Practice Free H12-891_V1.0-ENU Exam Online Questions
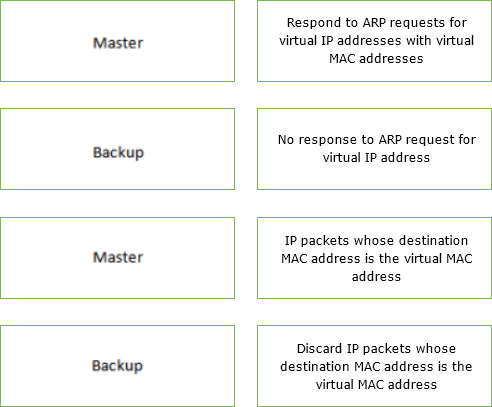
Please match the following VRRP status with the corresponding working mechanism
By executing the (), users on different ports in the same VLAN can be completely separated from each other on the second and third floors and cannot communicate.
Which of the following methods can be used to introduce traffic into the SR-MIPLS TE tunnel? (Multiple choice)
- A . Configure a static route and specify the outbound interface of the static route as the tunnel interface of SR HIPLS TE.
- B . Treat the SR-IPLS TE tunnel as a logical link to participate in IGP route calculation
- C . In the execution statement of policy routing, use the SR-MPLS TE tunnel interface as the outbound interface.
- D . By configuring tunnel policies
Which of the following source node behaviors can insert SRH into IPv6 packets? (Multiple choice)
- A . H. Encaps
- B . H. Insert
- C . H. Encaps. Red
- D . H. Insert. Red
Which of the following description of LinkID, Data, Type and Metric in Router-LSA is correct? (Multiple choice)
- A . Link ID represents the local identification of this connection. Different connection types have different meanings.
- B . Type indicates the type of connection
- C . Metric describes the cost of this connection
- D . Data is used to describe additional information about this connection. Different connection types describe different information.
When deploying BGP/MPLS IP VPN, when two VPNs have a common site, the common site must not use overlapping address spaces with other sites of the two VPNs.
- A . True
- B . False
Which of the following BGP routing attributes cannot control BGP route selection?
- A . Originator ID
- B . MED
- C . AS_Path
- D . Community
IPv6 over IPv4 uses tunnel technology to transmit IPv6 packets in IPv4 networks to realize island interconnection between IPv6 networks. The source IPv4 address and destination IPv4 address of the IPv6 over IPv4 tunnel must be configured manually.
- A . True
- B . False
Which of the following are common techniques for differentiating service models? (Multiple choice)
- A . Traffic speed limiting technology
- B . WAN acceleration technology
- C . Congestion avoidance technology
- D . Congestion management technology
Part of the configuration of device H is as shown in the figure. Which item is wrong in the following description of this configuration?
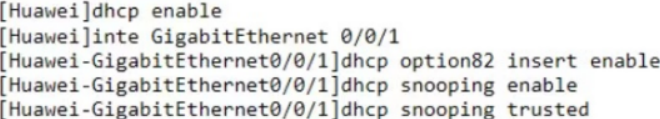
- A . Configure GigabitEthernet0/0/1 interface as a trusted interface
- B . Enable DHCP Snooping configuration to prevent ARP spoofing attacks
- C . If the DHCP request message received by the GigabitEthernet0/0/1 interface does not contain the SubOption information of Option82, the device will generate Option82 and insert it into the message.
- D . Enabling DHCP Snooping configuration can be used to prevent DHCP Server bogus attacks.
