Practice Free FCP_FGT_AD-7.4 Exam Online Questions
What types of traffic and attacks can be blocked by a web application firewall (WAF) profile? (Choose three.)
- A . Traffic to botnetservers
- B . Traffic to inappropriate web sites
- C . Server information disclosure attacks
- D . Credit card data leaks
- E . SQL injection attacks
C,D,E
Explanation:
The types of traffic and attacks that can be blocked by a Web Application Firewall (WAF) profile include:
C. Server information disclosure attacks: A WAF can help block attacks attempting to disclose sensitive information about the server.
D. Credit card data leaks: A WAF can be configured to detect and block attempts to leak credit card or other sensitive data.
E. SQL injection attacks: WAFs are effective in blocking SQL injection attacks, where attackers attempt to manipulate a web application’s database by injecting malicious SQL code. Options A and B are not typically associated with the primary functions of a WAF:
Which three options are the remote log storage options you can configure on FortiGate? (Choose three.)
- A . FortiSandbox
- B . FortiCloud
- C . FortiSIEM
- D . FortiCache
- E . FortiAnalyzer
B,C,E
Explanation:
B. FortiCloud
C. FortiSIEM
E. FortiAnalyzer
You can configure FortiGate to store logs on syslog servers, FortiCloud, FortiSIEM, FortiAnalyzer, or FortiManager. These logging devices can also be used as a backup solution. Whenever possible, it is preferred to store logs externally.
If storing logs locally does not fit your requirements, you can store logs externally. You can configure FG to store logs on syslog servers, FortiCloud, FortiSIEM, FortiAnalyzer or FortiManager. These logging devices can also be used as a backup solution.
An administrator wants to block https://www.example.com/videos and allow all other URLs on the website.
What are two configuration changes that the administrator can make to satisfy the requirement? (Choose two.)
- A . Configure web override for the URL and select a blocked FortiGuard subcategory
- B . Enable full SSL inspection
- C . Configure a video filter profile to block the URL
- D . Configure a static URL filter entry for the URL and select Block as the action
B,D
Explanation:
If the goal is to block the specific URL https://www.example.com/videos and allow all other URLs on the website, the correct configuration changes are:
B. Enable full SSL inspection.
Enabling full SSL inspection allows the FortiGate to inspect and filter HTTPS traffic, including the specific URL https://www.example.com/videos.
D. Configure a static URL filter entry for the URL and select Block as the action.
Create a static URL filter entry for the specific URL https://www.example.com/videos and set the action to Block. This will block access to the specified URL.
Enabling full SSL inspection is necessary to inspect and filter HTTPS traffic effectively, including the specific URL within the encrypted traffic.
So, the correct choices are B and D.
Which three methods can you use to deliver the token code to a user who is configured to use two-factor authentication? (Choose three.)
- A . Instant message app
- B . FortiToken
- C . Email
- D . Voicemail message
- E . SMS text message
B,C,E
Explanation:
The three methods that can be used to deliver the token code to a user configured to use two-factor authentication are:
B. FortiToken
FortiToken is a physical or software-based token that generates time-based or event-based codes for two-factor authentication.
C. Email
The token code can be delivered to the user via email, where the user has access to the code through their email account.
E. SMS text message
The token code can be sent to the user as a text message (SMS) to their mobile device.
These methods provide flexibility in delivering the token code to users for two-factor authentication.
So, the correct choices are B, C, and E.
What are two benefits of flow-based inspection compared to proxy-based inspection? (Choose two.)
- A . FortiGate uses fewer resources.
- B . FortiGate performs a more exhaustive inspection on traffic.
- C . FortiGate adds less latency to traffic.
- D . FortiGate allocates two sessions per connection.
A,C
Explanation:
Which of the following SD-WAN load Cbalancing method use interface weight value to distribute traffic? (Choose two.)
- A . Source IP
- B . Spillover
- C . Volume
- D . Session
C,D
Explanation:
Session is the name of a mode. Spillover is not the real name for SD-WAN that is in ECMP. Spillover is called Usage in SD-WAN.
The correct load balancing method that uses interface weight values to distribute traffic is:
C. Volume
D. Session
Both Volume-based and Session-based load balancing methods in SD-WAN can use interface weight values to distribute traffic proportionally based on the weights assigned to each interface.
The FortiGate uses the weight that you assign to each interface to calculate a percentage of the total sessions that are allowed to connect through each interface.
The FortiGate uses the volume weight that you assign to each interface to calculate a percentage of the total bandwidth that’s allowed to go through each interface.
A network administrator enabled antivirus and selected an SSL inspection profile on a firewall policy. When downloading an EICAR test file through HTTP, FortiGate detects the virus and blocks the file. When downloading the same file through HTTPS, FortiGate does not detect the virus and does not block the file, allowing it to be downloaded.
