Practice Free NSE7_SDW-7.2 Exam Online Questions
What are two advantages of using an IPsec recommended template to configure an IPsec tunnel in an hub-and-spoke topology? (Choose two.)
- A . It ensures consistent settings between phase1 and phase2.
- B . It guides the administrator to use Fortinet recommended settings.
- C . It automatically install IPsec tunnels to every spoke when they are added to the FortiManager ADOM.
- D . The VPN monitor tool provides additional statistics for tunnels defined with an IPsec recommended template.
AB
Explanation:
The use of an IPsec recommended template offers the advantage of ensuring consistent settings between phase1 and phase2 (A), which is essential for the stability and security of the IPsec tunnel. Additionally, it guides the administrator to use Fortinet’s recommended settings (B), which are designed to optimize performance and security based on Fortinet’s best practices.
Reference: The benefits of using IPsec recommended templates are outlined in Fortinet’s SD-WAN documentation, which emphasizes the importance of consistency and adherence to recommended configurations.
Refer to the exhibit.
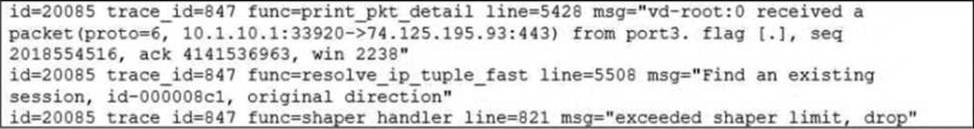
Which conclusion about the packet debug flow output is correct?
- A . The original traffic exceeded the maximum packets per second of the outgoing interface, and the packet was dropped.
- B . The reply traffic exceeded the maximum bandwidth configured in the traffic shaper, and the packet was dropped.
- C . The original traffic exceeded the maximum bandwidth of the outgoing interface, and the packet was dropped.
- D . The original traffic exceeded the maximum bandwidth configured in the traffic shaper, and the packet was dropped.
What is the route-tag setting in an SD-WAN rule used for?
- A . To indicate the routes for health check probes.
- B . To indicate the destination of a rule based on learned BGP prefixes.
- C . To indicate the routes that can be used for routing SD-WAN traffic.
- D . To indicate the members that can be used to route SD-WAN traffic.
Refer to the exhibit, which shows an SD-WAN zone configuration on the FortiGate GUI.
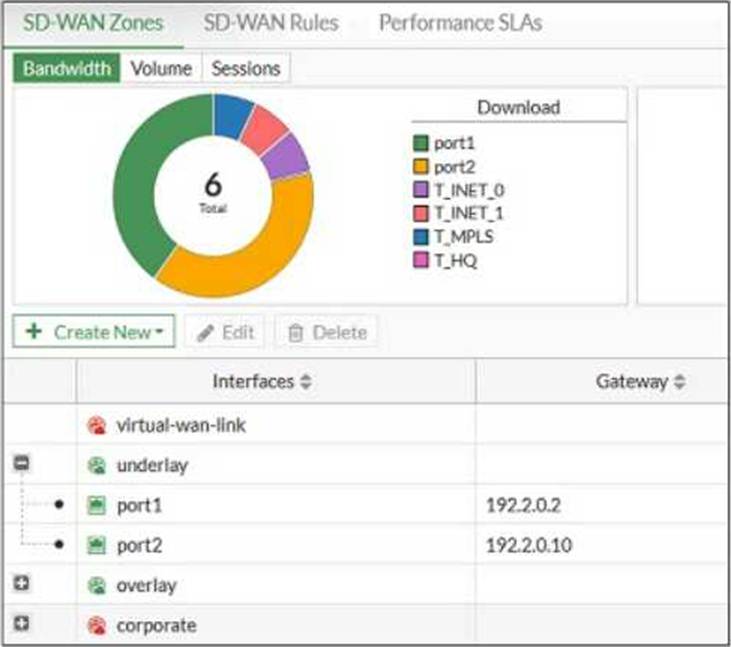
Based on the exhibit, which statement is true?
- A . You can delete the virtual-wan-link zone because it contains no member.
- B . The corporate zone contains no member.
- C . You can move port1 from the underlay zone to the overlay zone.
- D . The overlay zone contains four members.
B
Explanation:
Based on the exhibit, the "corporate" zone contains no member (B). In the FortiGate GUI, zones without members do not display any interfaces listed under them, which is the case for the corporate zone in the exhibit.
Reference: This conclusion is based on standard Fortinet GUI interpretation and the operational logic of SD-WAN zones as per Fortinet’s guidelines and user interface standards.
