Practice Free NSE6_FAZ-7.2 Exam Online Questions
Refer to the exhibit.
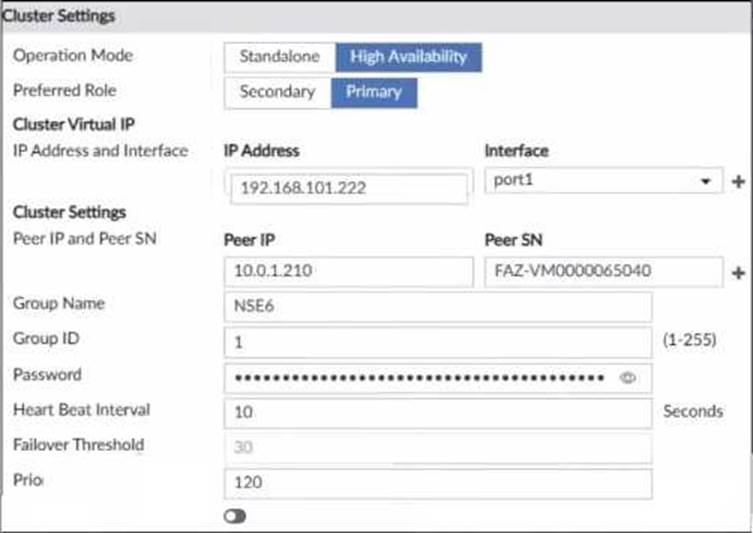
The image displays "he configuration of a FortiAnalyzer the administrator wants to join to an existing HA cluster.
What can you conclude from the configuration displayed?
- A . After joining to the cluster, this FortiAnalyzer will keep an updated log database.
- B . This FortiAnalyzer will trigger a failover after losing communication with its peers for 10 seconds.
- C . This FortiAnalyzer will join to the existing HA cluster as the primary.
- D . This FortiAnalyzer is configured to receive logs in its port1.
D
Explanation:
The configuration displayed in the exhibit indicates that the FortiAnalyzer is set up with a cluster virtual IP address of 192.168.101.222 assigned to interface port1. This setup is typically used for the FortiAnalyzer to receive logs on that interface when operating in a High Availability (HA) configuration. The exhibit does not provide enough information to conclude whether this FortiAnalyzer will be the primary unit in the HA cluster or the duration for the failover trigger; it only confirms the interface configuration for log reception.
Reference: Based on the FortiAnalyzer 7.4.1 Administration Guide, the similar configurations for HA and log reception are discussed, which would be relevant for understanding the settings in FortiAnalyzer 7.2.
Which two statements are true regarding FortiAnalyzer system backups? (Choose two.)
- A . Existing reports can be included in the backup files.
- B . The system reserves at least 5% to 20% disk space for backup files.
- C . Scheduled system backups can be configured only from the CLI.
- D . Backup files can be uploaded to SCP and SFTP servers.
AD
Explanation:
FortiAnalyzer allows for the inclusion of existing reports in the backup files, providing a comprehensive backup of configurations and data. Additionally, the backup files can be configured to be uploaded to SCP and SFTP servers, ensuring secure transfer and offsite storage of backup data. This can be configured both in the GUI and the CLI, providing flexibility in how backups are scheduled and managed.
Reference: FortiAnalyzer 7.4.1 Administration Guide, "Scheduling automatic backups" section.
An administrator has configured the following settings:

What is the purpose of executing these commands?
- A . To record the hash value and authentication code of log files.
- B . To encrypt log transfer between FortiAnalyzer and other devices.
- C . To verify the integrity of the log files received.
- D . To create the secure channel used by the OFTP process.
C
Explanation:
The purpose of executing the provided CLI commands, which include setting the log-checksum to md5-auth, is to ensure the integrity of the log files. This setting is used to record the MD5 hash value of log files, which is a widely used cryptographic hash function that produces a 128-bit (16-byte) hash value. By using MD5 authentication, FortiAnalyzer ensures that the log files have not been altered or tampered with during transit, thereby verifying their integrity upon receipt. This is not related to encrypting log transfers, scheduling reports, or creating secure channels for OFTP (Over-the-FortiGate Protocol) processes.
What is true about a FortiAnalyzer Fabric?
- A . Supervisors support HA.
- B . Members events can be raised from the supervisor.
