Practice Free FCP_FGT_AD-7.4 Exam Online Questions
Refer to the exhibits.
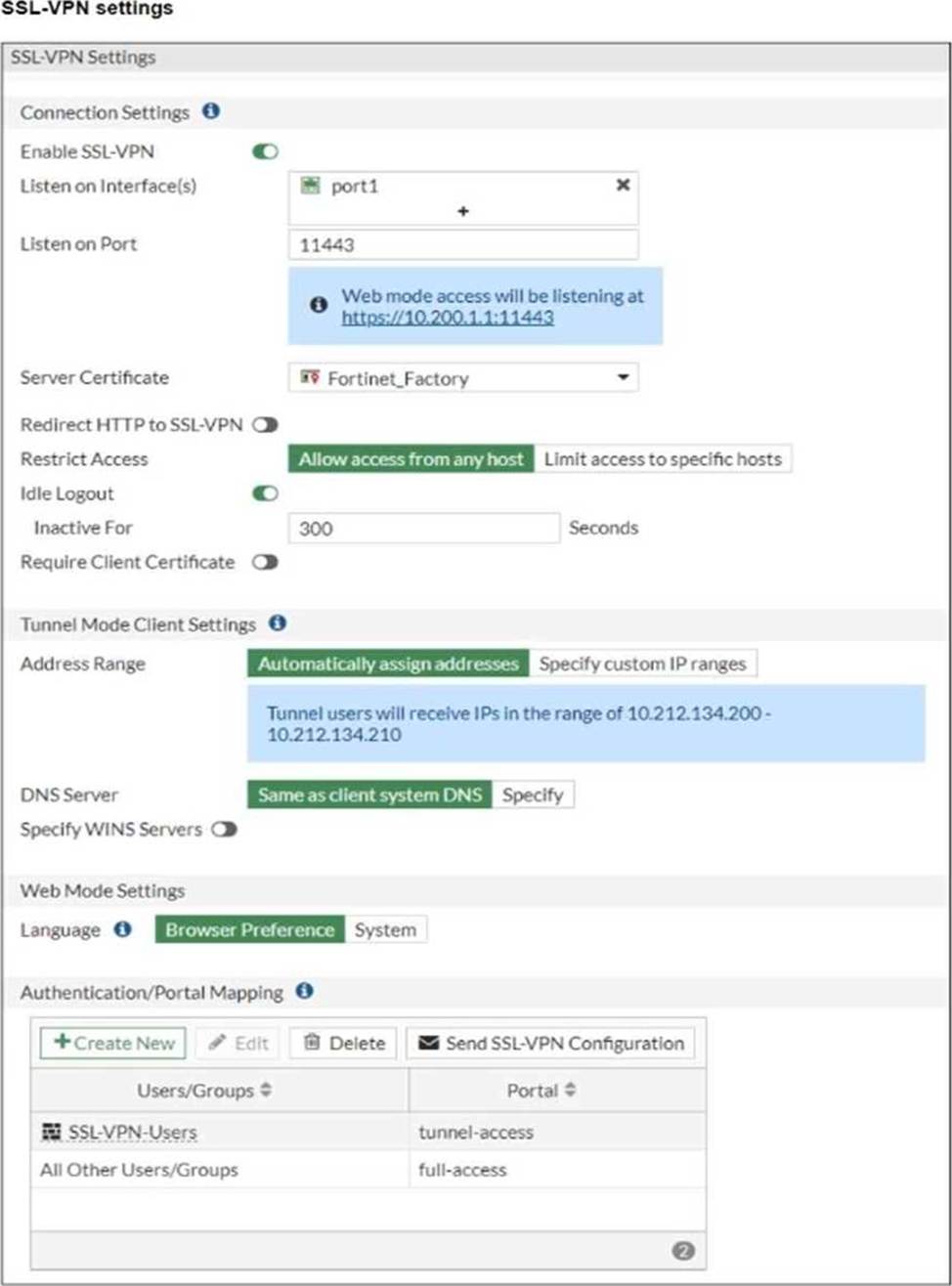
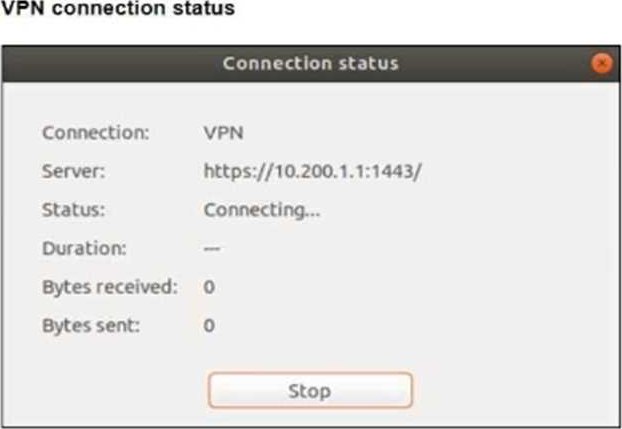
The SSL VPN connection fails when a user attempts to connect to it.
