Practice Free FCSS_ADA_AR-6.7 Exam Online Questions
Where are the SQLite databases that are used for the baselining, stored?
- A . /opt/phoenix/cache
- B . /opt/phoenix/bin
- C . /opt/phoenix/config
- D . /opt/phoenix/delta
A
Explanation:
In FortiSIEM, SQLite databases used for baselining are stored in the /opt/phoenix/cache directory. This location is used for temporary storage and caching of profile data that is essential for anomaly detection and trend analysis.
● Baselining involves analyzing historical data to determine expected behavior patterns.
● SQLite databases store aggregated statistics, which are referenced during rule evaluations.
● The cache directory allows quick access to these values without querying the main database repeatedly.
Where are the SQLite databases that are used for the baselining, stored?
- A . /opt/phoenix/cache
- B . /opt/phoenix/bin
- C . /opt/phoenix/config
- D . /opt/phoenix/delta
A
Explanation:
In FortiSIEM, SQLite databases used for baselining are stored in the /opt/phoenix/cache directory. This location is used for temporary storage and caching of profile data that is essential for anomaly detection and trend analysis.
● Baselining involves analyzing historical data to determine expected behavior patterns.
● SQLite databases store aggregated statistics, which are referenced during rule evaluations.
● The cache directory allows quick access to these values without querying the main database repeatedly.
Refer to the exhibit.
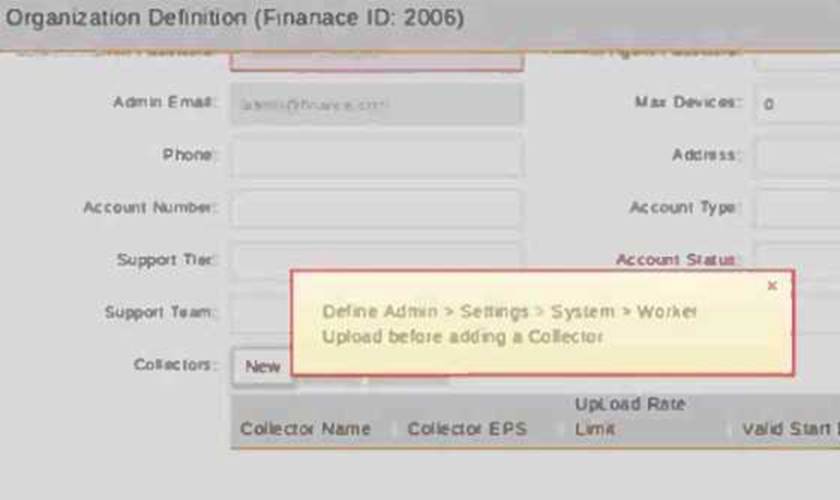
A service provider does not have a dedicated worker in the cluster, but still wants to add a collector to an organization.
What option does the administrator have?
- A . Define a pseudo address as a worker IP address
- B . Install a worker
- C . Ignore the warning and continue adding the collector
- D . Define the supervisor IP address as a worker unload address
D
Explanation:
In FortiSIEM, collectors need to upload event logs to a worker node for processing.
However, if there is no dedicated worker, the supervisor can function as the worker to receive data.
● The error message suggests that a worker upload address must be defined before adding a collector.
● Since there is no dedicated worker, the administrator can set the Supervisor IP as the upload destination to enable log collection.
Refer to the exhibit.
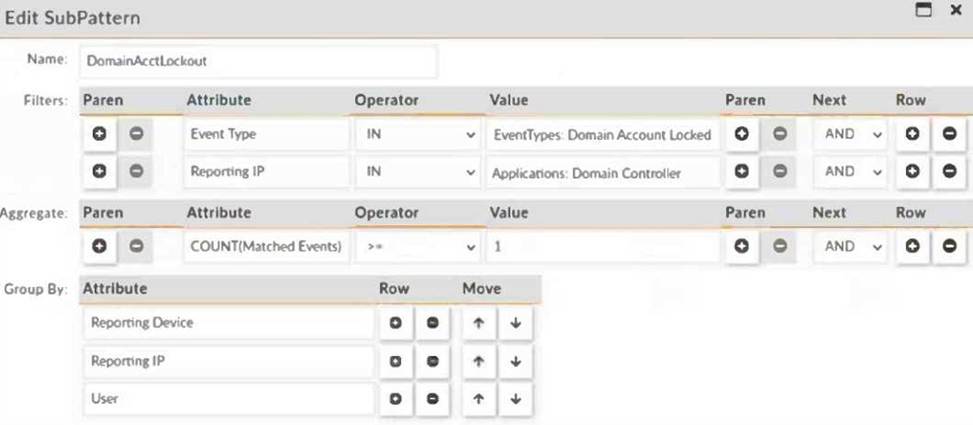
Consider the five account locked events received by FortiSIEM from domain controllers within the last 10 minutes (ten minutes is the evaluation window for the subpattern DomainAcctLockout):
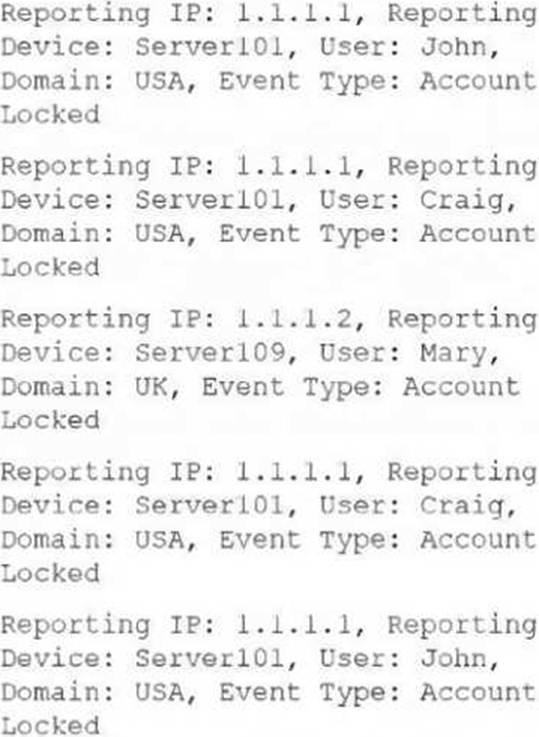
If you look for one or more matching events and groupings by the same reporting IP address, reporting device, and user, how many incidents are created?
