Practice Free JN0-636 Exam Online Questions
You are asked to detect domain generation algorithms
Which two steps will accomplish this goal on an SRX Series firewall? (Choose two.)
- A . Define an advanced-anti-malware policy under [edit services].
- B . Attach the security-metadata-streaming policy to a security
- C . Define a security-metadata-streaming policy under [edit
- D . Attach the advanced-anti-malware policy to a security policy.
You are asked to determine if the 203.0.113.5 IP address has been added to the third-party security feed, DS hield, from Juniper Seclnte1. You have an SRX Series device that is using Seclnte1 feeds from Juniper ATP Cloud
Which command will return this information?
- A . show security dynamic―address category―name CC | match 203.0.113.5
- B . show security dynamic―address category―name Infected―Hosts | match 203.0.113.5
- C . show security dynamic-address category-name IPFilter I match 203.0.113.5
- D . show Security dynamic-address category-name JWAS | match 203.0.113.5
All interfaces involved in transparent mode are configured with which protocol family?
- A . mpls
- B . bridge
- C . inet
- D . ethernet ― switching
You are asked to share threat intelligence from your environment with third party tools so that those tools can be identify and block lateral threat propagation from compromised hosts.
Which two steps accomplish this goal? (Choose Two)
- A . Configure application tokens in the SRX Series firewalls to limit who has access
- B . Enable Juniper ATP Cloud to share threat intelligence
- C . Configure application tokens in the Juniper ATP Cloud to limit who has access
- D . Enable SRX Series firewalls to share Threat intelligence with third party tool.
BC
Explanation:
To share threat intelligence from your environment with third party tools, you need to enable Juniper ATP Cloud to share threat intelligence and configure application tokens in the Juniper ATP Cloud to limit who has access. The other options are incorrect because:
A) Configuring application tokens in the SRX Series firewalls is not necessary or sufficient to share threat intelligence with third party tools. Application tokens are used to authenticate and authorize requests to the Juniper ATP Cloud API, which can be used to perform various operations such as submitting files, querying C&C feeds, and managing allowlists and blocklists1. However, to share threat intelligence with third party tools, you need to enable the TAXII service in the Juniper ATP Cloud, which is a different protocol for exchanging threat information2.
D) Enabling SRX Series firewalls to share threat intelligence with third party tools is not possible or supported. SRX Series firewalls can send potentially malicious objects and files to the Juniper ATP Cloud for analysis and receive threat intelligence from the Juniper ATP Cloud to block malicious traffic3. However, SRX Series firewalls cannot directly share threat intelligence with third party tools. You need to use the Juniper ATP Cloud as the intermediary for threat intelligence sharing. Therefore, the correct answer is B and C. You need to enable Juniper ATP Cloud to share threat intelligence and configure application tokens in the Juniper ATP Cloud to limit who has access.
To do so, you need to perform the following steps:
Enable and configure the TAXII service in the Juniper ATP Cloud. TAXII (Trusted Automated eXchange of Indicator Information) is a protocol for communication over HTTPS of threat information between parties. STIX (Structured Threat Information eXpression) is a language used for reporting and sharing threat information using TAXII. Juniper ATP Cloud can contribute to STIX reports by sharing the threat intelligence it gathers from file scanning. Juniper ATP Cloud also uses threat information from STIX reports as well as other sources for threat prevention2. To enable and configure the TAXII service, you need to select Configure > Threat Intelligence Sharing in the Juniper ATP Cloud WebUI, move the knob to the right to Enable TAXII, and move the slidebar to designate a file sharing threshold2. Configure application tokens in the Juniper ATP Cloud. Application tokens are used to authenticate and authorize requests to the Juniper ATP Cloud API and the TAXII service. You can create and manage application tokens in the Juniper ATP Cloud WebUI by selecting Configure > Application Tokens. You can specify the name, description, expiration date, and permissions of each token. You can also revoke or delete tokens as needed. You can use the application tokens to limit who has access to your shared threat intelligence by granting or denying permissions to the TAXII service1.