What should the user do to successfully connect to the SSL VPN?
- A . Change the SSL VPN portal to the tunnel.
- B . Change the idle timeout.
- C . Change the server IP address.
- D . Change the SSL VPN port on the client.
D
Explanation:
The SSL VPN is configured to listen on port 11443 on the FortiGate device, as shown in the SSL VPN settings in the exhibit. However, the user is attempting to connect to the server using port 1443, as displayed in the VPN connection status. The mismatch between the ports is causing the connection failure. To resolve this, the user should change the client configuration to use port 11443 to match the FortiGate SSL VPN configuration.
Refer to exhibit.
An administrator configured the web filtering profile shown in the exhibit to block access to all social networking sites except Twitter. However, when users try to access twitter.com, they are redirected to a FortiGuard web filtering block page.
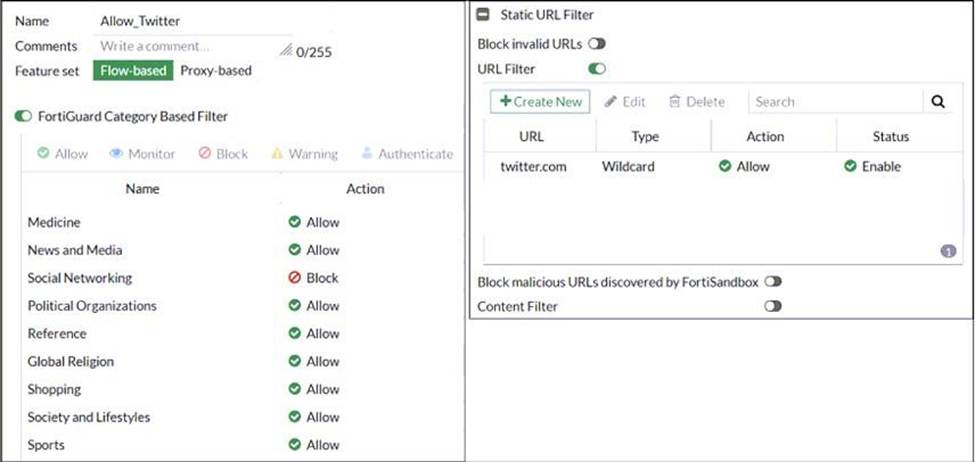
Based on the exhibit, which configuration change can the administrator make to allow Twitter while blocking all other social networking sites?
- A . On the FortiGuard Category Based Filter configuration, set Action to Warning for Social Networking.
- B . On the Static URL Filter configuration, set Type to Simple.
- C . On the Static URL Filter configuration, set Action to Exempt.
- D . On the Static URL Filter configuration, set Action to Monitor.
C
Explanation:
C. On the Static URL Filter configuration, set Action to Exempt.
Based on the exhibit, the administrator has configured the FortiGuard Category Based Filter to block access to all social networking sites, and has also configured a Static URL Filter to block access to twitter.com. As a result, users are being redirected to a block page when they try to access twitter.com.