Which component is NOT part of Fortinet’s Secure SD-WAN solution?
- A . FortiManager
- B . FortiAnalyzer
- C . FortiSwitch
- D . FortiAP
Refer to the exhibit.
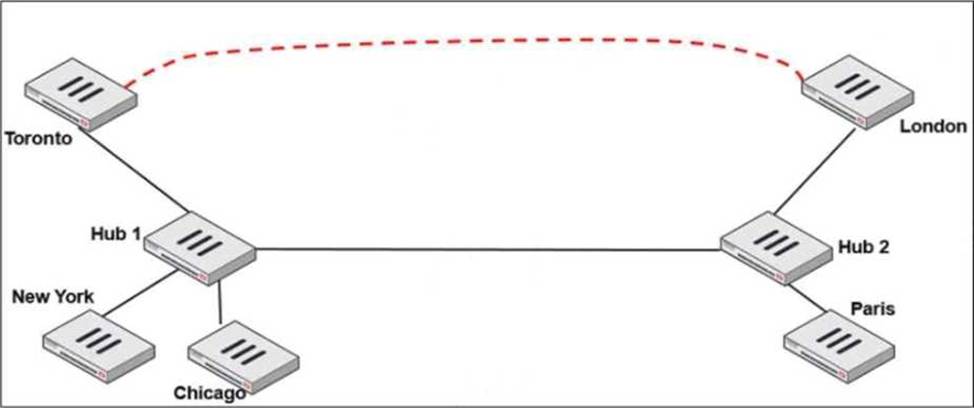
Two hub-and-spoke groups are connected through a site-to-site IPsec VPN between Hub 1 and Hub 2.
Which two configuration settings are required for Toronto and London spokes to establish an ADVPN
shortcut? (Choose two.)
- A . On the hubs, auto-discovery-sender must be enabled on the IPsec VPNs to spokes.
- B . On the spokes, auto-discovery-receiver must be enabled on the IPsec VPN to the hub.
- C . auto-discovery-forwarder must be enabled on all IPsec VPNs.
- D . On the hubs, net-device must be enabled on all IPsec VPNs.
Refer to the exhibits.
Exhibit A
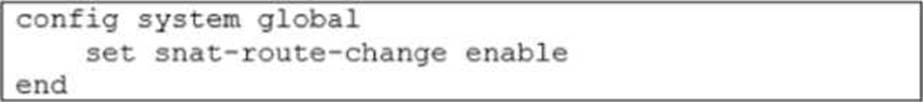
Exhibit B
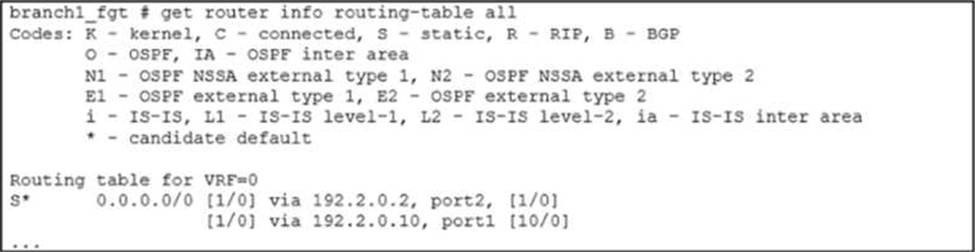
Exhibit A shows the source NAT (SNAT) global setting and exhibit B shows the routing table on FortiGate.
Based on the exhibits, which two actions does FortiGate perform on existing sessions established over port2, if the administrator increases the static route priority on port2 to 20? (Choose two.)
- A . FortiGate flags the sessions as dirty.
- B . FortiGate continues routing the sessions with no SNAT, over port2.
- C . FortiGate performs a route lookup for the original traffic only.
- D . FortiGate updates the gateway information of the sessions with SNAT so that they use port1 instead of port2.
What is the role of FortiController in the SD-WAN architecture?
- A . To serve as the primary router
- B . To manage SD-WAN rules and policies
- C . To monitor network health and analytics
- D . There is no component named FortiController in Fortinet’s SD-WAN solution.
In FortiGate SD-WAN, which feature ensures the confidentiality and integrity of data?
- A . IPSec VPN
- B . SSL inspection
- C . Antivirus
- D . Web filtering
Which FortiGate interface is used to configure SD-WAN members?
- A . WAN interface
- B . Internal interface
- C . Virtual interface
- D . Loopback interface
