Practice Free NSE5_EDR-5.0 Exam Online Questions
What is the purpose of the Threat Hunting feature?
- A . Delete any file from any collector in the organization
- B . Find and delete all instances of a known malicious file or hash in the organization
- C . Identify all instances of a known malicious file or hash and notify affected users
- D . Execute playbooks to isolate affected collectors in the organization
What is true about classifications assigned by Fortinet Cloud Sen/ice (FCS)?
- A . The core is responsible for all classifications if FCS playbooks are disabled
- B . The core only assigns a classification if FCS is not available
- C . FCS revises the classification of the core based on its database
- D . FCS is responsible for all classifications
Refer to the exhibit.
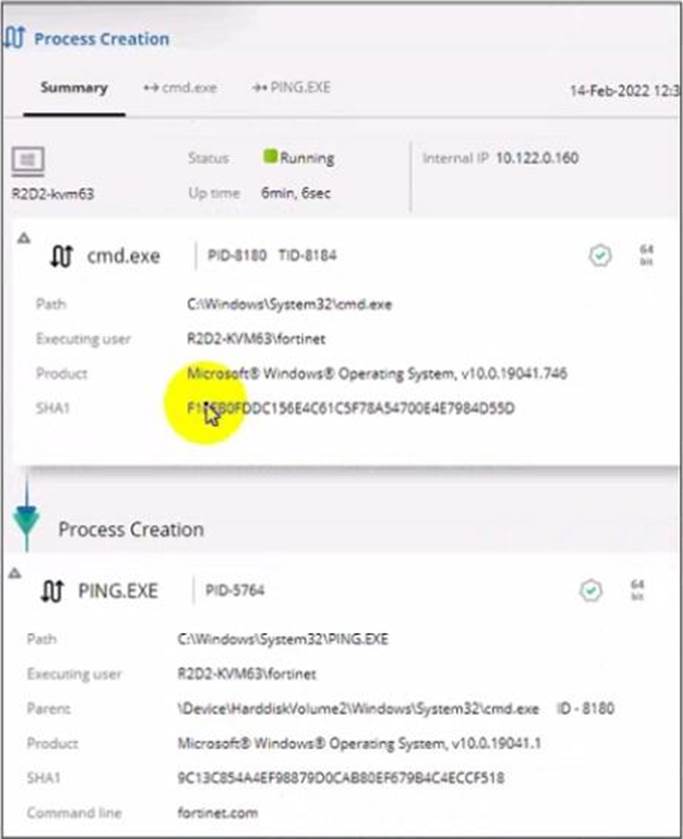
Based on the threat hunting event details shown in the exhibit, which two statements about the event are true? (Choose two.)
- A . The PING EXE process was blocked
- B . The user fortinet has executed a ping command
- C . The activity event is associated with the file action
- D . There are no MITRE details available for this event
An administrator finds a third party free software on a user’s computer mat does not appear in me application list in the communication control console
Which two statements are true about this situation? (Choose two)
- A . The application is allowed in all communication control policies
- B . The application is ignored as the reputation score is acceptable by the security policy
- C . The application has not made any connection attempts
- D . The application is blocked by the security policies
Which two types of remote authentication does the FortiEDR management console support? (Choose two.)
- A . Radius
- B . SAML
- C . TACACS
- D . LDAP
How does FortiEDR implement post-infection protection?
- A . By preventing data exfiltration or encryption even after a breach occurs
- B . By using methods used by traditional EDR
- C . By insurance against ransomware
- D . By real-time filtering to prevent malware from executing
Refer to the exhibit.
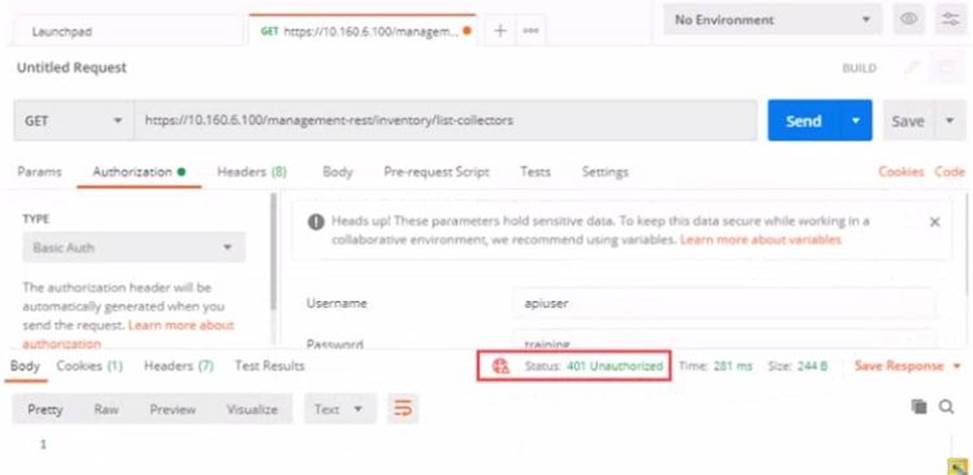
Based on the postman output shown in the exhibit why is the user getting an unauthorized error?
- A . The user has been assigned Admin and Rest API roles
- B . FortiEDR requires a password reset the first time a user logs in
- C . Postman cannot reach the central manager
- D . API access is disabled on the central manager
Which threat hunting profile is the most resource intensive?
- A . Comprehensive
- B . Inventory
- C . Default
- D . Standard Collection
What is the role of a collector in the communication control policy?
- A . A collector blocks unsafe applications from running
- B . A collector is used to change the reputation score of any application that collector runs
- C . A collector records applications that communicate externally
- D . A collector can quarantine unsafe applications from communicating
