Practice Free FCP_FGT_AD-7.4 Exam Online Questions
Refer to the exhibit.
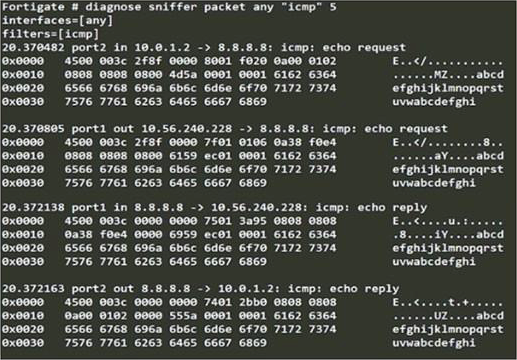
An administrator is running a sniffer command as shown in the exhibit.
Which three pieces of information are included in the sniffer output? (Choose three.)
- A . Interface name
- B . Ethernet header
- C . IP header
- D . Application header
- E . Packet payload
A,C,E
Explanation:
Packet Capture Verbosity Level which is set to 5 in the exhibit, if it was level 6 it should also include ethernet headers. Application headers are never included.
This is Correct:
Packet payload
IP header
Interface name
Sniffer with verbose 5: IP header, IP payload, Port name.
When FortiGate performs SSL/SSH full inspection, you can decide how it should react when it detects an invalid certificate.
Which three actions are valid actions that FortiGate can perform when it detects an invalid certificate? (Choose three.)
- A . Allow & Warning
- B . Trust & Allow
- C . Allow
- D . Block & Warning
- E . Block
A, D, E
Explanation:
When FortiGate performs SSL/SSH full inspection and detects an invalid certificate, there are three valid actions it can take:
Allow & Warning: This action allows the session but generates a warning.
Block & Warning: This action blocks the session and generates a warning.
Block: This action blocks the session without generating a warning.
Actions such as "Trust & Allow" or just "Allow" without additional configurations are not applicable in the context of handling invalid certificates.
Reference: FortiOS 7.4.1 Administration Guide: Configuring SSL/SSH inspection profile
Which two statements are correct about SLA targets? (Choose two.)
- A . You can configure only two SLA targets per one Performance SLA.
- B . SLA targets are optional.
- C . SLA targets are required for SD-WAN rules with a Best Quality strategy.
- D . SLA targets are used only when referenced by an SD-WAN rule.
B,D
Explanation:
B. SLA targets are optional.
D. SLA targets are used only when referenced by an SD-WAN rule.
Incorrect:
View the exhibit.
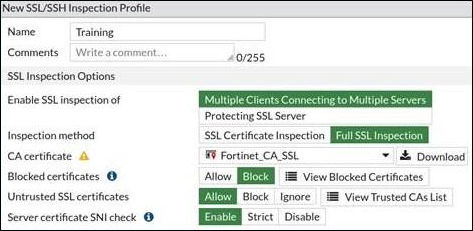
Which two behaviors result from this full (deep) SSL configuration? (Choose two.)
- A . The browser bypasses all certificate warnings and allows the connection.
- B . A temporary trusted FortiGate certificate replaces the server certificate, even when the server certificate is untrusted.
- C . A temporary trusted FortiGate certificate replaces the server certificate when the server certificate is trusted.
- D . A temporary untrusted FortiGate certificate replaces the server certificate when the server certificate is untrusted.
C,D
Explanation:
C. A temporary trusted FortiGate certificate replaces the server certificate when the server certificate is trusted.
D. A temporary untrusted FortiGate certificate replaces the server certificate when the server certificate is untrusted.
In a full (deep) SSL configuration, a temporary untrusted FortiGate certificate replaces the server certificate when the server certificate is untrusted, and a temporary trusted FortiGate certificate replaces the server certificate when the server certificate is trusted.
The behavior that results from this full (deep) SSL configuration is that a temporary untrusted FortiGate certificate replaces the server certificate when the server certificate is untrusted. Additionally, a temporary trusted FortiGate certificate replaces the server certificate when the server certificate is trusted.
Which Security rating scorecard helps identify configuration weakness and best practice violations in your network?
- A . Fabric Coverage
- B . Automated Response
- C . Security Posture
- D . Optimization
C
Explanation:
Security Posture
Description of the three major scorecards is seen in Security fabric > Security rating>Security posture. Security Posture
Identify configuration weaknesses and best practice violations in your deployment.
Fabric Coverage
Identify in your overall network, where Security Fabric can enhance visibility and control. Optimization
Optimize your fabric deployment.
The Security Posture scorecard is designed to identify configuration weaknesses and best practice violations in a network. It assesses the overall security stance of an organization’s network infrastructure by evaluating how well it adheres to established security practices and configurations.
When using the Security Posture scorecard, the goal is to identify areas where the network configuration may be vulnerable or where best practices are not being followed. It helps organizations assess and improve their security posture by highlighting potential weaknesses and areas that require attention.
In contrast, the other options:
An administrator has configured central DNAT and virtual IPs.
Which item can be selected in the firewall policy Destination field?
- A . An IP pool
- B . A VIP object
- C . A VIP group
- D . The mapped IP address object of the VIP object
D
Explanation:
– when central NAT is enabled => put the mapped IP address of the VIP object.
– when central NAT is disabled => put the VIP object.
In the context of central DNAT and virtual IPs in FortiGate, the correct option for the firewall policy
Destination field is:
D. The mapped IP address object of the VIP object
When configuring central DNAT, you typically select the mapped IP address object associated with the VIP object in the firewall policy Destination field. This mapped IP address represents the internal destination to which traffic will be redirected.
So, the correct choice is D.
