Practice Free FCP_FGT_AD-7.4 Exam Online Questions
What is the effect of enabling auto-negotiate on the phase 2 configuration of an IPsec tunnel?
- A . FortiGate automatically negotiates different local and remote addresses with the remote peer.
- B . FortiGate automatically negotiates a new security association after the existing security association expires.
- C . FortiGate automatically negotiates different encryption and authentication algorithms with the remote peer.
- D . FortiGate automatically brings up the IPsec tunnel and keeps it up, regardless of activity on the IPsec tunnel.
D
Explanation:
When IPsec SAs expire, FortiGate needs to negotiate new SAs to continue sending and receiving traffic over the IPsec tunnel. Technically, FortiGate deletes the expired SAs from the respective phase 2 selectors, and installs new ones. If IPsec SA renegotiation takes too much time, then FortiGate might drop interesting traffic because of the absence of active SAs. To prevent this, you can enable Auto-negotiate. When you do this, FortiGate not only negotiates new SAs before the current SAs expire, but it also starts using the new SAs right away. The latter prevents traffic disruption by IPsec SA renegotiation. Enable auto-negotiate by default enabling auto-keep-alive too which brings up tunnel automatically. Answer B is little bit tricky, auto-negotiate will negotiate new SA "before" existing SA expired not "after" existing SA expired.
An administrator needs to create a tunnel mode SSL-VPN to access an internal web server from the Internet. The web server is connected to port1. The Internet is connected to port2. Both interfaces belong to the VDOM named Corporation.
What interface must be used as the source for the firewall policy that will allow this traffic?
- A . ssl.root
- B . ssl.Corporation
- C . port2
- D . port1
B
Explanation:
ssl.Corporation
If you are working within a specific VDOM named "Corporation," and the SSL VPN is associated with that VDOM, then the correct choice is:
B. ssl.Corporation
Using the "ssl.Corporation" interface as the source for the firewall policy makes sense in the context of a VDOM-specific SSL VPN.
Refer to the exhibit.
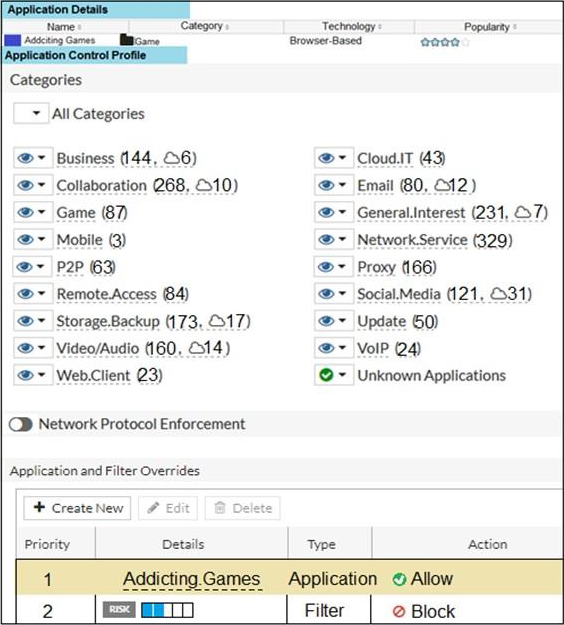
A user located behind the FortiGate device is trying to go to http://www.addictinggames.com (Addicting.Games). The exhibit shows the application detains and application control profile.
Based on this configuration, which statement is true?
- A . Addicting.Games will be blocked, based on the Filter Overrides configuration.
- B . Addicting.Games will be allowed only if the Filter Overrides action is set to Learn.
- C . Addicting.Games will be allowed, based on the Categories configuration.
- D . Addicting.Games will be allowed, based on the Application Overrides configuration.
D
Explanation:
Addicting.Games will be allowed, based on the Application Overrides configuration.
Based on the Scan order. Application and Filter overrides>>Category.
Application and Filter overrides follows the same rules as firewall policy. Application override will be considered first.
Refer to the exhibits.
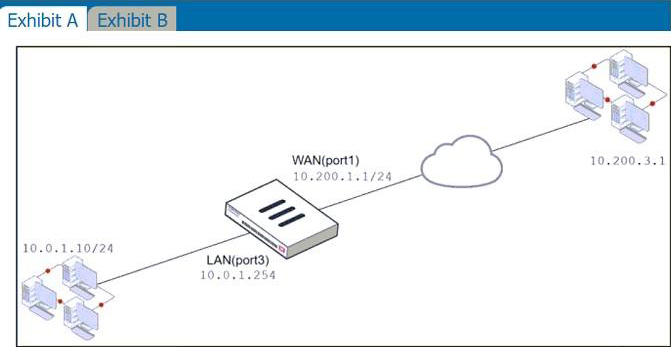
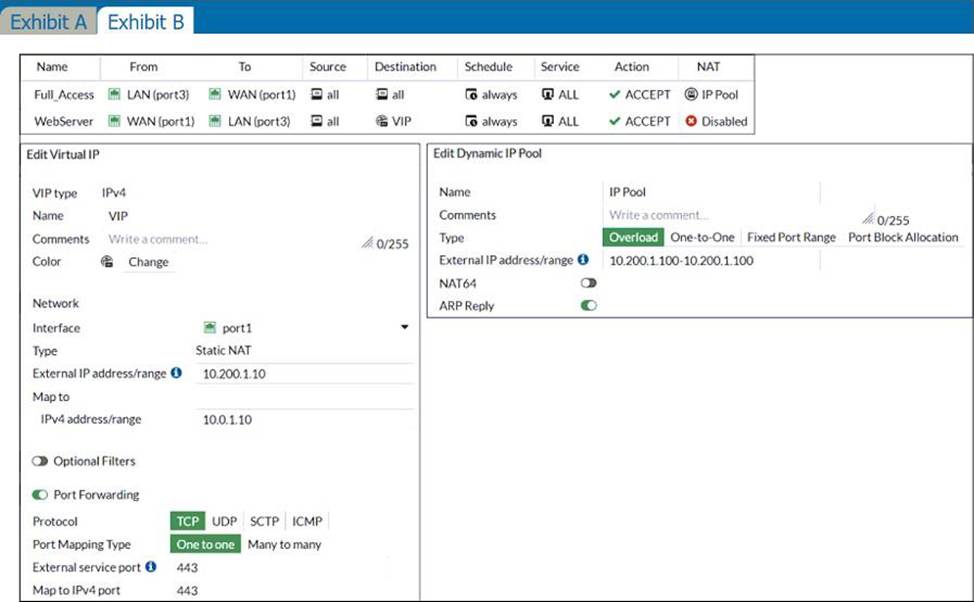
The exhibits contain a network diagram, and virtual IP, IP pool, and firewall policies configuration information.