The administrator confirms that the traffic matches the configured firewall policy.
What are two reasons for the failed virus detection by FortiGate? (Choose two.)
- A . The website is exempted from SSL inspection.
- B . The EICAR test file exceeds the protocol options oversize limit.
- C . The selected SSL inspection profile has certificate inspection enabled.
- D . The browser does not trust the FortiGate self-signed CA certificate.
A,C
Explanation:
Two possible explanations for FortiGate’s failure to detect the virus are:
Which security fabric feature causes an event trigger to monitor the network when a threat is detected?
- A . Security rating
- B . Optimization
- C . Automation stiches
- D . Fabric connectors
C
Explanation:
Automation stitches
In the context of the Fortinet Security Fabric, automation stitches are responsible for orchestrating responses to security events. When a threat is detected, automation stitches can trigger events to monitor the network, coordinate responses, and ensure a synchronized defense across the entire security fabric. Therefore, option C is the correct answer.
Each automation stitch pairs an event trigger and one or more actions, it allows you to monitor your network and take appropiate action when SecFabric detects a threat.
Refer to the exhibits.
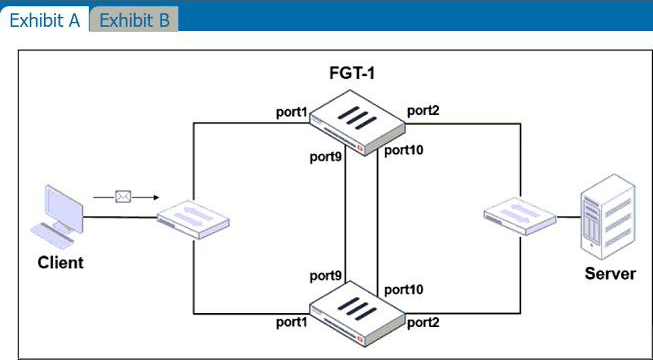
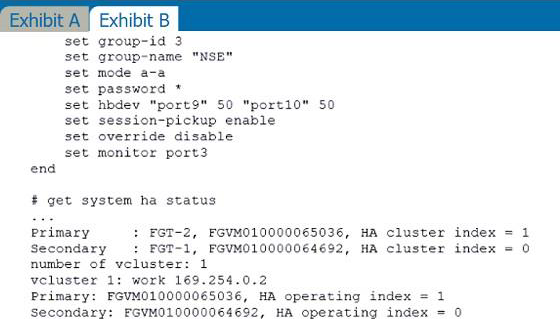
Exhibit A shows a topology for a FortiGate HA cluster that performs proxy-based inspection on traffic.
Exhibit B shows the HA configuration and the partial output of the get system ha status command.
Based on the exhibits, which two statements about the traffic passing through the cluster are true? (Choose two.)
- A . For non-load balanced connections, packets forwarded by the cluster to the server contain the virtual MAC address of port2 as source.
- B . The traffic sourced from the client and destined to the server is sent to FGT-1.
- C . The cluster can load balance ICMP connections to the secondary.
- D . For load balanced connections, the primary encapsulates TCP SYN packets before forwarding them
to the secondary.
A,D
Explanation:
A: Non load balance: traffic enters port1 and go out port2 from FGT1. FGT2 is in primary mode
D: In proxy inspection mode, SYN packet goes to FGT1 port1. It is then forwarded to FGT2. the source MAC address of the packet is changed to the physical MAC address of port1 on the primary and the destination MAC address to the physical MAC address of port1 on the secondary. This is also known as MAC address rewrite. In addition, the primary encapsulates the packet in an Ethernet frame type 0x8891. The encapsulation is done only for the first packet of a load balanced session
What is the primary FortiGate election process when the HA override setting is disabled?
- A . Connected monitored ports > System uptime > Priority > FortiGate Serial number
- B . Connected monitored ports > HA uptime > Priority > FortiGate Serial number
- C . Connected monitored ports > Priority > HA uptime > FortiGate Serial number
- D . Connected monitored ports > Priority > System uptime > FortiGate Serial number
B
Explanation:
If Override DISABLED then: ports > HA Uptime > Priority > SN.
If Overrrid ENABLED then: ports > Priority > HA Uptime > SN.
The FortiGate election process when the HA override setting is disabled follows the criteria you provided:
Connected monitored ports: The FortiGate with more connected monitored ports is preferred.
HA uptime: The FortiGate with the longer High Availability (HA) uptime (less recently rebooted in HA) is preferred.
Priority: Priority is used as a tiebreaker. If two FortiGates have the same number of connected monitored ports and the same HA uptime, the one with the higher priority is preferred.
FortiGate Serial number: The FortiGate Serial number is used as a final tiebreaker if all other criteria are the same.
