Practice Free FCSS_SOC_AN-7.4 Exam Online Questions
How do event handlers improve the efficiency of SOC operations?
- A . By automating routine decision-making processes
- B . By eliminating the need for IT staff
- C . By reducing the number of security tools needed
- D . By increasing the volume of data storage
Which role does a threat hunter play within a SOC?
- A . investigate and respond to a reported security incident
- B . Collect evidence and determine the impact of a suspected attack
- C . Search for hidden threats inside a network which may have eluded detection
- D . Monitor network logs to identify anomalous behavior
C
Explanation:
Role of a Threat Hunter:
A threat hunter proactively searches for cyber threats that have evaded traditional security defenses.
This role is crucial in identifying sophisticated and stealthy adversaries that bypass automated
detection systems.
Key Responsibilities:
Proactive Threat Identification:
Threat hunters use advanced tools and techniques to identify hidden threats within the network. This includes analyzing anomalies, investigating unusual behaviors, and utilizing threat intelligence.
Reference: SANS Institute, "Threat Hunting: Open Season on the Adversary" SANS Threat Hunting Understanding the Threat Landscape:
They need a deep understanding of the threat landscape, including common and emerging tactics, techniques, and procedures (TTPs) used by threat actors.
Reference: MITRE ATT&CK Framework MITRE ATT&CK
Advanced Analytical Skills:
Utilizing advanced analytical skills and tools, threat hunters analyze logs, network traffic, and endpoint data to uncover signs of compromise.
Reference: Cybersecurity and Infrastructure Security Agency (CISA) Threat Hunting Guide CISA Threat Hunting
Distinguishing from Other Roles:
Investigate and Respond to Incidents (A):
This is typically the role of an Incident Responder who reacts to reported incidents, collects evidence, and determines the impact.
Reference: NIST Special Publication 800-61, "Computer Security Incident Handling Guide" NIST Incident Handling
Collect Evidence and Determine Impact (B):
This is often the role of a Digital Forensics Analyst who focuses on evidence collection and impact
assessment post-incident.
Monitor Network Logs (D):
This falls under the responsibilities of a SOC Analyst who monitors logs and alerts for anomalous
behavior and initial detection.
Conclusion:
Threat hunters are essential in a SOC for uncovering sophisticated threats that automated systems may miss. Their proactive approach is key to enhancing the organization’s security posture.
Reference: SANS Institute, "Threat Hunting: Open Season on the Adversary"
MITRE ATT&CK Framework
CISA Threat Hunting Guide
NIST Special Publication 800-61, "Computer Security Incident Handling Guide"
By searching for hidden threats that elude detection, threat hunters play a crucial role in maintaining the security and integrity of an organization’s network.
When configuring playbook triggers, what factor is essential to optimize the efficiency of automated responses?
- A . The color scheme of the playbook interface
- B . The timing and conditions under which the playbook is triggered
- C . The number of pages in the playbook
- D . The geographical location of the SOC
In the context of SOC automation, how does effective management of connectors influence incident management?
- A . It decreases the effectiveness of communication channels
- B . It simplifies the process of handling incidents by automating data exchanges
- C . It increases the need for paper-based reporting
- D . It reduces the importance of cybersecurity training
Which statement describes automation stitch integration between FortiGate and FortiAnalyzer?
- A . An event handler on FortiAnalyzer executes an automation stitch when an event is created.
- B . An automation stitch is configured on FortiAnalyzer and mapped to FortiGate using the FortiOS connector.
- C . An event handler on FortiAnalyzer is configured to send a notification to FortiGate to trigger an automation stitch.
- D . A security profile on FortiGate triggers a violation and FortiGate sends a webhook call to FortiAnalyzer.
D
Explanation:
Overview of Automation Stitches: Automation stitches in Fortinet solutions enable automated
responses to specific events detected within the network. This automation helps in swiftly mitigating
threats without manual intervention.
FortiGate Security Profiles:
FortiGate uses security profiles to enforce policies on network traffic. These profiles can include antivirus, web filtering, intrusion prevention, and more.
When a security profile detects a violation or a specific event, it can trigger predefined actions.
Webhook Calls:
FortiGate can be configured to send webhook calls upon detecting specific security events.
A webhook is an HTTP callback triggered by an event, sending data to a specified URL. This allows FortiGate to communicate with other systems, such as FortiAnalyzer. FortiAnalyzer Integration:
FortiAnalyzer collects logs and events from various Fortinet devices, providing centralized logging and analysis.
Upon receiving a webhook call from FortiGate, FortiAnalyzer can further analyze the event, generate reports, and take automated actions if configured to do so. Detailed Process:
Step 1: A security profile on FortiGate triggers a violation based on the defined security policies.
Step 2: FortiGate sends a webhook call to FortiAnalyzer with details of the violation.
Step 3: FortiAnalyzer receives the webhook call and logs the event.
Step 4: Depending on the configuration, FortiAnalyzer can execute an automation stitch to respond to the event, such as sending alerts, generating reports, or triggering further actions.
Reference: Fortinet Documentation: FortiOS Automation Stitches
FortiAnalyzer Administration Guide: Details on configuring event handlers and integrating with FortiGate.
FortiGate Administration Guide: Information on security profiles and webhook configurations.
By understanding the interaction between FortiGate and FortiAnalyzer through webhook calls and automation stitches, security operations can ensure a proactive and efficient response to security events.
Which two assets are available with the outbreak alert licensed feature on FortiAnalyzer?
(Choose two.)
- A . Custom event handlers from FortiGuard
- B . Outbreak-specific custom playbooks
- C . Custom connectors from FortiGuard
- D . Custom outbreak reports
Refer to the exhibits.
Domain List:
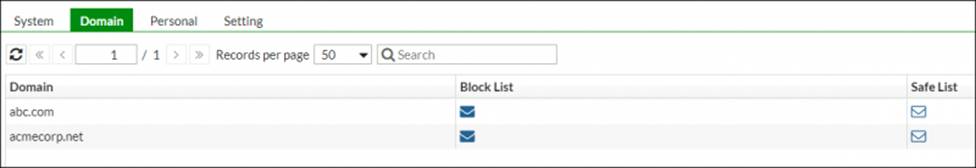
Domain abc.com:
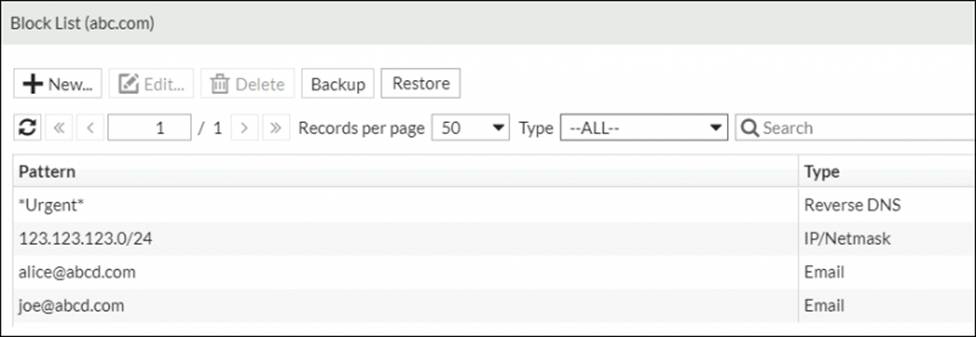
Which connector and action on FortiAnalyzer can you use to add the entries show in the exhibits?
- A . The FortiClient EMS connector and the quarantine action
- B . The FortiMail connector and the add send to blocklist action
- C . The Local connector and the update asset and identity action
- D . The FortiMail connector and the get sender reputation action
Which of the following should be a priority when monitoring SOC playbooks?
- A . Monitoring the personal emails of SOC analysts
- B . Checking for the timely execution of tasks
- C . Ensuring that playbooks are printed and distributed
- D . Watching for unusual increases in playbook file sizes
How does regular monitoring of playbook performance benefit SOC operations?
- A . It enhances the social media presence of the SOC
- B . It ensures playbooks adapt to evolving threat landscapes
- C . It reduces the necessity for cybersecurity insurance
- D . It increases the workload on human resources
What should be monitored in playbooks to ensure they are functioning as intended?
- A . The number of coffee breaks taken by SOC staff
- B . The frequency of playbook activation
- C . The physical health of SOC analysts
- D . The execution paths and outcomes of the playbooks
