Practice Free FCP_FGT_AD-7.4 Exam Online Questions
Which two IP pool types are useful for carrier-grade NAT deployments? (Choose two.)
- A . Port block allocation
- B . Fixed port range
- C . One-to-one
- D . Overload
A,B
Explanation:
The two IP pool types that are useful for carrier-grade NAT (CGNAT) deployments are:
Refer to the exhibit.
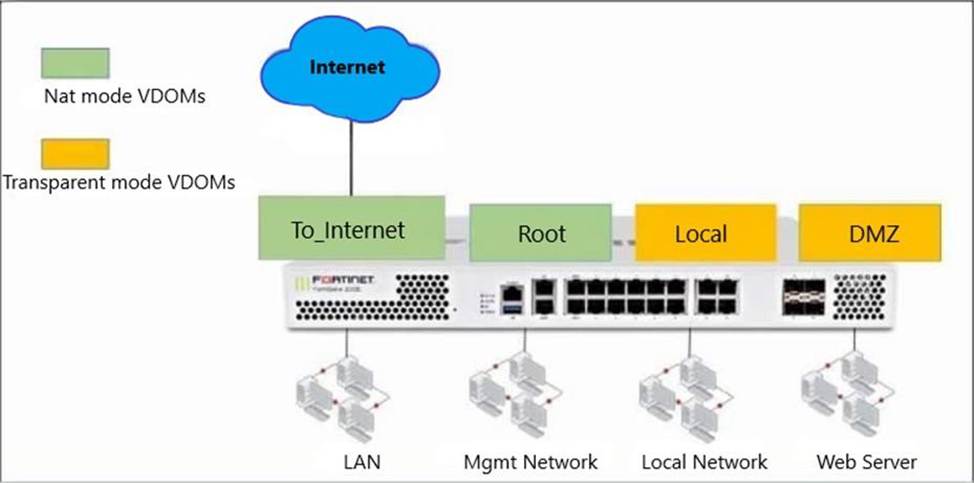
The Root and To_Internet VDOMs are configured in NAT mode. The DMZ and Local VDOMs are configured in transparent mode.
The Root VDOM is the management VDOM. The To_Internet VDOM allows LAN users to access the internet. The To_Internet VDOM is the only VDOM with internet access and is directly connected to ISP modem.
With this configuration, which statement is true?
- A . Inter-VDOM links are required to allow traffic between the Local and Root VDOMs.
- B . A default static route is not required on the To_Internet VDOM to allow LAN users to access the internet.
- C . Inter-VDOM links are required to allow traffic between the Local and DMZ VDOMs.
- D . Inter-VDOM links are not required between the Root and To_Internet VDOMs because the Root
VDOM is used only as a management VDOM.
A
Explanation:
Which two policies must be configured to allow traffic on a policy-based next-generation firewall (NGFW) FortiGate? (Choose two.)
- A . Firewall policy
- B . Policy rule
- C . Security policy
- D . SSL inspection and authentication policy
C,D
Explanation:
NGFW policy based mode, you must configure a few policies to allow traffic:
SSL inspection & Authentication, Security policy.
Security policies work with SSL Inspection & Authentication policies to inspect traffic. To allow traffic from a specific user or user group, both Security and SSL Inspection & Authentication policies must be configured.
If you are using Policy Based Mode, SSL Inspection & Authentication (consolidated) and Security Policy are required to allow traffic.
An administrator has a requirement to keep an application session from timing out on port 80.
What two changes can the administrator make to resolve the issue without affecting any existing services running through FortiGate? (Choose two.)
- A . Create a new firewall policy with the new HTTP service and place it above the existing HTTP policy.
- B . Create a new service object for HTTP service and set the session TTL to never
- C . Set the TTL value to never under config system-ttl
- D . Set the session TTL on the HTTP policy to maximum
A,B
Explanation:
The correct answers are:
Which three pieces of information does FortiGate use to identify the hostname of the SSL server when SSL certificate inspection is enabled? (Choose three.)
- A . The subject field in the server certificate
- B . The serial number in the server certificate
- C . The server name indication (SNI) extension in the client hello message
- D . The subject alternative name (SAN) field in the server certificate
- E . The host field in the HTTP header
A,C,D
Explanation:
When SSL certificate inspection is enabled, FortiGate uses the following three pieces of information to identify the hostname of the SSL server:
Refer to the exhibit.