- C . The supervisor and members cannot be in different time zones
- D . The members send their logs to the supervisor.
D
Explanation:
In a FortiAnalyzer Fabric, the FortiAnalyzer can recognize a Security Fabric group of devices, and it supports the Security Fabric by storing and analyzing logs from these units as if they were from a single device. The members of the Security Fabric group send their logs to the FortiAnalyzer, which acts as a supervisor for log storage and analysis, providing a centralized point of visibility and control over the logs.
Reference: FortiAnalyzer 7.4.1 Administration Guide, "Security Fabric" section.
Which statement is true when you are upgrading the firmware on an HA cluster made up of throe
FortiAnalyzer devices?
- A . All FortiAnalyzer devices will be upgraded at the same time.
- B . Enabling uninterruptible-upgrade prevents normal operations from being interrupted during the upgrade.
- C . You can perform the firmware upgrade using only a console connection.
- D . First, upgrade the secondary devices, and then upgrade the primary device.
D
Explanation:
In an HA cluster, the firmware upgrade process involves upgrading the secondary devices first. This approach ensures that the primary device can continue to handle traffic and maintain the operational stability of the network while the secondary devices are being upgraded. Once the secondary devices have successfully upgraded their firmware and are operational, the primary device can then be upgraded. This method minimizes downtime and maintains network integrity during the upgrade process.
When upgrading firmware in a High Availability (HA) cluster of FortiAnalyzer units, the recommended practice is to first upgrade the secondary devices before upgrading the primary device. This approach ensures that the primary device, which coordinates the cluster’s operations, remains functional for as long as possible, minimizing the impact on log collection and analysis. Once the secondary devices are successfully upgraded and operational, the primary device can be upgraded, ensuring a smooth transition and maintaining continuous operation of the cluster.
Reference: FortiAnalyzer 7.2 Administrator Guide – "System Administration" and "High Availability" sections.
Which statement is true about the communication between FortiGate high availability (HA) clusters and FortiAnalyzer?
- A . Each cluster member sends its logs directly to FortiAnalyzer.
- B . You must add the device lo the cluster first, and then registers the cluster with FortiAnalyzer.
- C . FortiAnalyzer distinguishes each cluster member by its MAC address.
- D . Only the primary device in the cluster communicates with FortiAnalyzer.
D
Explanation:
In a FortiGate high availability (HA) cluster, only the primary device sends its logs to the FortiAnalyzer. This is to ensure that logs are not duplicated between the primary and secondary devices in the cluster. The configuration of the FortiAnalyzer server on the FortiGate is such that the HA primary device is set as the server that forwards the logs.
Reference: FortiAnalyzer 7.4.1 Administration Guide, sections mentioning HA cluster configuration and log forwarding.
Which statement is true about using aggregation mode on FortiAnalyzer?
- A . Aggregation mode supports log filters.
- B . Aggregation mode can work with syslog servers.
- C . In aggregation mode, logs and content files are forwarded in real time.
- D . Aggregation mode can be configured only on the CLI.
B
Explanation:
In aggregation mode, FortiAnalyzer stores logs received from devices and forwards them at a specified time each day to avoid duplication. It is specifically designed to work between two FortiAnalyzer units and does not support syslog or CEF servers. Additionally, aggregation mode configurations are limited to CLI commands log-forward and log-forward-service.
Reference: FortiAnalyzer 7.2 Administrator Guide, "Aggregation" and "CLI Commands for Aggregation Mode" sections.
Refer to the exhibit.
