Practice Free FCSS_ADA_AR-6.7 Exam Online Questions
Which function of Linux is used by FortiSIEM for collecting logs?
- A . aureport
- B . ausearch
- C . autrace
- D . auditd
Multi-tenancy solutions for SOC environments primarily serve to:
- A . Allow multiple clients to share a single application instance.
- B . Enable faster boot times for SOC servers.
- C . Streamline antivirus scans in the environment.
- D . Deploy agents at a faster rate.
Refer to the exhibit.

The collector is registered and has pulled the license file from the supervisor.
What are the consequences of removing the license file?
- A . The collector must be re-registered with the supervisor to get the license file back.
- B . The collector processes will go down.
- C . The collector must be redeployed to get the license file back.
- D . The license file must be pushed manually from the supervisor.
A
Explanation:
The license file located at /etc/opsd/.fortisiem4x0 is critical for the collector’s operation, as it verifies the collector’s registration with the supervisor and enables proper functionality.
If this license file is removed, the collector:
● Will lose its registration with the supervisor.
● Will stop receiving updates and configurations from the FortiSIEM supervisor.
● Will require re-registration with the supervisor to obtain a new license file.
Which three statements about collector communication with the FortiSIEM cluster are true? (Choose three.)
- A . The only communication between the collector and the supervisor is during the registration process.
- B . Collectors communicate periodically with the supervisor node.
- C . The supervisor periodically checks the health of the collector.
- D . The supervisor does not initiate any connections to the collector node.
- E . Collectors upload event data to any node in the worker upload list, but report their health directly to the supervisor node.
In the context of incident remediation, how can FortiSOAR assist?
- A . By providing a platform for team communication during an incident?
- B . By automating specific response actions based on pre-defined playbooks?
- C . By archiving older logs to save storage space?
- D . By orchestrating actions across multiple security tools in the environment?
Refer to the exhibit.
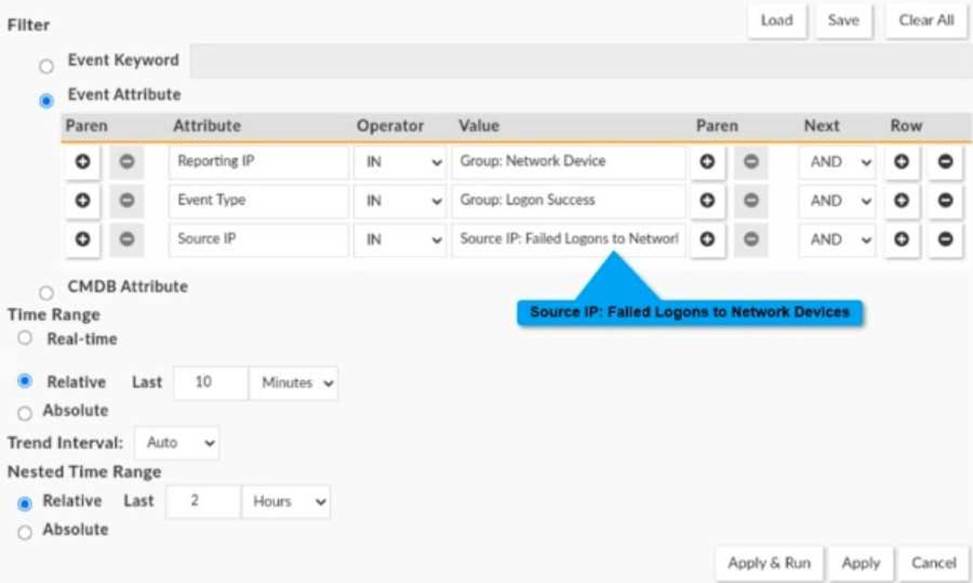
Consider a nested event query where both inner and outer queries are event queries.
Reporting IP is selected from the CMDB group Network Device, Event Type is selected from the CMDB group Logon Success, and Source IP is selected from the report Failed Logons to Network Devices.
An administrator is about to execute the nested query. The report time ranges must be set before execution.
The Nested Time Range will be applied to which attributes?
- A . The nested time range will be configured for the Reporting IP attribute.
- B . The nested time range will be configured for the Reporting IP and Event Type attributes.
- C . The nested time range will be configured for the Source IP attribute.
- D . The nested time range will be configured for the Event Type attribute.
C
Explanation:
In a nested event query, the inner query executes first, and its results feed into the outer query. Since the Source IP comes from the report "Failed Logons to Network Devices", which is part of the inner query, the nested time range applies to it. The other attributes, Reporting IP and Event Type, belong to the outer query and are not affected by the nested time range.
Refer to the exhibit.
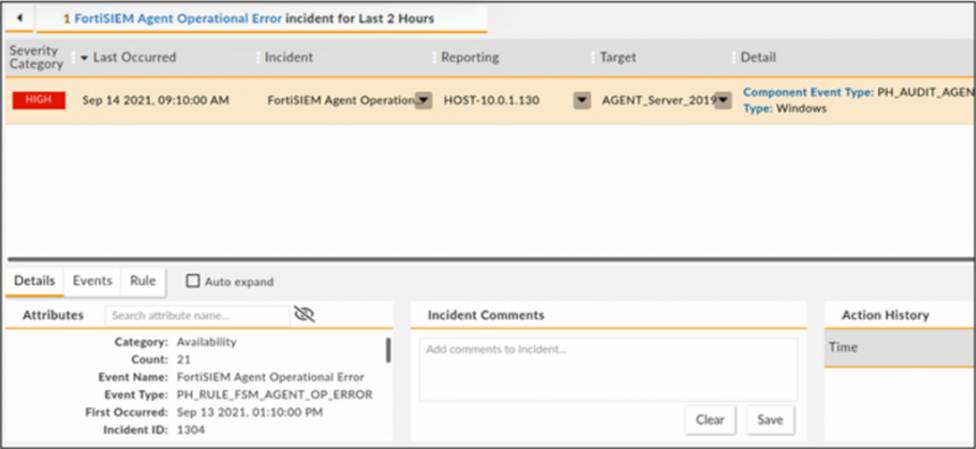
How long has the UEBA agent been operationally down?
- A . 21 Hours
- B . 9 Hours
- C . 20 Hours
- D . 2 Hours
Refer to the exhibit.
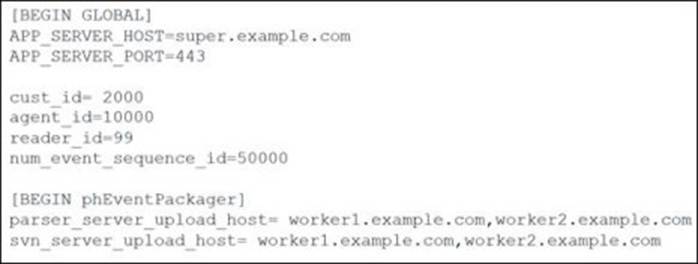
What is the collector ID?
- A . 2000
- B . 50000
- C . 99
- D . 10000
How does the MITRE ATT&CK® framework assist cybersecurity professionals?
- A . By providing a sales strategy for security products?
- B . By detailing a list of recommended security vendors?
- C . By offering insights into attacker behavior and techniques?
- D . By setting up firewall rules for different environments?
Refer to the exhibit.
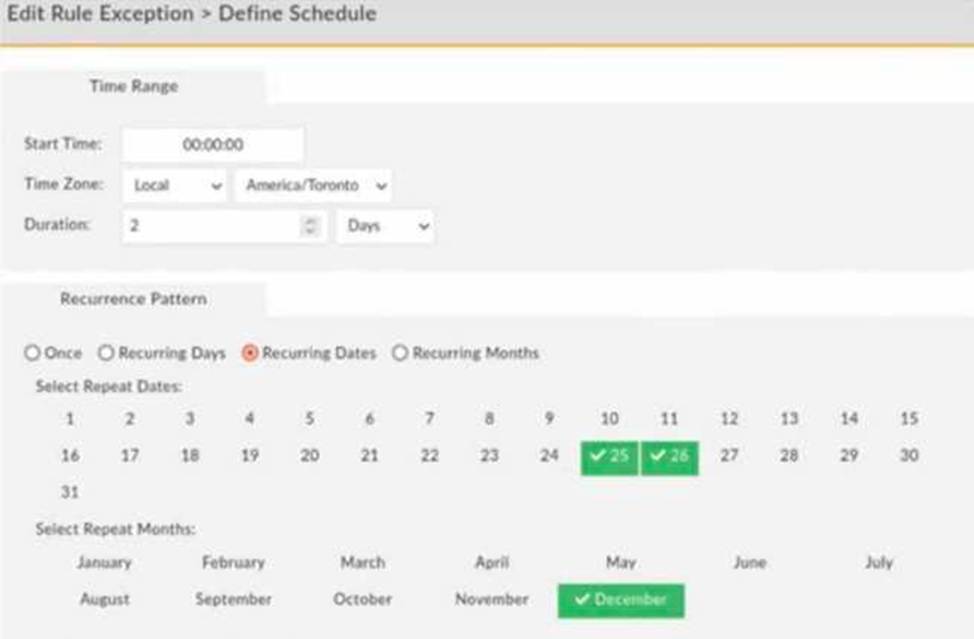
An administrator applies the rule exception shown in the exhibit.
How does this configuration impact the incident generation for that rule?
- A . Incidents will not be generated during the specified period.
- B . Incidents will be generated only during the specified period.
- C . Incidents will be generated without triggering an email alert during the specified period.
- D . Events will not be processed by the rule during the specified period.
A
Explanation:
From the exhibit, the rule exception is set for:
● Time Range: Starts at 00:00:00
● Duration: 2 days
● Recurrence Pattern: December 25th and December 26th
This means that during these two days (every year in December), the rule will not trigger incidents.
Rule exceptions temporarily suppress incident generation during the specified period.
Events are still processed, but no incidents are generated.
