Practice Free N10-009 Exam Online Questions
A network technician is troubleshooting network latency and has determined the issue to be occurring two network switches (Switch10 and Switch11). Symptoms reported included poor video performance and slow file copying.
Given the following information:
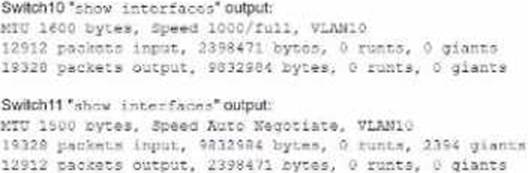
Which of the following should the technician most likely do to resolve the issue?
- A . Disable automatic negotiation on Switch11.
- B . Modify Switch10 MTU value to 1500.
- C . Configure STP on both switches.
- D . Change the native VLAN on the ports.
A network technician is troubleshooting network latency and has determined the issue to be occurring two network switches (Switch10 and Switch11). Symptoms reported included poor video performance and slow file copying.
Given the following information:

Which of the following should the technician most likely do to resolve the issue?
- A . Disable automatic negotiation on Switch11.
- B . Modify Switch10 MTU value to 1500.
- C . Configure STP on both switches.
- D . Change the native VLAN on the ports.
A network technician is troubleshooting network latency and has determined the issue to be occurring two network switches (Switch10 and Switch11). Symptoms reported included poor video performance and slow file copying.
Given the following information:

Which of the following should the technician most likely do to resolve the issue?
- A . Disable automatic negotiation on Switch11.
- B . Modify Switch10 MTU value to 1500.
- C . Configure STP on both switches.
- D . Change the native VLAN on the ports.
Several users in an organization report connectivity issues and lag during a video meeting. The network administrator performs a tcpdump and observes increased retransmissions for other non-video applications on the network.
Which of the following symptoms describes the users’ reported issues?
- A . Latency
- B . Packet loss
- C . Bottlenecking
- D . Jitter
B
Explanation:
Packet loss occurs when network packets fail to reach their destination, leading to disruptions in connectivity and performance issues. In this scenario:
Users report connectivity issues and lag during video meetings.
The administrator detects increased retransmissions in tcpdump, which is a strong indicator of lost packets that must be resent.
Video meetings are particularly sensitive to packet loss, leading to buffering, frozen screens, and dropped calls.
Latency (Option A) refers to delayed data transmission but does not necessarily cause retransmissions.
Bottlenecking (Option C) happens when a network component (e.g., router, switch) cannot handle the traffic load, but packet retransmissions are more directly related to packet loss.
Jitter (Option D) affects the consistency of packet arrival times, but the symptoms described here are more aligned with packet loss rather than timing variations.
?
Reference: CompTIA Network+ (N10-009) Official Study Guide C Section: Troubleshooting Connectivity Issues
Which of the following best explains the role of confidentiality with regard to data at rest?
- A . Datacanbe accessedby anyone on the administrative network.
- B . Datacanbe accessedremotely with proper training.
- C . Datacanbe accessedafter privileged access Is granted.
- D . Datacanbe accessedafter verifying the hash.
C
Explanation:
Confidentiality with Data at Rest: Confidentiality is a core principle of data security, ensuring that data stored (at rest) is only accessible to authorized individuals. This protection is achieved through mechanisms such as encryption, access controls, and permissions.
Privileged Access: The statement "Data can be accessed after privileged access is granted" aligns with the confidentiality principle, as it restricts data access to users who have been granted specific permissions or roles. Only those with the appropriate credentials or permissions can access the data. Incorrect Options:
Which of the following steps of the troubleshooting methodology should a technician take to confirm a theory?
- A . Duplicate the problem.
- B . Identify the symptoms.
- C . Gather information.
- D . Determine any changes.
A
Explanation:
Troubleshooting Methodology:
Troubleshooting involves a systematic approach to diagnosing and resolving issues. It typically includes steps such as identifying symptoms, gathering information, formulating and testing theories, and implementing solutions.
Confirming a Theory:
Duplicate the Problem: To confirm a theory, the technician should reproduce the problem in a controlled environment. This helps verify that the identified cause actually leads to the observed issue.
Verification: By duplicating the problem, the technician can observe the issue firsthand, validate the hypothesis, and rule out other potential causes.
