Practice Free FCSS_EFW_AD-7.4 Exam Online Questions
Refer to the exhibit, which shows a partial troubleshooting command output.
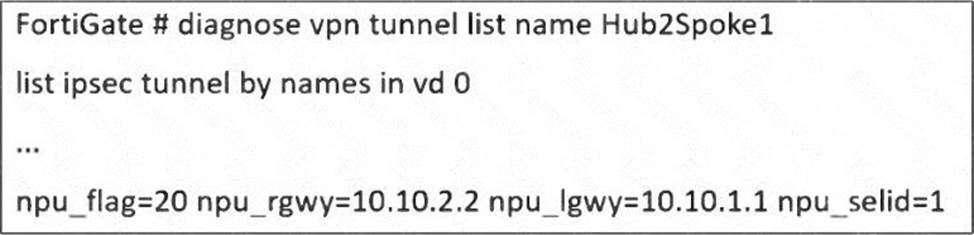
An administrator is extensively using IPsec on FortiGate. Many tunnels show information similar to the output shown in the exhibit.
What can the administrator conclude?
- A . IPsec SAs cannot be offloaded.
- B . The two IPsec SAs, inbound and outbound, are copied to the NPU.
- C . Only the outbound IPsec SA is copied to the NPU.
- D . Only the inbound IPsec SA is copied to the NPU.
B
Explanation:
The diagnose vpn tunnel list name Hub2Spoke1 command output provides key information about the offloading status of an IPsec VPN tunnel to the Network Processing Unit (NPU).
# npu_flag=20:
# This flag indicates that both inbound and outbound IPsec Security Associations (SAs) have been offloaded to the NPU, meaning the VPN traffic is processed in hardware instead of the CPU.
# npu_rgwy=10.10.2.2 and npu_lgwy=10.10.1.1:
# These IPs represent the remote gateway (rgwy) and local gateway (lgwy), confirming that the tunnel is successfully offloaded.
# npu_selid=1:
# This value means the session selector for the NPU offloaded SA is active.
Since both inbound and outbound SAs are offloaded, the administrator can conclude that the FortiGate NPU is handling IPsec encryption and decryption efficiently, reducing CPU load and improving VPN performance.
Exhibits:
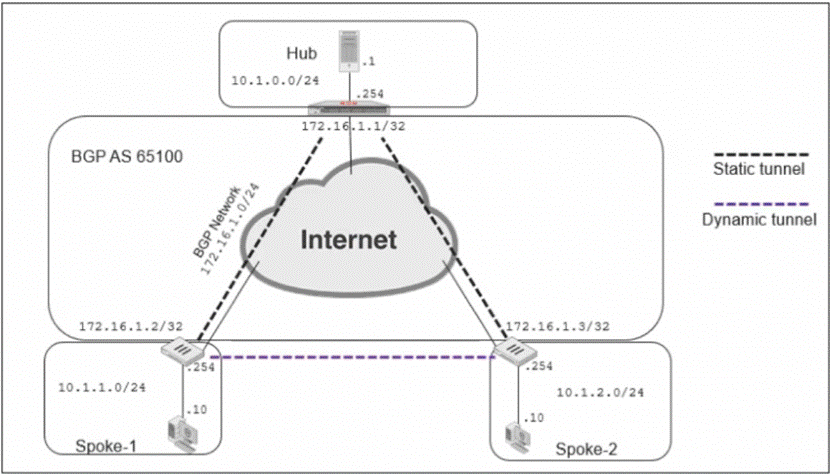
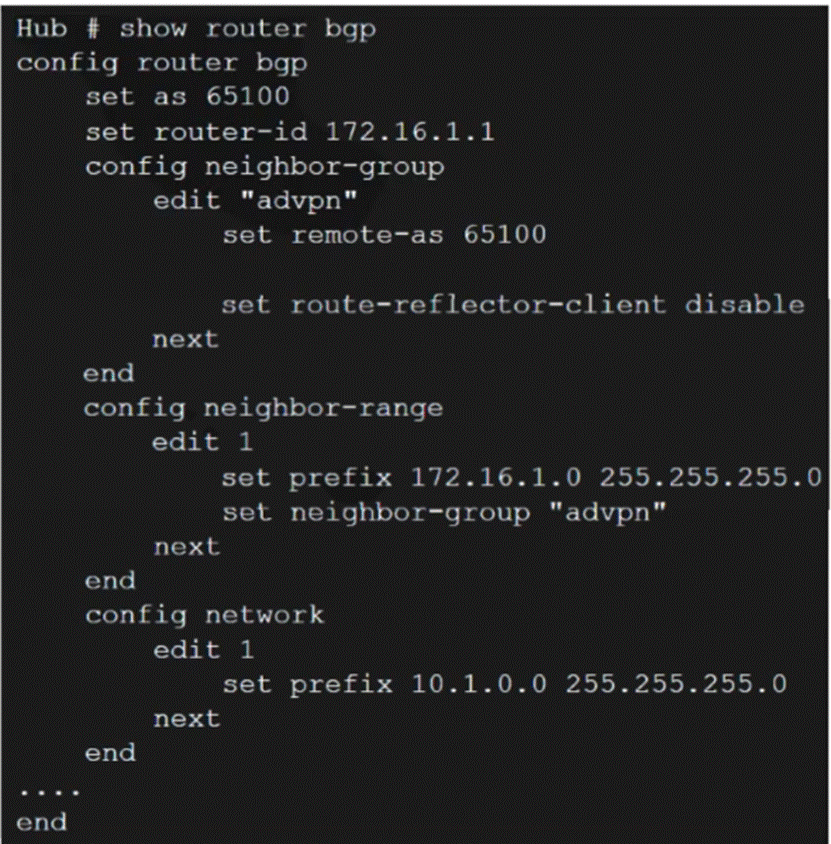
Refer to the exhibits, which contain the network topology and BGP configuration for a hub.
An administrator is trying to configure ADVPN with a hub-spoke VPN setup using iBGP. All the VPNs are up and connected to the hub. The hub is receiving route information from both spokes over iBGP; however, the spokes are not receiving route information from each other.
What change must the administrator make to the hub BGP configuration so that the routes learned by one spoke are forwarded to the other spokes?
- A . Configure the hub as a route reflector client.
- B . Change the router id to 10.1.0.254.
- C . Configure an individual neighbor and remove neighbor-range configuration.
- D . Make the configuration of remote-as different from the configuration of local-as.
An administrator must standardize the deployment of FortiGate devices across branches with consistent interface roles and policy packages using FortiManager.
