Practice Free NSE7_OTS-7.2 Exam Online Questions
What are two critical tasks the OT network auditors must perform during OT network risk assessment and management? (Choose two.)
- A . Planning a threat hunting strategy
- B . Implementing strategies to automatically bring PLCs offline
- C . Creating disaster recovery plans to switch operations to a backup plant
- D . Evaluating what can go wrong before it happens
When device profiling rules are enabled, which devices connected on the network are evaluated by the device profiling rules?
- A . Known trusted devices, each time they change location
- B . All connected devices, each time they connect
- C . Rogue devices, only when they connect for the first time
- D . Rogue devices, each time they connect
As an OT network administrator, you are managing three FortiGate devices that each protect different levels on the Purdue model. To increase traffic visibility, you are required to implement additional security measures to detect exploits that affect PLCs.
Which security sensor must implement to detect these types of industrial exploits?
- A . Intrusion prevention system (IPS)
- B . Deep packet inspection (DPI)
- C . Antivirus inspection
- D . Application control
In a wireless network integration, how does FortiNAC obtain connecting MAC address information?
- A . RADIUS
- B . Link traps
- C . End station traffic monitoring
- D . MAC notification traps
A
Explanation:
FortiNAC can integrate with RADIUS servers to obtain MAC address information for wireless clients that authenticate through the RADIUS server.
Reference: Fortinet NSE 7 – OT Security 6.4 Study Guide, Chapter 4: OT Security Devices, page 4-28.
Refer to the exhibit.
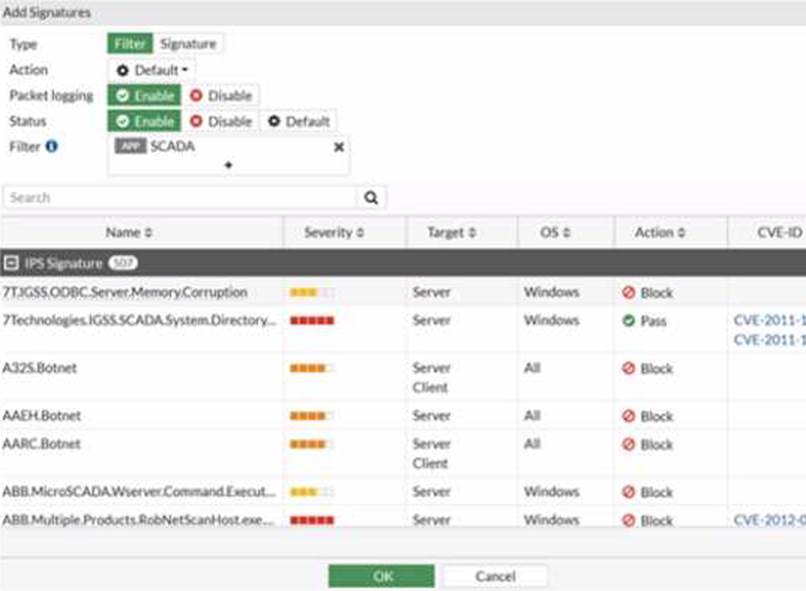
The IPS profile is added on all of the security policies on FortiGate.
For an OT network, which statement of the IPS profile is true?
- A . FortiGate has no IPS industrial signature database enabled.
- B . The listed IPS signatures are classified as SCADAapphcat nns
- C . All IPS signatures are overridden and must block traffic match signature patterns.
- D . The IPS profile inspects only traffic originating from SCADA equipment.
An OT network architect must deploy a solution to protect fuel pumps in an industrial remote network. All the fuel pumps must be closely monitored from the corporate network for any temperature fluctuations.
How can the OT network architect achieve this goal?
- A . Configure a fuel server on the remote network, and deploy a FortiSIEM with a single pattern temperature security rule on the corporate network.
- B . Configure a fuel server on the corporate network, and deploy a FortiSIEM with a single pattern temperature performance rule on the remote network.
- C . Configure a fuel server on the remote network, and deploy a FortiSIEM with a single pattern temperature performance rule on the corporate network.
- D . Configure both fuel server and FortiSIEM with a single-pattern temperature performance rule on the corporate network.
C
Explanation:
This way, FortiSIEM can discover and monitor everything attached to the remote network and provide security visibility to the corporate network
FortiAnalyzer is implemented in the OT network to receive logs from responsible FortiGate devices.
The logs must be processed by FortiAnalyzer.
In this scenario, which statement is correct about the purpose of FortiAnalyzer receiving and processing multiple log messages from a given PLC or RTU?
- A . To isolate PLCs or RTUs in the event of external attacks
- B . To configure event handlers and take further action on FortiGate
- C . To determine which type of messages from the PLC or RTU causes issues in the plant
- D . To help OT administrators configure the network and prevent breaches
An OT supervisor has configured LDAP and FSSO for the authentication. The goal is that all the users be authenticated against passive authentication first and, if passive authentication is not successful, then users should be challenged with active authentication.
What should the OT supervisor do to achieve this on FortiGate?
- A . Configure a firewall policy with LDAP users and place it on the top of list of firewall policies.
- B . Enable two-factor authentication with FSSO.
- C . Configure a firewall policy with FSSO users and place it on the top of list of firewall policies.
- D . Under config user settings configure set auth-on-demand implicit.
C
Explanation:
The OT supervisor should configure a firewall policy with FSSO users and place it on the top of list of
firewall policies in order to achieve the goal of authenticating users against passive authentication first and, if passive authentication is not successful, then challenging them with active authentication.
Which two statements about the Modbus protocol are true? (Choose two.)
- A . Modbus uses UDP frames to transport MBAP and function codes.
- B . Most of the PLC brands come with a built-in Modbus module.
- C . You can implement Modbus networking settings on internetworking devices.
- D . Modbus is used to establish communication between intelligent devices.