The WAN (port1) interface has the IP address 10.200.1.1/24.
The LAN (port3) interface has the IP address 10.0.1.254/24.
The first firewall policy has NAT enabled using IP pool.
The second firewall policy is configured with a VIP as the destination address.
Which IP address will be used to source NAT (SNAT) the internet traffic coming from a workstation with the IP address 10.0.1.10?
- A . 10.200.1.1
- B . 10.0.1.254
- C . 10.200.1.10
- D . 10.200.1.100
D
Explanation:
From LAN to WAN, the Source NAT will use the IPPOOL with address configured 10.200.1.100 Destination NAT, from WAN to LAN, will use the VIP
The question says SNAT, so the only correct answer here (looking at the IP Pool) is D.
(Step 2): FortiGate uses as NAT IP the external IP address defined in the VIP when performing SNAT on all egress traffic sourced from the mapped address in the VIP, provided the matching firewall policy has NAT enabled.
Note that you can override the behavior described in step 2 by using an IP pool.
Reference: https://kb.fortinet.com/kb/documentLink.do?externalID=FD44529
Examine this PAC file configuration.
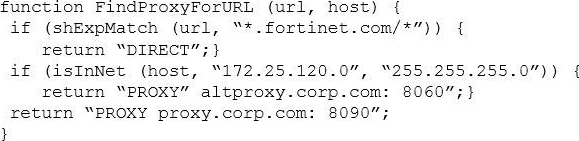
Which of the following statements are true? (Choose two.)
- A . Browsers can be configured to retrieve this PAC file from the FortiGate.
- B . Any web request to the 172.25. 120.0/24 subnet is allowed to bypass the proxy.
- C . All requests not made to Fortinet.com or the 172.25. 120.0/24 subnet, have to go through altproxy.corp.com: 8060.
- D . Any web request fortinet.com is allowed to bypass the proxy.
A, D
Explanation:
The command direct bypass the proxy and it is a standard for pac files. And browsers can download de pac file from any server/fortigate.
FortiGate is operating in NAT mode and has two physical interfaces connected to the LAN and DMZ networks respectively.
Which two statements are true about the requirements of connected physical interfaces on FortiGate? (Choose two.)
- A . Both interfaces must have the interface role assigned
- B . Both interfaces must have directly connected routes on the routing table
- C . Both interfaces must have DHCP enabled
- D . Both interfaces must have IP addresses assigned
B, D
Explanation:
Both interfaces must have directly connected routes on the routing table
In NAT mode, each interface must have a corresponding entry in the routing table, typically as a directly connected route, to route traffic between them effectively. Both interfaces must have IP addresses assigned
In NAT mode, each interface must have an IP address to participate in routing and NAT operations.
The IP addresses allow the FortiGate to forward traffic between different network segments.
Which CLI command will display sessions both from client to the proxy and from the proxy to the servers?
- A . diagnose wad session list
- B . diagnose wad session list | grep hook-pre&&hook-out
- C . diagnose wad session list | grep hook=pre&&hook=out
- D . diagnose wad session list | grep "hook=pre"&"hook=out"
A
Explanation:
diagnose wad session list
Running the diagnose wad session list command will indeed display the sessions managed by the Web Application Firewall (WAF) module, and you can review the information in the output to analyze traffic from the client to the proxy and from the proxy to the servers.
A FortiGate firewall policy is configured with active authentication however, the user cannot authenticate when accessing a website.
Which protocol must FortiGate allow even though the user cannot authenticate?
- A . ICMP
- B . DNS
- C . DHCP
- D . LDAP
B
Explanation:
An administrator configures FortiGuard servers as DNS servers on FortiGate using default settings.
What is true about the DNS connection to a FortiGuard server?
- A . It uses UDP 8888.
- B . It uses DNS over HTTPS.
- C . It uses DNS over TLS.
- D . It uses UDP 53.
C
Explanation:
By default, DNS queries to FortiGuard servers use UDP port 53.
An organization’s employee needs to connect to the office through a high-latency internet connection.
Which SSL VPN setting should the administrator adjust to prevent the SSL VPN negotiation failure?
- A . Change the session-ttl.
- B . Change the login-timeout.
- C . Change the idle-timeout.
- D . Change the udp-idle-timer.
B
Explanation:
Change the login-timeout.
Set up timers to avoid logouts when SSL VPN users are connected over high latency connections. When connected to SSL VPN over high latency connections, FortiGate can time out the client before the client can finish the negotiation process, such as DNS lookup and time to enter a token. Two new CLI commands under "config vpn ssl settings" have been added to address this. The first command "set login-timeout" allows you to set up the login timeout, replacing the previous hard timeout value. The second command "set dtls-hello-timeout" allows you to set up the maximum DTLS hello timeout for SSL
VPN connections.
