Practice Free NSE6_FSR-7.3 Exam Online Questions
What are two different services that you can configure for monitoring system and cluster health statuses on FortiSOAR? (Choose two.)
- A . Exchange
- B . POP
- C . IMAP
- D . SMTP
What is the purpose of audit logs in FortiSOAR?
- A . To track system errors and warnings only
- B . To monitor user activities and system changes
- C . To record network traffic
- D . To keep a log of emails sent by the system
When analyzing FortiSOAR log files, what information is crucial for identifying workflow execution problems? (Choose two)
- A . Timestamps
- B . User login attempts
- C . Execution IDs
- D . CPU usage at the time of execution
When identifying deployment requirements for SOC and SOAR, what is a crucial factor to ensure effective data correlation?
- A . Selecting a platform based solely on its popularity
- B . Ensuring the solution can integrate and correlate data from various sources
- C . Implementing the most visually appealing user interface
- D . Choosing a solution based entirely on its cost-effectiveness
Role-Based Access Control (RBAC) limits system access to authorized users.
What does RBAC primarily manage?
- A . The physical access to buildings
- B . Permissions based on user roles
- C . Internet bandwidth per user
- D . The number of logins per user
View the exhibit.
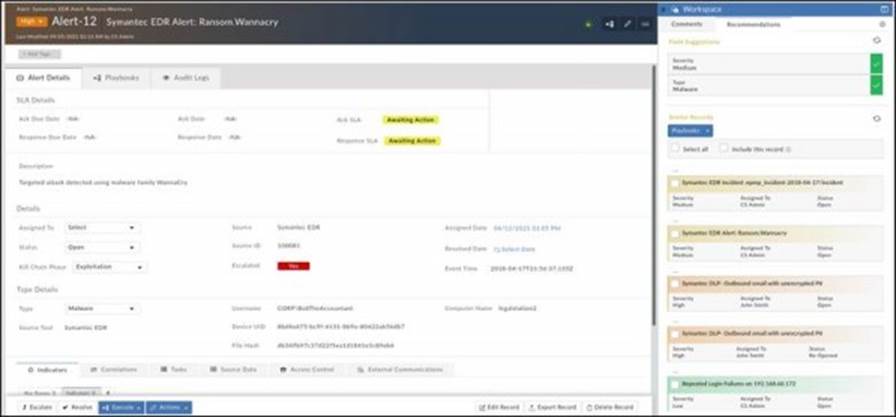
The dataset on FortiSOAR has been trained to predict which record field?
- A . Assigned To
- B . Status
- C . Playbooks
- D . Severity
Differentiating between appliance authentication and user authentication is crucial.
Which of the following best describes appliance authentication?
- A . Authentication of a user’s personal device
- B . Authentication involving the verification of network devices and servers
- C . Verification of user identity through passwords or biometrics
- D . Authentication of software applications
________ authentication is primarily concerned with verifying the identity of individuals attempting to access the system.
- A . Server
- B . Network
- C . User
- D . Device
How can administrators export FortiSOAR system configuration?
- A . Through command line interface only
- B . Via the System Configuration section under Administration
- C . By manually copying configuration files
- D . System configuration cannot be exported
What is a key feature of system fixtures in FortiSOAR?
- A . They are used for hardware diagnostics.
- B . They allow for the customization of dashboards.
- C . They enable the export and import of predefined configurations.
- D . They provide encryption for data at rest.