Refer to the exhibits.
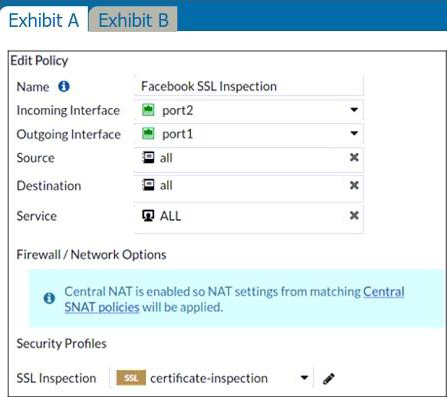
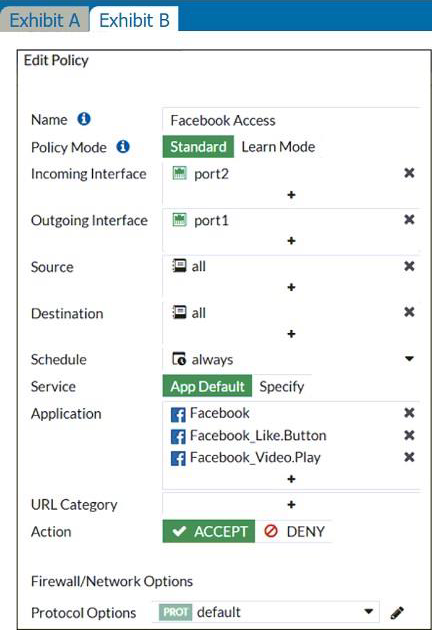
The exhibits show the SSL and authentication policy (Exhibit A) and the security policy (Exhibit B) for Facebook.
Users are given access to the Facebook web application. They can play video content hosted on Facebook, but they are unable to leave reactions on videos or other types of posts.
Which part of the policy configuration must you change to resolve the issue?
- A . Force access to Facebook using the HTTP service.
- B . Make the SSL inspection a deep content inspection.
- C . Add Facebook in the URL category in the security policy.
- D . Get the additional application signatures required to add to the security policy.
B
Explanation:
Needs SSL full inspection.
They can play video (tick) content hosted on Facebook, but they are unable to leave reactions on videos or other types of posts.
This indicate that the rule are partially working as they can watch video but can’t react, i.e. liking the content. So, must be an issue with the SSL inspection rather then adding an app rule.
The lock logo behind Facebook_like.Button indicates that SSL Deep Inspection is Required. All other Application Signatures Facebook and Facebook_Video.Play does not require SSL inspection. Hence that the users can play video content. If you look up the Application Signature for Facebook_like.Button it will say "Requires SSL Deep Inspection".
FortiGate needs to perform full SSL inspection. Without full SSL inspection, FortiGate cannot inspect encrypted traffic.
Which two statements are correct about a software switch on FortiGate? (Choose two.)
- A . It can be configured only when FortiGate is operating in NAT mode
- B . Can act as a Layer 2 switch as well as a Layer 3 router
- C . All interfaces in the software switch share the same IP address
- D . It can group only physical interfaces
A,C
Explanation:
A is correct: "Only supported in NAT mode"
C is correct: "The interfaces share the same IP address and belong to the same broadcast domain.
Incorrect options:
B is incorrect: "Acts Like a traditional Layer 2 switch".
D is incorrect: "Can group multiple physical and wireless interfaces into a single virtual switch Interface"
Can group physical and wireless.
Only works on NAT mode.
Acts like traditional layer 3 switch.
Interfaces share same IP and broadcast domain.
Refer to the exhibit.
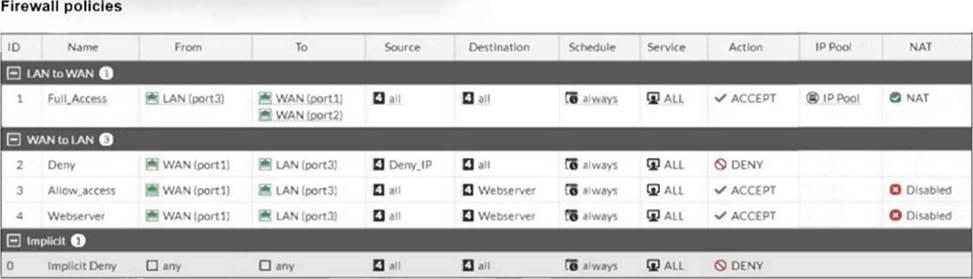
Which statement about this firewall policy list is true?
- A . The Implicit group can include more than one deny firewall policy.
- B . The firewall policies are listed by ID sequence view.
- C . The firewall policies are listed by ingress and egress interfaces pairing view.
- D . LAN to WAN. WAN to LAN. and Implicit are sequence grouping view lists.
C
Explanation:
The firewall policy list in the exhibit is arranged in the "Interface Pair View," where policies are grouped by their incoming (ingress) and outgoing (egress) interface pairs. Each section (LAN to WAN, WAN to LAN, etc.) groups policies based on these interface pairings. This view helps administrators quickly identify which policies apply to specific traffic flows between network interfaces.
Options A and D are incorrect because the Implicit group typically does not include more than one deny policy, and there is no "sequence grouping view" in FortiGate. Option B is incorrect as the list is not displayed strictly by ID sequence.
Reference: FortiOS 7.4.1 Administration Guide: Firewall Policy Views
Which of the following are valid actions for FortiGuard category based filter in a web filter profile ui proxy-based inspection mode? (Choose two.)
- A . Warning
- B . Exempt
- C . Allow
- D . Learn
A,C
Explanation:
