Practice Free FCSS_EFW_AD-7.4 Exam Online Questions
Question #81
An administrator wants to scale the IBGP sessions and optimize the routing table in an IBGP network.
Which parameter should the administrator configure?
- A . network-import-check
- B . ibgp-enforce-multihop
- C . neighbor-group
- D . route-reflector-client
Correct Answer: D
D
Explanation:
In anIBGP (Internal BGP) network, all routers must befully meshed, meaning every router must establish a BGP session with every other router in the sameautonomous system (AS). Thisdoes not scale wellin large networks due to the exponential increase in BGP sessions.
Tooptimize and scale IBGP,Route Reflectors (RRs)are used. ARoute Reflector (RR)reduces the number ofIBGP peer connectionsby allowing acentralized router (RR)to redistribute IBGP routes to other IBGP peers (calledclients). This eliminates the need for afull mesh, significantlyreducing BGP session overhead.
By configuring theroute-reflector-clientsetting on IBGP peers, an administrator can:
#Scale IBGP sessionsby reducing the number of direct BGP peer connections.
#Optimize the routing tableby ensuring routes are efficiently propagated within the IBGP network.
#Eliminate the need for full mesh topology, making IBGP more manageable.
D
Explanation:
In anIBGP (Internal BGP) network, all routers must befully meshed, meaning every router must establish a BGP session with every other router in the sameautonomous system (AS). Thisdoes not scale wellin large networks due to the exponential increase in BGP sessions.
Tooptimize and scale IBGP,Route Reflectors (RRs)are used. ARoute Reflector (RR)reduces the number ofIBGP peer connectionsby allowing acentralized router (RR)to redistribute IBGP routes to other IBGP peers (calledclients). This eliminates the need for afull mesh, significantlyreducing BGP session overhead.
By configuring theroute-reflector-clientsetting on IBGP peers, an administrator can:
#Scale IBGP sessionsby reducing the number of direct BGP peer connections.
#Optimize the routing tableby ensuring routes are efficiently propagated within the IBGP network.
#Eliminate the need for full mesh topology, making IBGP more manageable.
Question #82
The IT department discovered during the last network migration that all zero phase selectors in phase 2 IPsec configurations impacted network operations.
What are two valid approaches to prevent this during future migrations? (Choose two.)
- A . Use routing protocols to specify allowed subnets over the tunnel.
- B . Configure an IPsec-aggregate to create redundancy between each firewall peer.
- C . Clearly indicate to the VPN which segments will be encrypted in the phase two selectors.
- D . Configure an IP address on the IPsec interface of each firewall to establish unique peer connections and avoid impacting network operations.
Correct Answer: A C
A C
Explanation:
Zero phase selectors inIPsec Phase 2mean thatno specific traffic selectors (subnets) are defined, allowing any traffic to be encryptedthrough the VPN tunnel. This can causeunintended traffic forwarding issues and disrupt network operations.
To prevent this from happening during future migrations:
#Using routing protocolsensures thatonly specific subnets are advertised over the tunnel. Dynamic routing (such as OSPF or BGP) helps define which networks should use the tunnel, preventing unintended traffic from being encrypted.
#Clearly defining phase 2 selectorsavoids the problem of encrypting all traffic byexplicitly stating the allowed source and destination subnets. This prevents the tunnel from affecting unrelated network traffic.
A C
Explanation:
Zero phase selectors inIPsec Phase 2mean thatno specific traffic selectors (subnets) are defined, allowing any traffic to be encryptedthrough the VPN tunnel. This can causeunintended traffic forwarding issues and disrupt network operations.
To prevent this from happening during future migrations:
#Using routing protocolsensures thatonly specific subnets are advertised over the tunnel. Dynamic routing (such as OSPF or BGP) helps define which networks should use the tunnel, preventing unintended traffic from being encrypted.
#Clearly defining phase 2 selectorsavoids the problem of encrypting all traffic byexplicitly stating the allowed source and destination subnets. This prevents the tunnel from affecting unrelated network traffic.
Question #83
Refer to the exhibit, which shows the output of get system ha status. NGFW-1 and NGFW-2 have been up for a week.
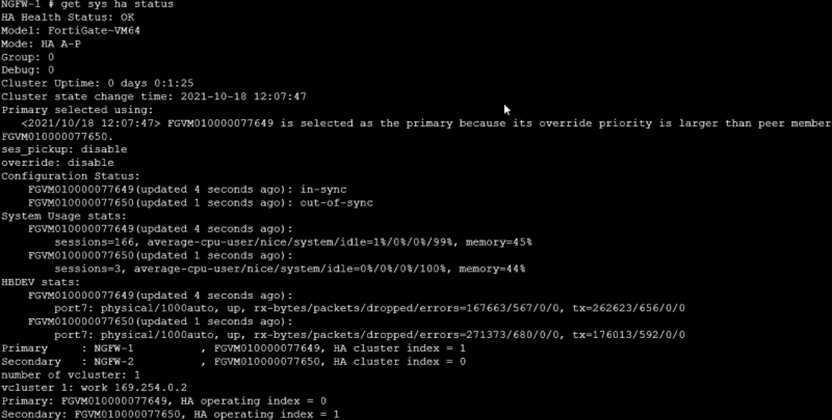
Which two statements about the output are true? (Choose two.)
- A . If FGVM…649 is rebooted, FGVM…650 will become the primary and retain that role, even after FGVM…649 rejoins the cluster.
- B . If no action is taken, the primary FortiGate will leave the cluster due to the current sync status.
- C . If port7 becomes disconnected on the secondary, both FortiGate devices will elect itself the primary.
- D . If a configuration change is made to the primary FortiGate at this time, the secondary will initiate a synchronization reset.
Correct Answer: AC
