Practice Free FCSS_SOC_AN-7.4 Exam Online Questions
Which two playbook triggers enable the use of trigger events in later tasks as trigger variables? (Choose two.)
- A . EVENT
- B . INCIDENT
- C . ON SCHEDULE
- D . ON DEMAND
AB
Explanation:
Understanding Playbook Triggers:
Playbook triggers are the starting points for automated workflows within FortiAnalyzer or FortiSOAR. These triggers determine how and when a playbook is executed and can pass relevant information (trigger variables) to subsequent tasks within the playbook. Types of Playbook Triggers:
EVENT Trigger:
Initiates the playbook when a specific event occurs.
The event details can be used as variables in later tasks to customize the response.
Selected as it allows using event details as trigger variables.
INCIDENT Trigger:
Activates the playbook when an incident is created or updated. The incident details are available as variables in subsequent tasks. Selected as it enables the use of incident details as trigger variables. ON SCHEDULE Trigger:
Executes the playbook at specified times or intervals.
Does not inherently use trigger events to pass variables to later tasks.
Not selected as it does not involve passing trigger event details.
ON DEMAND Trigger:
Runs the playbook manually or as required.
Does not automatically include trigger event details for use in later tasks. Not selected as it does not use trigger events for variables. Implementation Steps:
Step 1: Define the conditions for the EVENT or INCIDENT trigger in the playbook configuration. Step 2: Use the details from the trigger event or incident in subsequent tasks to customize actions and responses.
Step 3: Test the playbook to ensure that the trigger variables are correctly passed and utilized.
Conclusion:
EVENT and INCIDENT triggers are specifically designed to initiate playbooks based on specific occurrences, allowing the use of trigger details in subsequent tasks.
Reference: Fortinet Documentation on Playbook Configuration FortiSOAR Playbook Guide
By using the EVENT and INCIDENT triggers, you can leverage trigger events in later tasks as variables, enabling more dynamic and responsive playbook actions.
Refer to the exhibits.
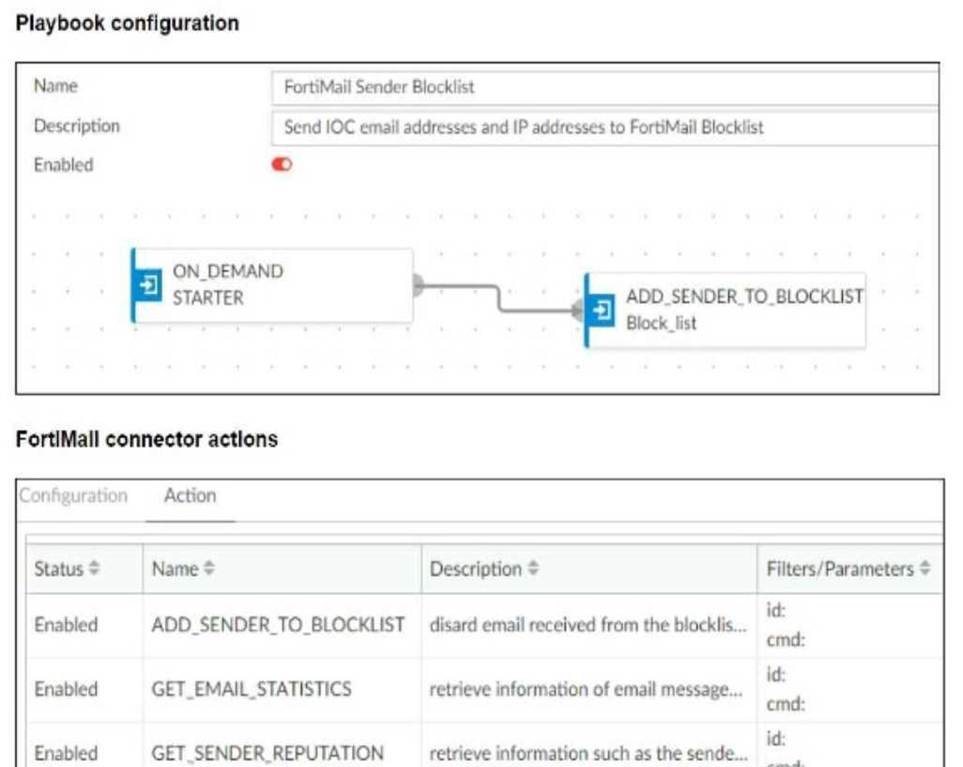
The FortiMail Sender Blocklist playbook is configured to take manual input and add those entries to the FortiMail abc. com domain-level block list. The playbook is configured to use a FortiMail connector and the ADD_SENDER_TO_BLOCKLIST action.