What is the recommended best practice for interface assignment in this scenario?
- A . Enable metadata variables to use dynamic configurations in the standard interfaces of FortiManager.
- B . Use the Install On feature in the policy package to automatically assign different interfaces based on the branch.
- C . Create interfaces using device database scripts to use them on the same policy package of FortiGate devices.
- D . Create normalized interface types per-platform to automatically recognize device layer interfaces based on the FortiGate model and interface name.
A
Explanation:
Whenstandardizing the deployment of FortiGate devices across branchesusing FortiManager, thebest practiceis to usemetadata variables. This allows fordynamic interface configurationwhile maintaining a single, consistent policy packagefor all branches.
#Metadata variablesin FortiManager enableinterface roles and configurations to be dynamically assigned based on the specific FortiGate device.
# This ensuresscalabilityandconsistent security policy enforcementacross all branches without manually adjusting interface settings for each device.
# When a new branch FortiGate is deployed, metadata variables automaticallymap to the correct physical interfaces, reducing manual configuration errors.
Which step can be taken to ensure that only FortiAP devices receive IP addresses from a DHCP server on FortiGate?
- A . Change the interface addressing mode to FortiAP devices
- B . Create a reservation list in the DHCP server settings
- C . Configure a VCI string value of FortiAP in the DHCP server settings
- D . Use DHCP option 138 to assign IPs to FortiAP devices
What is the purpose of an internal segmentation firewall (ISFW)?
- A . It inspects incoming traffic to protect services in the corporate DMZ.
- B . It is the first line of defense at the network perimeter.
- C . It splits the network into multiple security segments to minimize the impact of breaches.
- D . It is an all-in-one security appliance that is placed at remote sites to extend the enterprise network.
What action does FortiSwitch take when it receives a loop guard data packet (LGDP) that was sent by itself?
- A . The receiving port is shut down
- B . The sending port is shut down
- C . The receiving port is moved to the STP blocking state
- D . The sending port is moved to the STP blocking state
Refer to the exhibit, which contains the partial output of an IKE real-time debug.
