Practice Free NSE7_PBC-7.2 Exam Online Questions
What kind of underlying mechanism does Transit Gateway Connect use to send traffic from the virtual private cloud (VPC) to the transit gateway?
- A . A BGP attachment
- B . A GRE attachment
- C . A transport attachment
- D . Transit Gateway Connect attachment
D
Explanation:
Transit Gateway Connect Specificity: AWS Transit Gateway Connect is a specific feature designed to streamline the integration of SD-WAN appliances and third-party virtual appliances into your Transit Gateway.expand_more It utilizes a specialized attachment type.exclamation
BGP’s Role: While Transit Gateway Connect attachments leverage BGP for dynamic routing, BGP itself is a routing protocol and not the core connectivity mechanism in this context.
GRE Tunneling: GRE is a tunneling protocol commonly used with Transit Gateway Connect attachments to encapsulate traffic.
You are adding more spoke VPCs to an existing hub and spoke topology Your goal is to finish this task in the minimum amount of time without making errors.
Which Amazon AWS services must you subscribe to accomplish your goal?
- A . GuardDuty, CloudWatch
- B . WAF, DynamoDB
- C . Inspector, S3
- D . CloudWatch, S3
D
Explanation:
The correct answer is D. CloudWatch and S3.
According to the GitHub repository for the Fortinet aws-lambda-tgw script1, this function requires the following AWS services:
CloudWatch: A monitoring and observability service that collects and processes events from various AWS resources, including Transit Gateway attachments and route tables.
S3: A scalable object storage service that can store the configuration files and logs generated by the Lambda function.
By using the Fortinet aws-lambda-tgw script, you can automate the creation and configuration of Transit Gateway Connect attachments for your FortiGate devices. This can help you save time and avoid errors when adding more spoke VPCs to an existing hub and spoke topology1.
The other AWS services mentioned in the options are not required for this task. GuardDuty is a threat detection service that monitors for malicious and unauthorized behavior to help protect AWS accounts and workloads. WAF is a web application firewall that helps protect web applications from common web exploits. Inspector is a security assessment service that helps improve the security and compliance of applications deployed on AWS. DynamoDB is a fast and flexible NoSQL database service that can store various types of data.
1: GitHub – fortinet/aws-lambda-tgw
You must allow an SSH traffic rule in an Amazon Web Services (AWS) network access list (NACL) to allow SSH traffic to travel to a subnet for temporary testing purposes. When you review the current inbound network ACL rules, you notice that rule number 5 demes SSH and telnet traffic to the subnet.
What can you do to allow SSH traffic?
- A . You must create a new allow SSH rule below rule number 5
- B . You must create a new allow SSH rule above rule number 5-
- C . You must create a new allow SSH rule anywhere in the network ACL rule base to allow SSH traffic.
- D . You do not have to create any NACL rules because the default security group rule automatically allows SSH traffic to the subnet.
B
Explanation:
Network ACLs are stateless, and they evaluate each packet separately based on the rules that you define. The rules are processed in order, starting with the lowest numbered rule1. If the traffic matches a rule, the rule is applied and no further rules are evaluated1. Therefore, if you want to allow SSH traffic to a subnet, you must create a new allow SSH rule above rule number 5, which denies SSH and telnet traffic. Otherwise, the deny rule will take precedence and block the SSH traffic.
The other options are incorrect because:
Creating a new allow SSH rule below rule number 5 will not allow SSH traffic, because the deny rule will be evaluated first and block the traffic.
Creating a new allow SSH rule anywhere in the network ACL rule base will not guarantee that SSH traffic will be allowed, because it depends on the order of the rules. If the allow SSH rule is below the deny rule, it will not be effective.
You cannot rely on the default security group rule to allow SSH traffic to the subnet, because network ACLs act as an additional layer of security for your VPC. Even if your security group allows SSH traffic, your network ACL must also allow it. Otherwise, the traffic will be blocked at the subnet level.
Which two Amazon Web Services (AWS) features support east-west traffic inspection within the AWS cloud by the FortiGate VM? (Choose two.)
- A . A NAT gateway with an EIP
- B . A transit gateway with an attachment
- C . An Internet gateway with an EIP
- D . A transit VPC
BD
Explanation:
The correct answer is B and D. A transit gateway with an attachment and a transit VPC support east-west traffic inspection within the AWS cloud by the FortiGate VM.
According to the Fortinet documentation for Public Cloud Security, a transit gateway is a network transit hub that connects VPCs and on-premises networks. A transit gateway attachment is a resource that connects a VPC or VPN to a transit gateway. By using a transit gateway with an attachment, you can route traffic from your spoke VPCs to your security VPC, where the FortiGate VM can inspect the traffic1.
A transit VPC is a VPC that serves as a global network transit center for connecting multiple VPCs, remote networks, and virtual private networks (VPNs). By using a transit VPC, you can deploy the FortiGate VM as a virtual appliance that provides network security and threat prevention for your VPCs2.
The other options are incorrect because:
A NAT gateway with an EIP is a service that enables instances in a private subnet to connect to the internet or other AWS services, but prevents the internet from initiating a connection with those instances. A NAT gateway with an EIP does not support east-west traffic inspection within the AWS cloud by the FortiGate VM3.
An Internet gateway with an EIP is a horizontally scaled, redundant, and highly available VPC component that allows communication between instances in your VPC and the internet. An Internet gateway with an EIP does not support east-west traffic inspection within the AWS cloud by the FortiGate VM4.