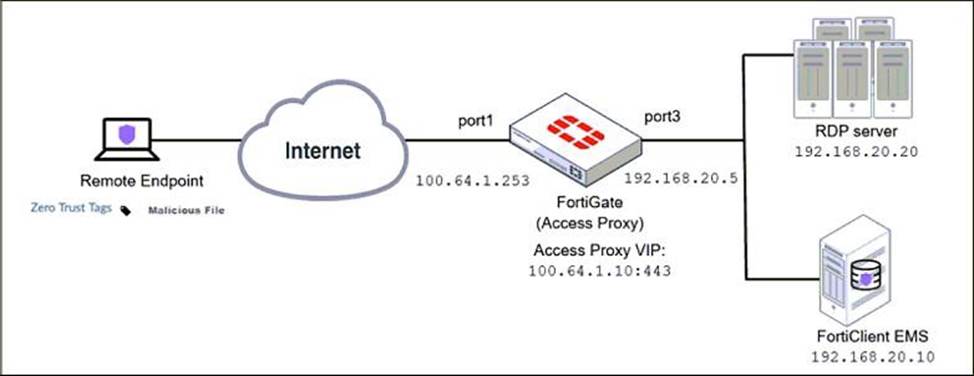
Based on the ZTNA tag, the security posture of the remote endpoint has changed.
What will happen to endpoint active ZTNA sessions?
- A . They will be re-evaluated to match the endpoint policy.
- B . They will be re-evaluated to match the firewall policy.
- C . They will be re-evaluated to match the ZTNA policy.
- D . They will be re-evaluated to match the security policy.
C
Explanation:
C. They will be re-evaluated to match the ZTNA policy.
Endpoint posture changes trigger active ZTNA proxy sessions to be re-verified and terminated if the endpoint is no longer compliant with the ZTNA policy.
You have enabled logging on your FortiGate device for Event logs and all Security logs, and you have set up logging to use the FortiGate local disk.
What is the default behavior when the local disk is full?
- A . Logs are overwritten and the only warning is issued when log disk usage reaches the threshold of 95%.
- B . No new log is recorded until you manually clear logs from the local disk.
- C . Logs are overwritten and the first warning is issued when log disk usage reaches the threshold of 75%.
- D . No new log is recorded after the warning is issued when log disk usage reaches the threshold of 95%.
C
Explanation:
C. Logs are overwritten, and the first warning is issued when log disk usage reaches the threshold of 75%.
When the log disk usage reaches 75%, a warning is issued, and logs are overwritten to make space for new logs. This allows the device to continue logging events while maintaining a threshold to prevent the disk from filling up completely.
First warning 75%, second 90% and final Warning 95%
Only 75% of the disk is available to store logs, this is distributed in the existing vdoms.
Diagnose sys logdisk usage — CLI command to verify this.
What must you configure to enable proxy-based TCP session failover?
- A . You must configure ha-configuration-sync under configure system ha.
- B . You do not need to configure anything because all TCP sessions are automatically failed over.
- C . You must configure session-pickup-enable under configure system ha.
- D . You must configure session-pickup-connectionless enable under configure system ha.
C
Explanation:
The correct answer is:
C. You must configure session-pickup-enable under configure system ha.
To enable proxy-based TCP session failover on a Fortinet FortiGate firewall, you must configure the session-pickup-enable setting under the high availability (HA) configuration. This setting allows the firewall to pick up and maintain TCP sessions after a failover event, ensuring continuity of service for established connections.
Refer to the exhibits, which show the firewall policy and the security profile for Facebook.
