic flows through a platform with NP6 and you obtain the following output:
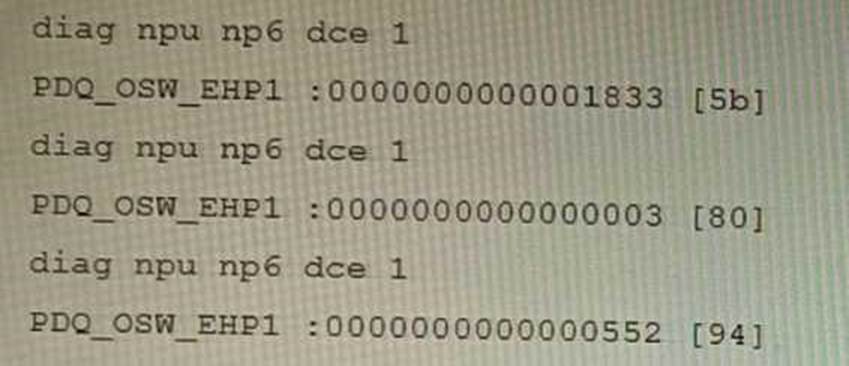
Given the information shown in the output, which two statements are true? (Choose two.)
- A . Enabling bandwidth control between the ISF and the NP will change the output
- B . The output is showing a packet descriptor queue accumulated counter
- C . Enable HPE shaper for the NP6 will change the output
- D . Host-shortcut mode is enabled.
- E . There are packet drops at the XAUI.
Refer to the exhibits.
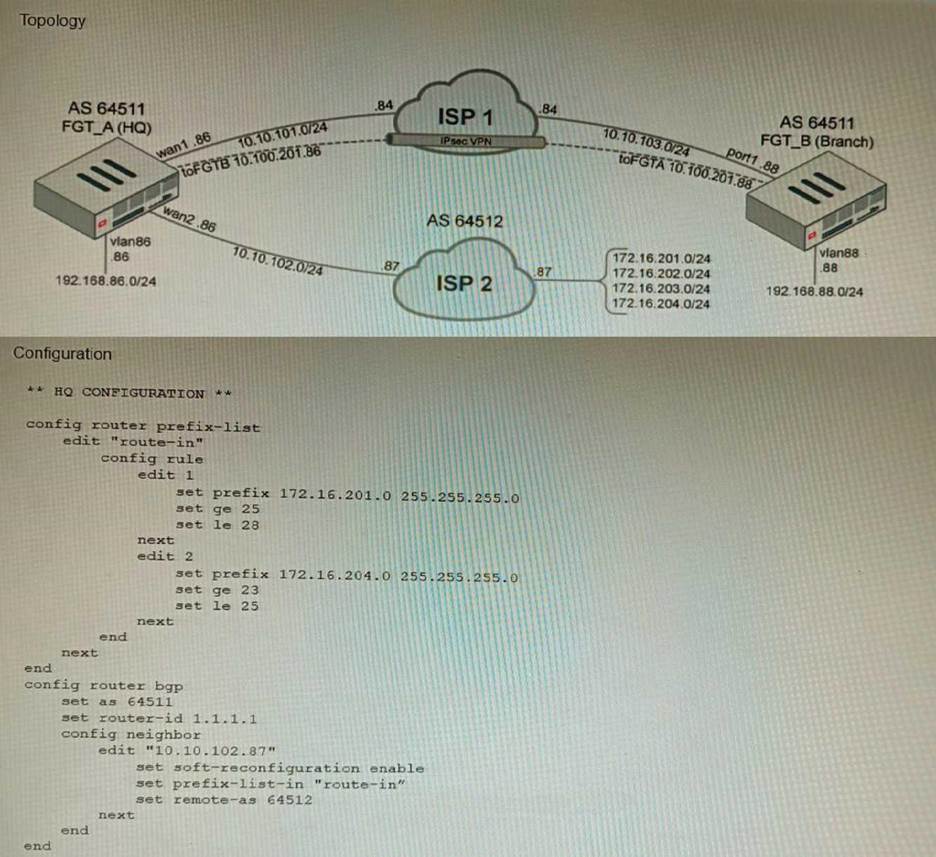
A customer has deployed a FortiGate with iBGP and eBGP routing enabled. HQ is receiving routes over eBGP from ISP 2; however, only certain routes are showing up in the routing table-Assume that BGP is working perfectly and that the only possible modifications to the routing table are solely due to the prefix list that is applied on HQ.
Given the exhibits, which two routes will be active in the routing table on the HQ firewall? (Choose two.)
- A . 172.16.204.128/25
- B . 172.16.201.96/29
- C . 172,620,64,27
- D . 172.16.204.64/27
An automation stitch was configured using an incoming webhook as the trigger named ‘my_incoming_webhook’.
The action is configured to execute the CLI Script shown:
A)
![]()
B)
![]()
C)
![]()
D)
![]()
- A . Option A
- B . Option B
- C . Option C
- D . Option D
Refer to the exhibit.
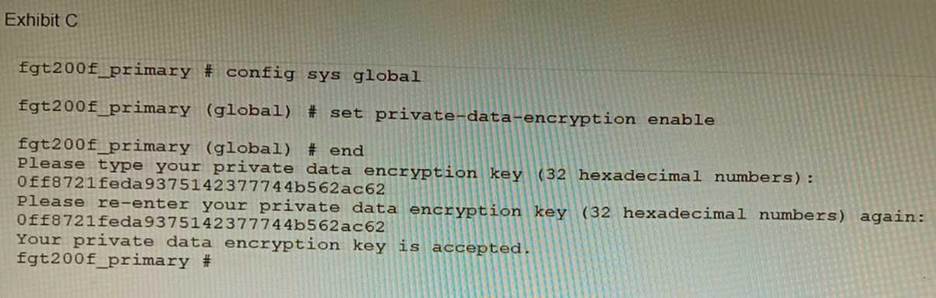
A customer has deployed a FortiGate 200F high-availability (HA) cluster that contains & TPM chip. The exhibit shows output from the FortiGate CLI session where the administrator enabled TPM. Following these actions, the administrator immediately notices that both FortiGate high availability (HA) status and FortiManager status for the FortiGate are negatively impacted.
What are the two reasons for this behavior? (Choose two.)
- A . The private-data-encryption key entered on the primary did not match the value that the TPM expected.
- B . Configuration for TPM is not synchronized between FortiGate HA cluster members.
- C . The FortiGate has not finished the auto-update process to synchronize the new configuration to FortiManager yet.
- D . TPM functionality is not yet compatible with FortiGate HA D The administrator needs to manually enter the hex private data encryption key in FortiManager