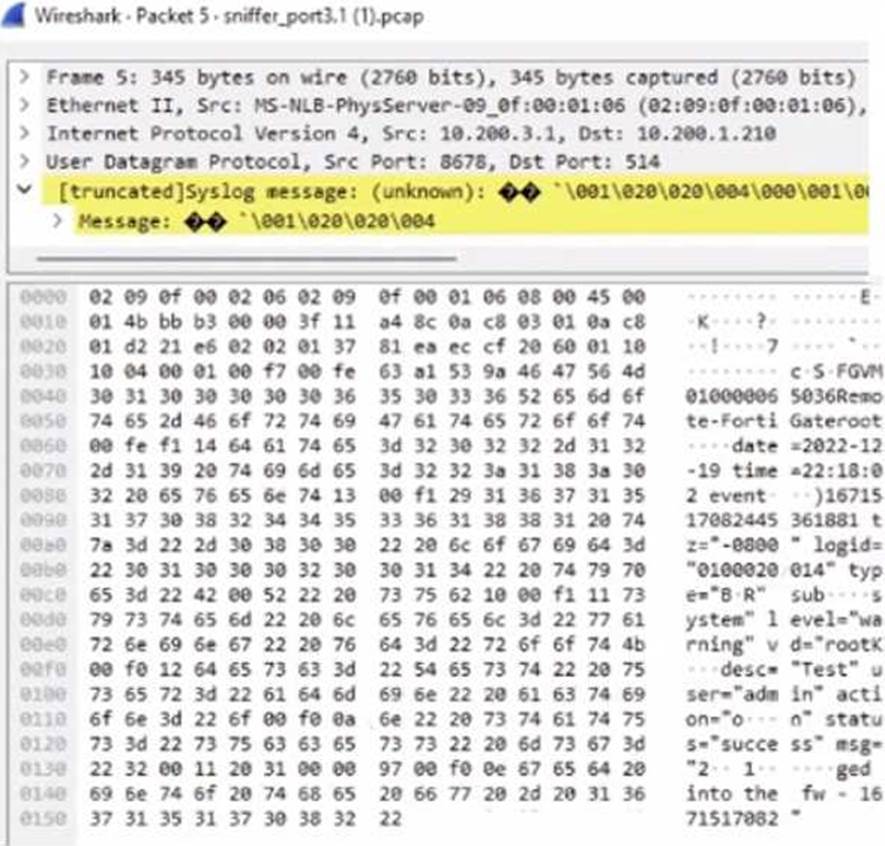
Which image corresponds to the packet capture shown in the exhibit?
A)
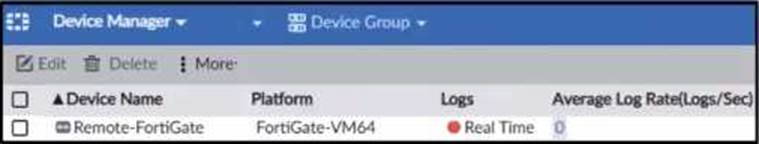
B)
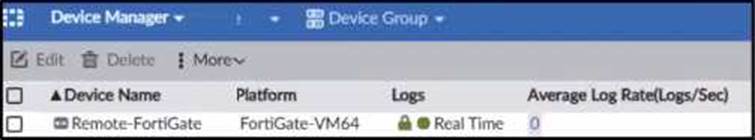
C)
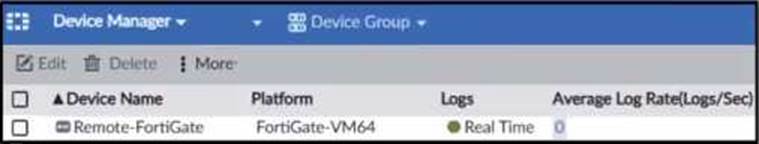
- A . Option A
- B . Option B
- C . Option C
A
Explanation:
The exhibit shows a packet capture with a syslog message containing a log event from a FortiGate device. This log event includes several details such as the date, time, and event message. The corresponding image that matches this packet capture would be the one which shows that the FortiGate device has logs being received in real-time, as indicated by the highlighted section in the packet capture where it mentions "real-time". Therefore, Option A is the correct answer because it shows logs with "Real Time" status for the FortiGate-VM64 device, indicating that this FortiAnalyzer is currently receiving real-time logs from the device, matching the activity in the packet capture.
Reference: Based on the provided exhibits and the real-time logging information, correlated with the knowledge from the FortiAnalyzer 7.2 Administrator documentation regarding log reception and device management.
A rogue administrator was accessing FortiAnalyzer without permission.
Where can you view the activities that the rogue administrator performed on FortiAnalyzer?
- A . FortiView
- B . Fabric View
- C . Log View
- D . System Settings
A
Explanation:
To monitor the activities performed by any administrator, including a rogue one, on the FortiAnalyzer, you should use the FortiView feature. FortiView provides a comprehensive overview of the activities and events happening within the FortiAnalyzer environment, including administrator actions, making it the appropriate tool for tracking unauthorized or suspicious activities.
Reference: FortiAnalyzer 7.4.1 Administration Guide, "System Settings > Fabric Management" section.
