Practice Free FCSS_ADA_AR-6.7 Exam Online Questions
Question #41
Refer to the exhibit.
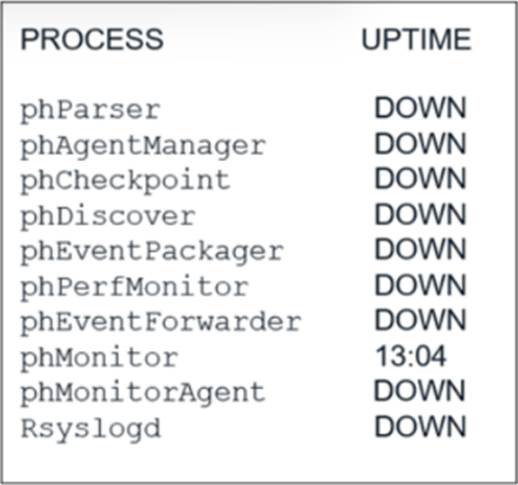
An administrator deploys a new collector for the first time, and notices that all the processes except the phMonitor are down.
How can the administrator bring the processes up?
- A . The administrator needs to run the command phtools –start all on the collector.
- B . Rebooting the collector will bring up the processes.
- C . The processes will come up after the collector is registered to the supervisor.
- D . The collector was not deployed properly and must be redeployed.
Correct Answer: C
Question #42
Which statement accurately contrasts lookup tables with watchlists?
- A . Lookup table values age out after a period, whereas watchlist values do not have any time condition.
- B . You can populate lookup tables through an incident, whereas you cannot populate watchlists through an incident.
- C . Lookup tables can contain multiple columns, whereas watchlists contain only a single column.
- D . You can reference lookup table data in analytic queries and reports almost immediately, whereas you may have to wait up to 5-10 minutes for watchlist entries to be useable in queries and reports.
Correct Answer: C
C
Explanation:
Lookup tables and watchlists serve different purposes in Fortinet’s Advanced Analytics:
● Lookup tables allow for structured data storage with multiple columns, making them useful for correlating different attributes or key-value pairs.
● Watchlists are simpler and contain only a single column, often used for quick reference to flagged values, such as IP addresses or user accounts.
C
Explanation:
Lookup tables and watchlists serve different purposes in Fortinet’s Advanced Analytics:
● Lookup tables allow for structured data storage with multiple columns, making them useful for correlating different attributes or key-value pairs.
● Watchlists are simpler and contain only a single column, often used for quick reference to flagged values, such as IP addresses or user accounts.
Question #43
What is the disadvantage of automatic remediation?
- A . It can make a disruptive change to a user, block access to an application, or disconnect critical systems from the network.
- B . It is equivalent to running an IPS in monitor-only mode ― watches but does not block.
- C . External threats or attacks detected by FortiSIEM will need user interaction to take action on an already overworked SOC team.
- D . Threat behaviors occurring during the night could take hours to respond to.
Correct Answer: A
Question #44
In a customer network that includes a collector, which device performs device discoveries?
- A . Agent
- B . Supervisor
- C . Worker
- D . Collector
Correct Answer: B
B
Explanation:
In a FortiSIEM deployment, device discovery is handled by the Supervisor, even when a Collector is present.
● The Supervisor initiates active scans using protocols such as SNMP, WMI, SSH, and API queries to discover devices in the network.
● Collectors do not perform discovery; they primarily collect and forward logs from designated devices to the Supervisor.
● Workers handle event processing, not discovery.
B
Explanation:
In a FortiSIEM deployment, device discovery is handled by the Supervisor, even when a Collector is present.
● The Supervisor initiates active scans using protocols such as SNMP, WMI, SSH, and API queries to discover devices in the network.
● Collectors do not perform discovery; they primarily collect and forward logs from designated devices to the Supervisor.
● Workers handle event processing, not discovery.