To allow users to access twitter.com while blocking all other social networking sites, the administrator can make the following configuration change:
On the Static URL Filter configuration, set Action to Exempt: By setting the Action to Exempt, the administrator can override the block on twitter.com that was specified in the FortiGuard Category Based Filter. This will allow users to access twitter.com, while all other social networking sites will still be blocked.
Note:
Tested this in a lab environment and to make this work as stated in the question the Exempt action is the only way to go, and also *.twimg.com will has to be added to the URL Filter with an Exempt action for this situation to really work!
Allow: Access is permitted. Traffic is passed to remaining operations, including FortiGuard web filter, web content filter, web script filters, and antivirus scanning.
Exempt: Allows traffic from trusted sources to bypass all security inspections.
The HTTP inspection process in web filtering follows a specific order when multiple features are enabled in the web filter profile.
What order must FortiGate use when the web filter profile has features enabled, such as safe search?
- A . DNS-based web filter and proxy-based web filter
- B . Static URL filter, FortiGuard category filter, and advanced filters
- C . Static domain filter, SSL inspection filter, and external connectors filters
- D . FortiGuard category filter and rating filter
B
Explanation:
The correct order for the HTTP inspection process in web filtering, specifically when features like safe search are enabled in the web filter profile, is:
B. Static URL filter, FortiGuard category filter, and advanced filters
This means that the FortiGate device will first check against the Static URL filter, followed by the FortiGuard category filter, and then any additional advanced filters configured in the web filter profile. This sequence allows for a systematic evaluation of the URL against different criteria, ensuring comprehensive web filtering.
The HTTP Inspection Order (Static URL Filter -> FortiGuard Category Filter -> Advanced Filters)
Which two statements about antivirus scanning in a firewall policy set to proxy-based inspection mode, are true? (Choose two.)
- A . A file does not need to be buffered completely before it is moved to the antivirus engine for scanning.
- B . The client must wait for the antivirus scan to finish scanning before it receives the file.
- C . FortiGate sends a reset packet to the client if antivirus reports the file as infected.
- D . If a virus is detected, a block replacement message is displayed immediately.
B,D
Explanation:
In a firewall policy set to proxy-based inspection mode:
B. The client must wait for the antivirus scan to finish scanning before it receives the file.
In proxy-based inspection, the client may need to wait for the antivirus scan to complete before receiving the file. The file may need to be fully scanned before being delivered to the client, depending on the specific configuration and circumstances.
D. If a virus is detected, a block replacement message is displayed immediately.
If a virus is detected during the antivirus scan in proxy-based inspection mode, FortiGate can generate a block replacement message immediately, informing the user that the file is infected. So, both statements B and D are valid in the context of proxy-based inspection mode.
Which statement about the deployment of the Security Fabric in a multi-VDOM environment is true?
- A . Downstream devices can connect to the upstream device from any of their VDOMs
- B . Each VDOM in the environment can be part of a different Security Fabric
- C . VDOMs without ports with connected devices are not displayed in the topology
- D . Security rating reports can be run individually for each configured VDOM
B
Explanation:
In a multi-VDOM environment, each VDOM can be treated as an independent virtual firewall, and each VDOM can belong to a separate Security Fabric. This allows administrators to configure and manage separate Security Fabrics for different VDOMs, providing flexibility in managing security policies and fabric connections across virtual domains.
An administrator is configuring an Ipsec between site A and site B. The Remotes Gateway setting in both sites has been configured as Static IP Address. For site A, the local quick mode selector is 192.16.1.0/24 and the remote quick mode selector is 192.16.2.0/24.
How must the administrator configure the local quick mode selector for site B?