Why is the FortiMail Sender Blocklist playbook execution failing7
- A . You must use the GET_EMAIL_STATISTICS action first to gather information about email messages.
- B . FortiMail is expecting a fully qualified domain name (FQDN).
- C . The client-side browser does not trust the FortiAnalzyer self-signed certificate.
- D . The connector credentials are incorrect
B
Explanation:
Understanding the Playbook Configuration:
The playbook "FortiMail Sender Blocklist" is designed to manually input email addresses or IP addresses and add them to the FortiMail block list.
The playbook uses a FortiMail connector with the action ADD_SENDER_TO_BLOCKLIST.
Analyzing the Playbook Execution:
The configuration and actions provided show that the playbook is straightforward, starting with an
ON_DEMAND STARTER and proceeding to the ADD_SENDER_TO_BLOCKLIST action.
The action description indicates it is intended to block senders based on email addresses or domains.
Evaluating the Options:
Option A: Using GET_EMAIL_STATISTICS is not required for the task of adding senders to a block list.
This action retrieves email statistics and is unrelated to the block list configuration.
Option B: The primary reason for failure could be the requirement for a fully qualified domain name (FQDN). FortiMail typically expects precise information to ensure the correct entries are added to the block list.
Option C: The trust level of the client-side browser with FortiAnalyzer’s self-signed certificate does not impact the execution of the playbook on FortiMail.
Option D: Incorrect connector credentials would result in an authentication error, but the problem described is more likely related to the format of the input data. Conclusion:
The FortiMail Sender Blocklist playbook execution is failing because FortiMail is expecting a fully
qualified domain name (FQDN).
Reference: Fortinet Documentation on FortiMail Connector Actions.
Best Practices for Configuring FortiMail Block Lists.
Refer to the Exhibit:
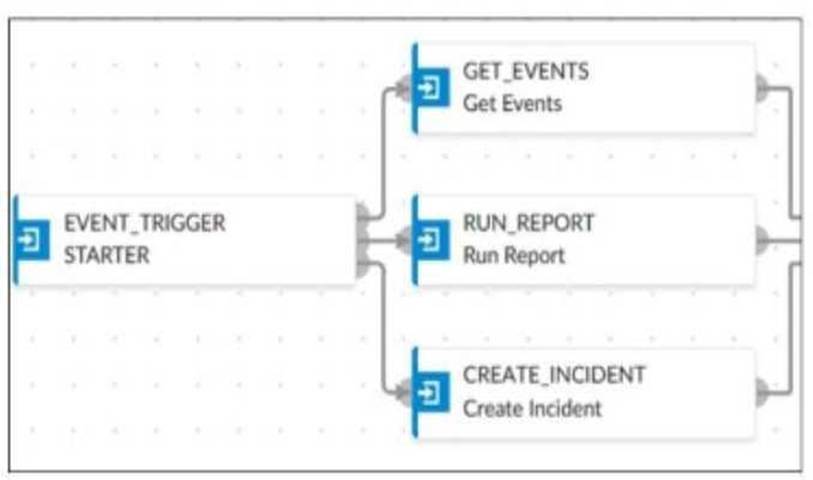
An analyst wants to create an incident and generate a report whenever FortiAnalyzer generates a malicious attachment event based on FortiSandbox analysis. The endpoint hosts are protected by FortiClient EMS integrated with FortiSandbox. All devices are logging to FortiAnalyzer.
Which connector must the analyst use in this playbook?
- A . FortiSandbox connector
- B . FortiClient EMS connector
- C . FortiMail connector
- D . Local connector
A
Explanation:
Understanding the Requirements:
The objective is to create an incident and generate a report based on malicious attachment events detected by FortiAnalyzer from FortiSandbox analysis.
The endpoint hosts are protected by FortiClient EMS, which is integrated with FortiSandbox. All logs
are sent to FortiAnalyzer.
Key Components:
FortiAnalyzer: Centralized logging and analysis for Fortinet devices.
FortiSandbox: Advanced threat protection system that analyzes suspicious files and URLs.
FortiClient EMS: Endpoint management system that integrates with FortiSandbox for endpoint
protection.
Playbook Analysis:
The playbook in the exhibit consists of three main actions: GET_EVENTS, RUN_REPORT, and CREATE_INCIDENT.
EVENT_TRIGGER: Starts the playbook when an event occurs.
GET_EVENTS: Fetches relevant events.
RUN_REPORT: Generates a report based on the events.
CREATE_INCIDENT: Creates an incident in the incident management system.
Selecting the Correct Connector:
The correct connector should allow fetching events related to malicious attachments analyzed by FortiSandbox and facilitate integration with FortiAnalyzer. Connector Options:
FortiSandbox Connector:
Directly integrates with FortiSandbox to fetch analysis results and events related to malicious attachments.
Best suited for getting detailed sandbox analysis results.
Selected as it is directly related to the requirement of handling FortiSandbox analysis events.
FortiClient EMS Connector:
Used for managing endpoint security and integrating with endpoint logs.
Not directly related to fetching sandbox analysis events.
Not selected as it is not directly related to the sandbox analysis events.
FortiMail Connector:
Used for email security and handling email-related logs and events.
Not applicable for sandbox analysis events.
Not selected as it does not relate to the sandbox analysis.
Local Connector:
Handles local events within FortiAnalyzer itself.
Might not be specific enough for fetching detailed sandbox analysis results. Not selected as it may not provide the required integration with FortiSandbox. Implementation Steps:
Step 1: Ensure FortiSandbox is configured to send analysis results to FortiAnalyzer.
Step 2: Use the FortiSandbox connector in the playbook to fetch events related to malicious attachments.
Step 3: Configure the GET_EVENTS action to use the FortiSandbox connector.
Step 4: Set up the RUN_REPORT and CREATE_INCIDENT actions based on the fetched events.
Reference: Fortinet Documentation on FortiSandbox Integration FortiSandbox Integration Guide Fortinet Documentation on FortiAnalyzer Event Handling FortiAnalyzer Administration Guide
By using the FortiSandbox connector, the analyst can ensure that the playbook accurately fetches events based on FortiSandbox analysis and generates the required incident and report.
What is the primary purpose of using collectors in a FortiAnalyzer deployment?
- A . To store backup configurations
- B . To aggregate and analyze log data
- C . To enhance the graphical user interface
- D . To manage network bandwidth usage
When configuring a FortiAnalyzer to act as a collector device, which two steps must you perform? (Choose two.)
- A . Enable log compression.
- B . Configure log forwarding to a FortiAnalyzer in analyzer mode.
- C . Configure the data policy to focus on archiving.
- D . Configure Fabric authorization on the connecting interface.
BD
Explanation:
Understanding FortiAnalyzer Roles:
FortiAnalyzer can operate in two primary modes: collector mode and analyzer mode. Collector Mode: Gathers logs from various devices and forwards them to another FortiAnalyzer operating in analyzer mode for detailed analysis.
Analyzer Mode: Provides detailed log analysis, reporting, and incident management.
Steps to Configure FortiAnalyzer as a Collector Device:
In the context of threat hunting, which information feeds are most beneficial?
- A . Stock market trends
- B . Cyber threat intelligence
- C . Marketing data
- D . Corporate governance updates
Which two statements about the FortiAnalyzer Fabric topology are true? (Choose two.)
- A . Downstream collectors can forward logs to Fabric members.
- B . Logging devices must be registered to the supervisor.
- C . The supervisor uses an API to store logs, incidents, and events locally.
- D . Fabric members must be in analyzer mode.
BD
Explanation:
Understanding FortiAnalyzer Fabric Topology:
The FortiAnalyzer Fabric topology is designed to centralize logging and analysis across multiple devices in a network.
It involves a hierarchy where the supervisor node manages and coordinates with other Fabric members.
Analyzing the Options:
Option A: Downstream collectors forwarding logs to Fabric members is not a typical configuration.
Instead, logs are usually centralized to the supervisor.
Option B: For effective management and log centralization, logging devices must be registered to the supervisor. This ensures proper log collection and coordination.
Option C: The supervisor does not primarily use an API to store logs, incidents, and events locally.
Logs are stored directly in the FortiAnalyzer database.
Option D: For the Fabric topology to function correctly, all Fabric members need to be in analyzer
mode. This mode allows them to collect, analyze, and forward logs appropriately within the
topology.
Conclusion:
The correct statements regarding the FortiAnalyzer Fabric topology are that logging devices must be registered to the supervisor and that Fabric members must be in analyzer mode.
Reference: Fortinet Documentation on FortiAnalyzer Fabric Topology.
Best Practices for Configuring FortiAnalyzer in a Fabric Environment.