1: Fortinet Documentation Library – Deploying FortiGate VMs on AWS 2: [Fortinet Documentation Library – Transit VPC on AWS] 3: [NAT Gateways – Amazon Virtual Private Cloud] 4: [Internet Gateways – Amazon Virtual Private Cloud]
An administrator is looking for a solution that can provide insight into users and data stored in major SaaS applications in the multicloud environment.
Which product should the administrator deploy to have secure access to SaaS applications?
- A . FortiProxy
- B . FortiSandbox
- C . ForliCASB
- D . FortiWeb
C
Explanation:
For administrators seeking to gain insights into user activities and data within major SaaS applications across multicloud environments, deploying FortiCASB (Cloud Access Security Broker) is the most effective solution (Option C).
Role of FortiCASB: FortiCASB is specifically designed to provide security visibility, compliance, data security, and threat protection for cloud-based services. It acts as a mediator between users and cloud service providers, offering deep visibility into the operations and data handled by SaaS applications.
Capabilities of FortiCASB: This product enables administrators to monitor and control the access and usage of SaaS applications. It helps in assessing security configurations, tracking user activities, and evaluating data movement across the cloud services. By doing so, it assists organizations in enforcing security policies, detecting anomalous behaviors, and ensuring compliance with regulatory standards.
Integration and Functionality: FortiCASB integrates seamlessly with major SaaS platforms, providing a centralized management interface that allows for comprehensive analysis and real-time protection measures. This integration ensures that organizations can maintain control over their data across various cloud services, enhancing the overall security posture in a multicloud environment.
Reference: Fortinet’s official documentation on FortiCASB details its functionalities and integration capabilities with SaaS applications, highlighting its role in providing enhanced security measures for cloud-based services.
Your goal is to deploy resources in multiple places and regions in the public cloud using Terraform.
What is the most efficient way to deploy resources without changing much of the Terraform code?
- A . Use multiple terraform.tfvars files With a variables.tf file.
- B . Use the provider. tf file to add all the new values
- C . Install and configure two Terraform staging servers to deploy resources.
- D . Use the variable, tf file and edit its values to match multiple resources
A
Explanation:
When deploying resources in multiple places and regions in the public cloud using Terraform, the most efficient way is:
How does Terraform keep track of provisioned resources?
- A . It uses the terraform. tf state file
- B . Terraform does not keep the state of resources created
- C . It uses the terraform. tfvars file.
- D . It uses the database. tf file.
A
Explanation:
Terraform manages and tracks the state of infrastructure resources through a file known as terraform.tfstate. This file is automatically created by Terraform and is updated after the application of a Terraform plan to capture the current state of the resources.
State File Purpose: The terraform.tfstate file contains a JSON object that records the IDs and properties of resources Terraform manages, so that it can map real-world resources to your configuration, keep track of metadata, and improve performance for large infrastructures.
State File Management: This file is crucial for Terraform to perform resource updates, deletions, and for creating dependencies. It’s essentially the ‘source of truth’ for Terraform about your managed infrastructure and services.
Reference: This behavior is documented in Terraform’s official documentation, which explains how the terraform.tfstate file is used to keep track of the infrastructure Terraform is managing.
Refer to Exhibit:
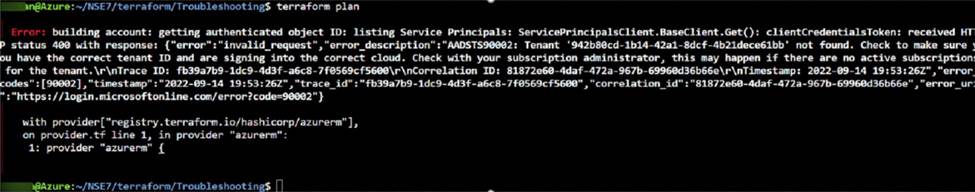
After the initial Terraform configuration in Microsoft Azure, the terraform plan command is run.
Which two statements about running the plan command are true? (Choose two.)
- A . The terraform plan command will deploy the rest of the resources except the service principle details.
- B . You cannot run the terraform apply command before the terraform plan command.
- C . You must run the terraform init command once, before the terraform plan command
- D . The terraform plan command makes terraform do a dry run.
CD
Explanation:
A is incorrect because the terraform plan command will not deploy any resources at all. It will only show the changes that would be made if the terraform apply command was run. The error message in the exhibit indicates that the service principal details are invalid, which means that Terraform cannot authenticate to Azure and cannot create any resources1.
B is incorrect because you can run the terraform apply command without running the terraform plan command first. The terraform apply command will automatically generate a new plan and prompt you to approve it before applying it2. However, running the terraform plan command first can help you preview the changes and avoid any unwanted or unexpected actions.
C is correct because you must run the terraform init command once before the terraform plan command. The terraform init command initializes a working directory containing Terraform configuration files. It downloads and installs the provider plugins required for your configuration, such as the Azure provider2. It also creates a hidden directory called .terraform to store the plugin binaries and other metadata1. Without running the terraform init command, the terraform plan command will fail because it cannot find the required plugins or modules.
D is correct because the terraform plan command makes Terraform do a dry run. A dry run is a simulation of what would happen if you executed a certain action, without actually performing it. The terraform plan command creates an execution plan, which is a description of the actions that Terraform would take to make your infrastructure match your configuration2. The execution plan shows you what resources will be created, modified, or destroyed, and what attributes will be changed. The execution plan does not affect your infrastructure or state file until you apply it with the terraform apply command1.
