Practice Free H12-891_V1.0-ENU Exam Online Questions
Which of the following commands can be used to view BGP VPNv4 routing and BGP private network routing information on PE?
- A . display bgp vpnv4 all routing-table
- B . display bgp routing-table address-family vpnv4
- C . display vpnv4 bgp routing-table
- D . display bgp routing-table ipv4-family vpnv4
Which of the following descriptions of strategic linkage plans are correct? (Multiple choice)
- A . Establish a CAPWAP tunnel between the authentication control point and the authentication execution point. Through this tunnel, user association, message communication, user authorization policy issuance, and user synchronization between the authentication control device and the authentication execution device are completed.
- B . Since the CAPWAP tunnel is used, the authentication execution point device does not need to enable the BPDU transparent transmission function.
- C . The authentication control point device is responsible for validating the identity of users accessing the network and specifying the network access rights that legitimate users can have, that is, which resources the users can access.
- D . The authentication execution point device is responsible for executing the user’s network access policy. That is, when the user accesses the network after completing the authentication, the corresponding access policy is executed, such as the VLAN, ACL, UCL group to which the user belongs, etc.
A certain campus network has deployed the business mobility function through ilaster NCE Campus. The configured policy control matrix is as shown in the figure.
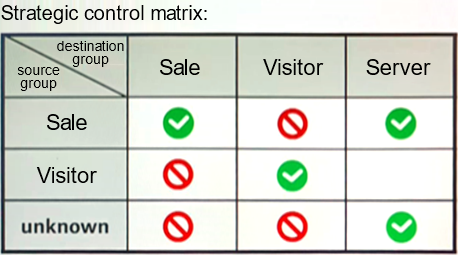
Which of the following descriptions of this policy control matrix is wrong?
- A . If the policy execution point does not find the security group corresponding to an IP address, the traffic of the IP address can access the server group
- B . The guest group can access the guest group
- C . The sales group and the guest group cannot access each other.
- D . If the server group is a resource group, you can configure a policy whose source is the server group.
As shown in the figure, the OSPF protocol is enabled on all interfaces of the router, and R4 and R5 can establish OSPF virtual connections.
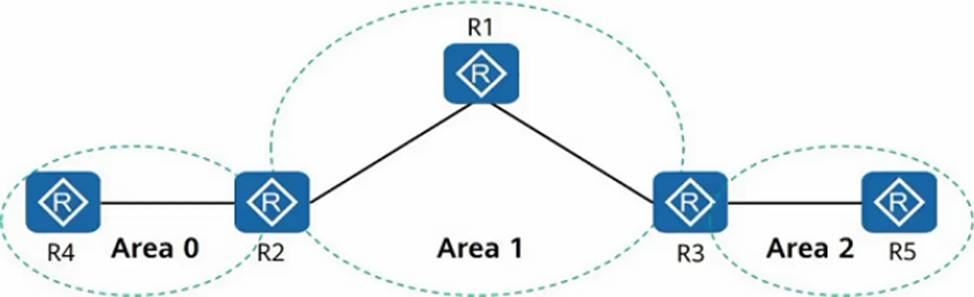
- A . True
- B . False
Network access authentication can be deployed at different levels of the network according to actual needs. Compared with deploying authentication at the aggregation layer or core layer of the network, deploying authentication at the access layer is more conducive to achieving fine-grained management of permissions and high network efficiency safety.
- A . True
- B . False
The request header field Accept-Language indicates the language type desired by the client.
- A . True
- B . False
Which of the following description of Network-Summary-LSA is correct? (Multiple choice)
- A . The Link State ID in Network-Summary-LSA is set to the IP address of the destination network
- B . The Metric in Network-Summary-LSA is set to the cost value from the ABR to the destination network segment.
- C . The Net mask in Network Summary-LSA is set to the network mask of the destination network segment.
- D . Network-Summary LSA is generated by ASBR
In Huawei’s SD-WAN solution, which of the following are the application optimization functions? (Multiple choice)
- A . QoS
- B . Intelligent routing
- C . Application identification
- D . Wide area optimization
Which of the following tunneling technologies does Huawei SD-WAN solution use to establish data channels?
- A . GRE Over IPsec
- B . VXLAN
- C . MPLS
- D . IPSec
Python Paramiko implements the SSH protocol. In the Python Paramiko module, which of the following classes is used to create an SFTP session connection and perform remote file operations?
- A . Transport class
- B . Packetizer class
- C . SFTP Client class
- D . Channel class