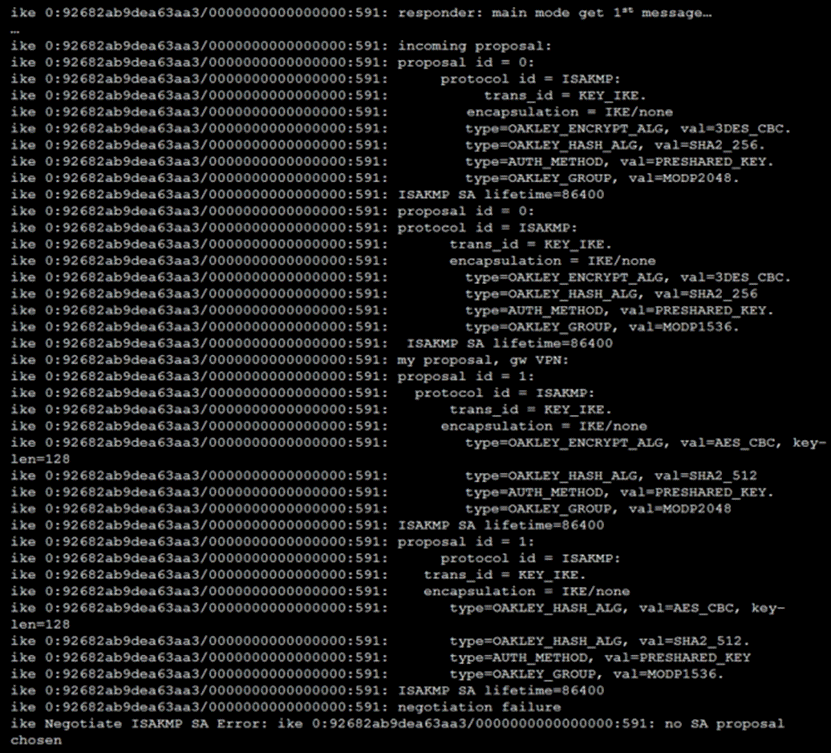
The administrator does not have access to the remote gateway. Based on the debug output, which configuration change can the administrator make to the local gateway to resolve the phase 1 negotiation error?
- A . Change phase 1 encryption to AESCBC and authentication to SHA128.
- B . Change phase 1 encryption to 3DES and authentication to CBC.
- C . Change phase 1 encryption to AES128 and authentication to SHA512.
- D . Change phase 1 encryption to 3DES and authentication to SHA256.
In which of the following states is a given session categorized as ephemeral? (Choose two.)
- A . A TCP session waiting to complete the three-way handshake.
- B . A TCP session waiting for FIN ACK.
- C . A UDP session with packets sent and received.
- D . A UDP session with only one packet received.
Examine these partial outputs from two routing debug commands:
# get router info routing-table database
S 0.0.0.0/0 [20/0] via 100.64.2.254, port2, [10/0]
S *> 0.0.0.0/0 [10/0] via 100.64.1.254, port1
# get router info routing-table all
S* 0.0.0.0/0 [10/0] via 100.64.1.254, port1
Why is the default route that uses port2 not in the output of the second command?
- A . It has a higher distance than the default route using port1.
- B . There can be only one default route present in an active routing table.
- C . It has a higher priority than the default route using port1.
- D . It is disabled in the FortiGate configuration.
Refer to the exhibit, which contains the output of a debug command.
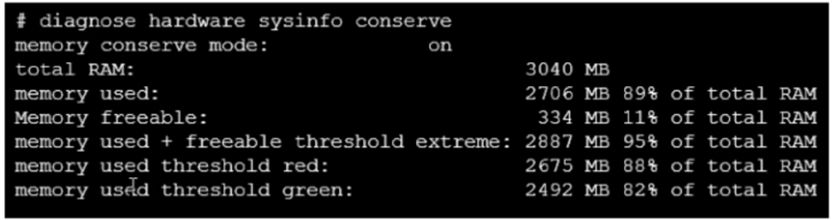
If the default settings are in place, what can be concluded about the conserve mode shown in the exhibit?
- A . FortiGate is currently blocking all new sessions regardless of the content inspection requirements or configuration settings due to high memory use.
- B . FortiGate is currently allowing new sessions that require flow-based or proxy-based content inspection but is not performing inspection on those sessions.
- C . FortiGate is currently blocking new sessions that require flow-based or proxy-based content inspection.
- D . FortiGate is currently allowing new sessions that require flow-based content inspection and blocking sessions that require proxy-based content inspection.