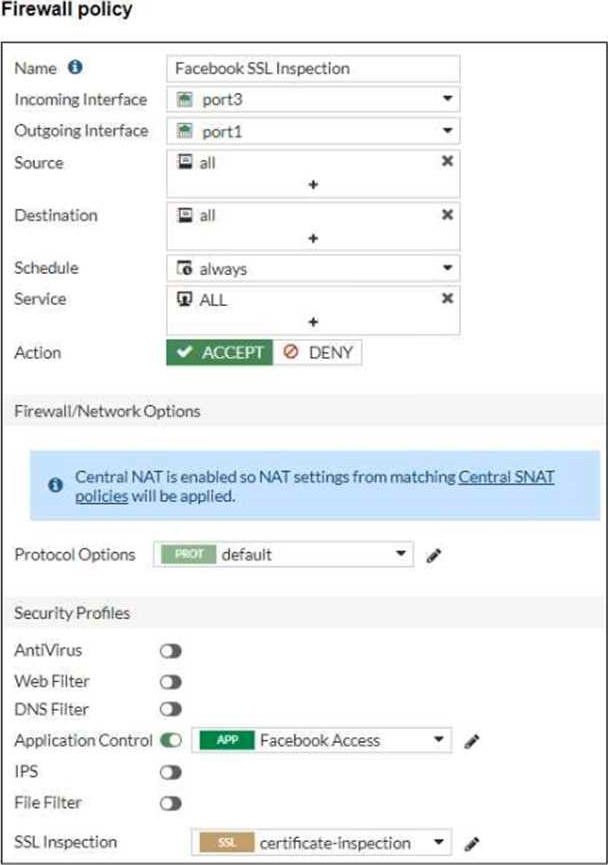
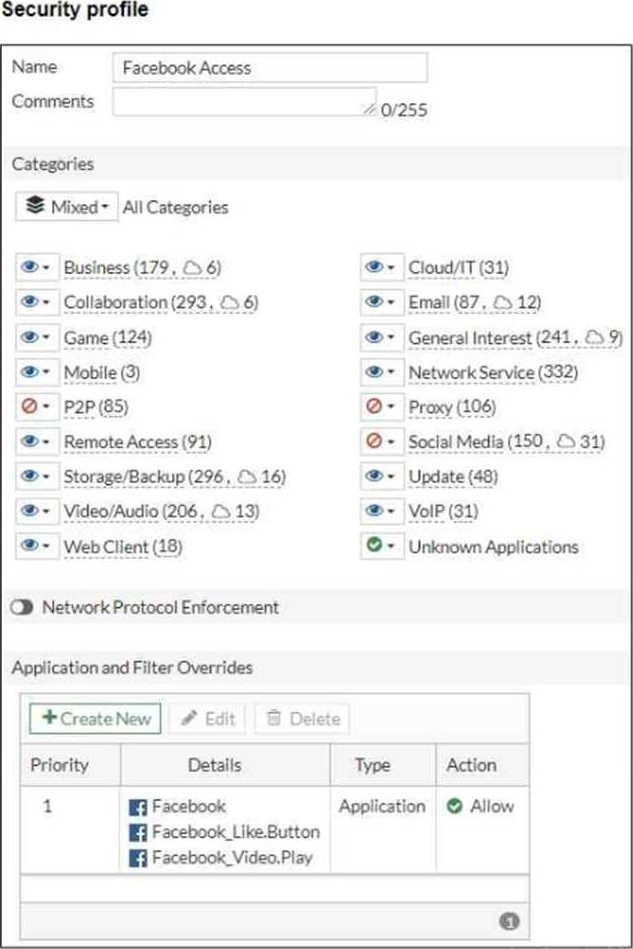
Users are given access to the Facebook web application. They can play video content hosted on Facebook but they are unable to leave reactions on videos or other types of posts.
Which part of the configuration must you change to resolve the issue?
- A . Make the SSL inspection a deep content inspection
- B . Add Facebook to the URL category in the security policy
- C . Disable HTTP redirect to HTTPS on the web browser
- D . Get the additional application signatures required to add to the security policy
D
Explanation:
In the security profile, there are application overrides for specific Facebook-related features, such as "Facebook" and "Facebook_Video.Play." However, the absence of specific signatures for actions like "Facebook_Like.Button" might be preventing reactions. You need to ensure that the necessary application signatures for all desired Facebook features, including reactions (like buttons), are included in the security policy. Therefore, retrieving or adding those signatures would resolve the issue.
An administrator needs to inspect all web traffic (including Internet web traffic) coming from users connecting to the SSL-VPN.
How can this be achieved?
- A . Assigning public IP addresses to SSL-VPN users
- B . Configuring web bookmarks
- C . Disabling split tunneling
- D . Using web-only mode
C
Explanation:
The correct answer is: C. Disabling split tunneling
Split tunneling allows VPN users to access both local and remote networks simultaneously. However, if you want to inspect all web traffic, including Internet traffic, coming from users connecting to the SSL-VPN, you should disable split tunneling. Disabling split tunneling forces all user traffic through the VPN tunnel, allowing you to inspect and control the traffic more effectively.