Comparison with Other Steps:
Identify the Symptoms: Initial step to understand what the problem is, not specifically for confirming a theory.
Gather Information: Involves collecting data and details about the issue, usually done before formulating a theory.
Determine Any Changes: Involves checking for recent changes that could have caused the issue, a
part of the information-gathering phase.
Implementation:
Use similar equipment or software in a test environment to recreate the issue.
Observe the results to see if they match the original problem, thereby confirming the theory.
Reference: CompTIA Network+ study materials on troubleshooting methodologies and best practices.
A network administrator is in the process of installing 35 PoE security cameras. After the administrator installed and tested the new cables, the administrator installed the cameras. However, a small number of the cameras do not work.
Which of the following is the most reason?
- A . Incorrect wiring standard
- B . Power budget exceeded
- C . Signal attenuation
- D . Wrong voltage
B
Explanation:
When installing multiple Power over Ethernet (PoE) devices like security cameras, it is crucial to ensure that the total power requirement does not exceed the power budget of the PoE switch. Each PoE switch has a maximum power capacity, and exceeding this capacity can cause some devices to fail to receive power.
PoE Standards: PoE switches conform to standards such as IEEE 802.3af (PoE) and 802.3at (PoE+), each with specific power limits per port and total power capacity.
Power Calculation: Adding up the power requirements of all connected PoE devices can help determine if the total power budget of the switch is exceeded.
Symptoms: When the power budget is exceeded, some devices, typically those farthest from the switch or connected last, may not power up or function correctly. Network
Reference: CompTIA Network+ N10-007 Official Certification Guide: Covers PoE standards and troubleshooting power issues.
Cisco Networking Academy: Discusses PoE technologies, power budgeting, and managing PoE devices.
Network+ Certification All-in-One Exam Guide: Provides information on PoE setup, including power budget considerations.
A network consultant needs to decide between running an ethernet uplink or using the built-in 5GHz-to-point functionality on a WAP.
Which of the following documents provides the best information to assist the consultant with this decision?
- A . Site survey results
- B . Physical diagram
- C . Service-level agreement
- D . Logical diagram
A network administrator needs to divide 192.168.1.0/24 into two equal halves.
Which of the following subnet masks should the administrator use?
- A . 255.255.0.0
- B . 255.255.254.0
- C . 255.255.255.0
- D . 255.255.255.128
D
Explanation:
Understanding Subnetting:
Original Network: 192.168.1.0/24 has a subnet mask of 255.255.255.0, which allows for 256 IP addresses (including network and broadcast addresses). Objective: Divide this network into two equal subnets.
Calculating Subnet Mask:
New Subnet Mask: To divide 192.168.1.0/24 into two equal halves, we need to borrow one bit from the host portion of the address, changing the subnet mask to 255.255.255.128 (/25).
Subnet Breakdown:
First Subnet: 192.168.1.0/25 (192.168.1.0 – 192.168.1.127)
Second Subnet: 192.168.1.128/25 (192.168.1.128 – 192.168.1.255)
Verification:
Each subnet now has 128 IP addresses (126 usable IP addresses, excluding the network and broadcast addresses).
Comparison with Other Options:
Which of the following is the most likely reason an insurance brokerage would enforce VPN usage?
- A . To encrypt sensitive data in transit
- B . To secure the endpoint
- C . To maintain contractual agreements
- D . To comply with data retention requirements
A
Explanation:
The most likely reason an insurance brokerage would enforce VPN usage is to encrypt sensitive data in transit. VPNs (Virtual Private Networks) create a secure tunnel between the user’s device and the corporate network, ensuring that data is encrypted and protected from interception.
Encryption: VPNs encrypt data, preventing unauthorized access and ensuring data privacy during transmission over public or unsecured networks.
Data Protection: Essential for industries handling sensitive information, such as insurance brokerages, to protect customer data and comply with regulatory requirements.
Security: Enhances overall network security by providing secure remote access for employees.
Network
Reference: CompTIA Network+ N10-007 Official Certification Guide: Discusses the role of VPNs in securing data in transit.
Cisco Networking Academy: Provides training on VPN technologies and their importance in data security.
Network+ Certification All-in-One Exam Guide: Explains VPN usage and its benefits in protecting sensitive information.