- A . 192.16.3.0/24
- B . 192.16.2.0/24
- C . 192.16.1.0/24
- D . 192.16.0.0/8
B
Explanation:
The local quick mode selector for site B should be configured to match the remote quick mode selector of site
Which two protocol options are available on the CLI but not on the GUI when configuring an SD-WAN Performance SLA? (Choose two.)
- A . udp-echo
- B . DNS
- C . TWAMP
- D . ping
A,C
Explanation:
The correct answers are:
A network administrator is configuring a new IPsec VPN tunnel on FortiGate. The remote peer IP address is dynamic. In addition, the remote peer does not support a dynamic DNS update service.
Which type of remote gateway should the administrator configure on FortiGate for the new IPsec VPN tunnel to work?
- A . Pre-shared key
- B . Dialup user
- C . Dynamic DNS
- D . Static IP address
B
Explanation:
In a scenario where the remote peer IP address is dynamic, and the remote peer does not support a dynamic DNS update service, the appropriate choice for configuring the remote gateway on FortiGate is:
B. Dialup user
Configuring the remote gateway as a dialup user allows flexibility for dynamic remote peer IP addresses without relying on dynamic DNS. Dialup user configurations are suitable for scenarios where the remote peer’s IP address may change dynamically, and it is not possible to use a static IP address or dynamic DNS.
The peer IP is not static.
D cannot be correct as the remote peer has a dynamic address so this will not be known to the local side as it may change.
The same goes for dynamic.
PSK is not an option, the answer is B.
When configuring a firewall virtual wire pair policy, which following statement is true?
- A . Any number of virtual wire pairs can be included, as long as the policy traffic direction is the same.
- B . Only a single virtual wire pair can be included in each policy.
- C . Any number of virtual wire pairs can be included in each policy, regardless of the policy traffic direction settings.
- D . Exactly two virtual wire pairs need to be included in each policy.
C
Explanation:
Any number of virtual wire pairs can be included in each policy, regardless of the policy traffic direction settings.
Firewall virtual wire pair policies can include more than a single virtual wire pair. This capability can streamline the policy management process by eliminating the need to create multiple, similiar policies for each virtual wire pair. When creating or modifiying a policy, you can select the traffic direction for each VWP included in the policy.
Note: We tested to create a policy. We can use any number of virtual wire pairs. We can select 3 options in traffic direction: in/out/both.
Refer to the web filter raw logs.
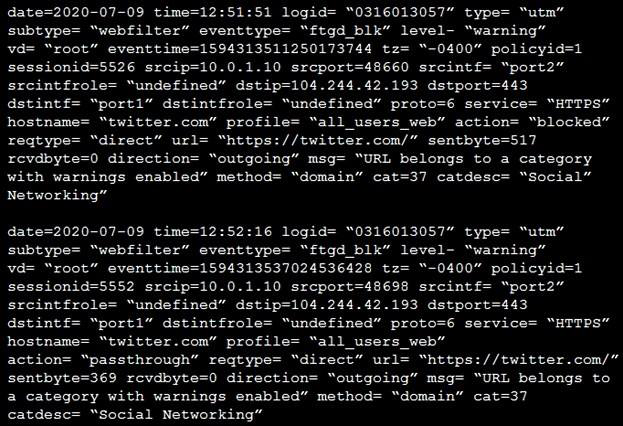
Based on the raw logs shown in the exhibit, which statement is correct?
- A . Access to the social networking web filter category was explicitly blocked to all users.
- B . The action on firewall policy ID 1 is set to warning.
- C . Social networking web filter category is configured with the action set to authenticate.
- D . The name of the firewall policy is all_users_web.
C
Explanation:
C is correct. We have two logs, first with action deny and second with passthrough.
A incorrect – second log shows: action="passthrough".
B incorrect – Firewall action can be allow or deny.
D incorrect – CLI don’t show policy name, only ID.
Remember … action="passthrough" mean that authentication has occurred/
At first attempt from the same IP source connection is blocked, but a warning message is displayed. At the second attempt with the same IP source connection passtrough, so considering the first block and the second pass, the user must authenticate to be granted with access.