- A . 3
- B . 4
- C . 2
- D . 1
C
Explanation:
The rule groups events by Reporting IP, Reporting Device, and User. Let’s analyze the five events:
Events Received:
Which of the following is a primary reason to deploy FortiSIEM agents on both Windows and Linux platforms?
- A . To cover a diverse range of operating systems in an environment.
- B . To increase the speed of the SOC server.
- C . To provide redundancy in case one platform fails.
- D . To prevent users from installing unauthorized software.
Refer to the exhibit.
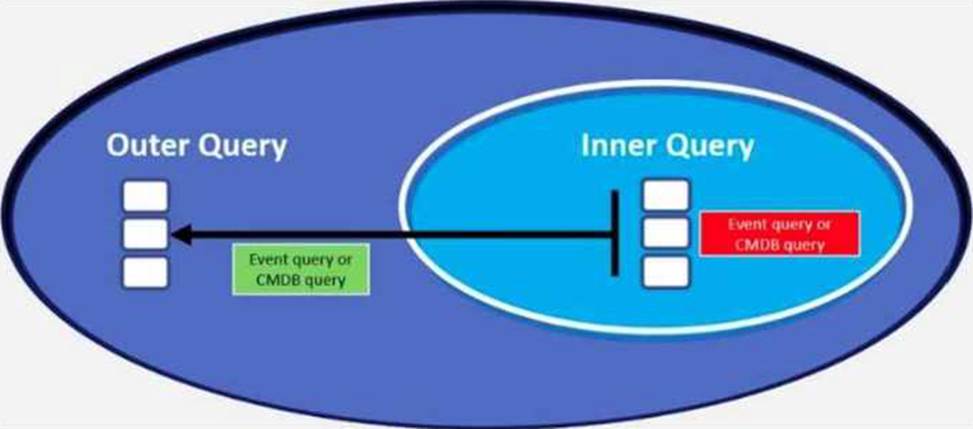
Which scenario is not a supported nested query scenario?
- A . The outer query is the event query, and the inner query is the event query.
- B . The outer query is the event query, and the inner query is the CMDB query.
- C . The outer query is the CMDB query, and the inner query is the event query.
- D . The outer query is the CMDB query, and the inner query is the CMDB query.
D
Explanation:
FortiSIEM does not allow CMDB queries to be nested within other CMDB queries. CMDB data is static information, and nesting would not add value or function properly in query execution.
Refer to the exhibit.

Which scenario is not a supported nested query scenario?
- A . The outer query is the event query, and the inner query is the event query.
- B . The outer query is the event query, and the inner query is the CMDB query.
- C . The outer query is the CMDB query, and the inner query is the event query.
- D . The outer query is the CMDB query, and the inner query is the CMDB query.
D
Explanation:
FortiSIEM does not allow CMDB queries to be nested within other CMDB queries. CMDB data is static information, and nesting would not add value or function properly in query execution.
FortiSOAR is primarily used for:
- A . Storing large amounts of data?
- B . Streamlining administrative tasks like adding new users?
- C . Automating response actions to security incidents?
- D . Designing network topologies?
How can you customize the AI model on FortiSIEM?
- A . Retrain the AI model
- B . Reconfigure UEBA rules
- C . Adjust risk weighting for UEBA tags
- D . Adjust number of samples collected by the UEBA agents
C
Explanation:
FortiSIEM’s User and Entity Behavior Analytics (UEBA) uses AI-driven modeling to detect anomalies and security risks based on user activity. The risk weighting for UEBA tags allows customization of the AI model by prioritizing certain behaviors or indicators over others.
Adjusting risk weightings fine-tunes how the AI model evaluates risk, helping organizations align detection sensitivity with their security policies. This provides a customized risk scoring mechanism without requiring full AI retraining.
Which function of Linux is used by FortiSIEM for collecting logs?
- A . aureport
- B . ausearch
- C . autrace
- D . auditd