Reference: Threat Intelligence Open API Setup Guide
Configure Threat Intelligence Sharing
About Juniper Advanced Threat Prevention Cloud
Exhibit
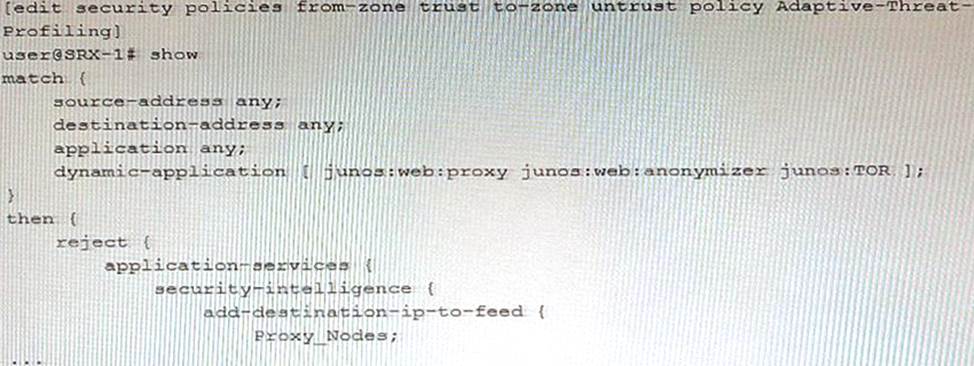
Referring to the exhibit, which two statements are true? (Choose two.)
- A . The SRX-1 device can use the Proxy__Nodes feed in another security policy.
- B . You can use the Proxy_Nodes feed as the source-address and destination-address match criteria of another security policy on a different SRX Series device.
- C . The SRX-1 device creates the Proxy_wodes feed, so it cannot use it in another security policy.
- D . You can only use the Proxy_Node3 feed as the destination-address match criteria of another security policy on a different SRX Series device.
According to the log shown in the exhibit, you notice the IPsec session is not establishing.
What is the reason for this behavior?
- A . Mismatched proxy ID
- B . Mismatched peer ID
- C . Mismatched preshared key
- D . Incorrect peer address.
B
Explanation:
https://www.juniper.net/documentation/en_US/release-independent/nce/topics/example/policy-based-vpn-using-j-series-srxseries-device-configuring.html
You have noticed a high number of TCP-based attacks directed toward your primary edge device. You are asked to configure the IDP feature on your SRX Series device to block this attack.
Which two IDP attack objects would you configure to solve this problem? (Choose two.)
- A . Network
- B . Signature
- C . Protocol anomaly
- D . host
In Juniper ATP Cloud, what are two different actions available in a threat prevention policy to deal with an infected host? (Choose two.)
- A . Send a custom message
- B . Close the connection.
- C . Drop the connection silently.
- D . Quarantine the host.
Refer to the Exhibit:

Which two statements about the configuration shown in the exhibit are correct?
- A . The remote IKE gateway IP address is 203.0.113.100.
- B . The local peer is assigned a dynamic IP address.
- C . The local IKE gateway IP address is 203.0.113.100.
- D . The remote peer is assigned a dynamic IP address.
AD
Explanation:
The two statements about the configuration shown in the exhibit are correct are:
A) The remote IKE gateway IP address is 203.0.113.100. The exhibit shows that the address option under the gateway statement is set to 203.0.113.100, which specifies the IP address of the primary IKE gateway. The address option is used to configure the IP address or the hostname of the remote peer that has a static IP address1.
D) The remote peer is assigned a dynamic IP address. The exhibit shows that the dynamic option under the gateway statement is configured with various attributes, such as general-ikeid, ike-user-type, and user-at-hostname. The dynamic option is used to configure the identifier for the remote gateway with a dynamic IP address. The dynamic option also enables the SRX Series device to accept multiple connections from remote peers that have the same identifier2.
The other statements are incorrect because:
B) The local peer is not assigned a dynamic IP address, but a static IP address. The exhibit shows that the local-address option under the gateway statement is set to 192.0.2.100, which specifies the IP address of the local IKE gateway. The local-address option is used to configure the IP address of the local peer that has a static IP address1.
C) The local IKE gateway IP address is not 203.0.113.100, but 192.0.2.100, as explained above.
Reference: gateway (Security IKE) dynamic (Security IKE)
You are required to deploy a security policy on an SRX Series device that blocks all known Tor network IP addresses.
Which two steps will fulfill this requirement? (Choose two.)
- A . Enroll the devices with Juniper ATP Appliance.
- B . Enroll the devices with Juniper ATP Cloud.
- C . Enable a third-party Tor feed.
- D . Create a custom feed containing all current known MAC addresses.
