Practice Free NSE6_FNC-7.2 Exam Online Questions
Question #11
Which three are components of a security rule? (Choose three.)
- A . Methods
- B . Security String
- C . Trigger
- D . User or host profile
- E . Action
Question #12
Where should you configure MAC notification traps on a supported switch?
- A . Configure them only after you configure linkup and linkdown traps.
- B . Configure them on all ports on the switch.
- C . Configure them only on ports set as 802 1g trunks.
- D . Configure them on all ports except uplink ports.
Question #13
Which connecting endpoints are evaluated against all enabled device profiling rules?
- A . All hosts, each time they connect
- B . Rogues devices, only when they connect for the first time
- C . Known trusted devices each time they change location
- D . Rogues devices, each time they connect
Question #14
View the command and output shown in the exhibit.
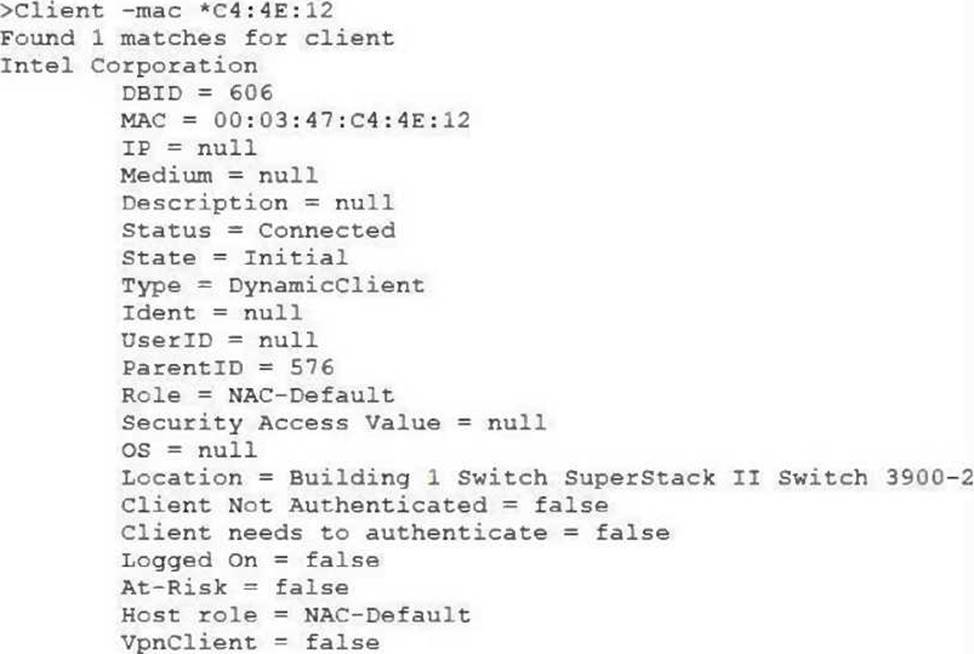
What is the current state of this host?
- A . Rogue
- B . Registered
- C . Not authenticated
- D . At-Risk
Question #15
By default, if after a successful Layer 2 poll, more than 20 endpoints are seen connected on a single switch port simultaneously, what happens to the port?
- A . The port becomes a threshold uplink
- B . The port is disabled
- C . The port is added to the Forced Registration group
- D . The port is switched into the Dead-End VLAN
Question #16
In a wireless integration, what method does FortiNAC use to obtain connecting MAC address information?
- A . SNMP traps
- B . RADIUS
- C . Endstation traffic monitoring
D Link traps
1 2
