Practice Free FCP_FCT_AD-7.2 Exam Online Questions
An administrator wants to simplify remote access without asking users to provide user credentials.
Which access control method provides this solution?
- A . ZTNA full mode
- B . SSL VPN
- C . L2TP
- D . ZTNA IP/MAC littering mode
A
Explanation:
Simplifying Remote Access:
The administrator wants to simplify remote access without asking users to provide user credentials.
Evaluating Access Control Methods:
ZTNA full mode can provide seamless access by leveraging device identity and posture, eliminating the need for user credentials for each access request.
Other methods like SSL VPN and L2TP typically require user credentials.
Conclusion:
The correct access control method that provides this solution is ZTNA full mode.
Reference: ZTNA section in the FortiGate Infrastructure 7.2 Study Guide.
A FortiClient EMS administrator has enabled the compliance rule for the sales department.
Which Fortinet device will enforce compliance with dynamic access control?
- A . FortiClient
- B . FortiClient EMS
- C . FortiGate
- D . FortiAnalyzer
C
Explanation:
Understanding Compliance Rules:
The compliance rule for the sales department needs to be enforced dynamically.
Enforcing Compliance:
FortiGate is responsible for enforcing compliance by integrating with FortiClient EMS to apply dynamic access control based on compliance status.
Conclusion:
The Fortinet device that will enforce compliance with dynamic access control is the FortiGate.
Reference: Compliance and enforcement documentation from FortiGate and FortiClient EMS study guides.
A FortiClient EMS administrator has enabled the compliance rule for the sales department.
Which Fortinet device will enforce compliance with dynamic access control?
- A . FortiClient
- B . FortiClient EMS
- C . FortiGate
- D . FortiAnalyzer
C
Explanation:
Understanding Compliance Rules:
The compliance rule for the sales department needs to be enforced dynamically.
Enforcing Compliance:
FortiGate is responsible for enforcing compliance by integrating with FortiClient EMS to apply dynamic access control based on compliance status.
Conclusion:
The Fortinet device that will enforce compliance with dynamic access control is the FortiGate.
Reference: Compliance and enforcement documentation from FortiGate and FortiClient EMS study guides.
Refer to the exhibit, which shows the endpoint summary information on FortiClient EMS.
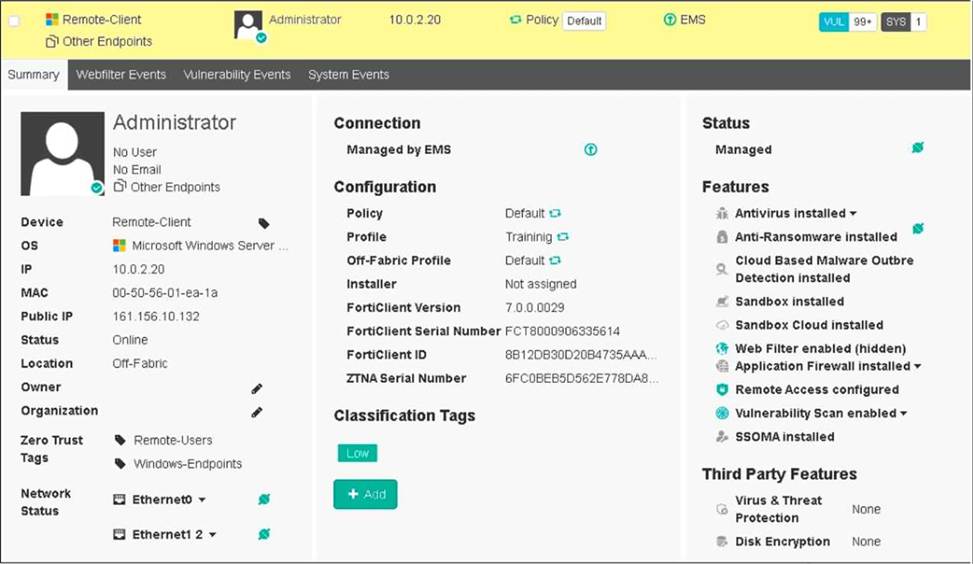
What two conclusions can you make based on the Remote-Client status shown above? (Choose two.)
- A . The endpoint is classified as at risk.
- B . The endpoint has been assigned the Default endpoint policy.
- C . The endpoint is configured to support FortiSandbox.
- D . The endpoint is currently off-net.
BD
Explanation:
Based on the Remote-Client status shown in the exhibit:
Endpoint Policy: The "Policy" field shows "Default," indicating that the endpoint has been assigned the Default endpoint policy.
Connection Status: The "Location" field shows "Off-Fabric," meaning that the endpoint is currently off the corporate network (off-net).
Therefore, the two conclusions that can be made are:
The endpoint has been assigned the Default endpoint policy.
The endpoint is currently off-net.
Reference
FortiClient EMS 7.2 Study Guide, Endpoint Summary Information Section Fortinet Documentation on Endpoint Policies and Status Indicators
Which two third-party tools can an administrator use to deploy FortiClient? (Choose two.)
- A . Microsoft Windows Installer
- B . Microsoft SCCM
- C . Microsoft Active Directory GPO
- D . QR code generator
BC
Explanation:
Administrators can use several third-party tools to deploy FortiClient:
Microsoft SCCM (System Center Configuration Manager): SCCM is a robust tool used for deploying software across large numbers of Windows-based systems. It supports deployment of FortiClient through its software distribution capabilities.
Microsoft Active Directory GPO (Group Policy Object): GPOs are used to manage user and computer settings in an Active Directory environment. Administrators can deploy FortiClient to multiple machines using GPO software installation settings.
These tools provide centralized and scalable methods for deploying FortiClient across numerous endpoints in an enterprise environment.
Reference
FortiClient EMS 7.2 Study Guide, FortiClient Deployment Section Fortinet Documentation on FortiClient Deployment using SCCM and GPO
Refer to the exhibits.
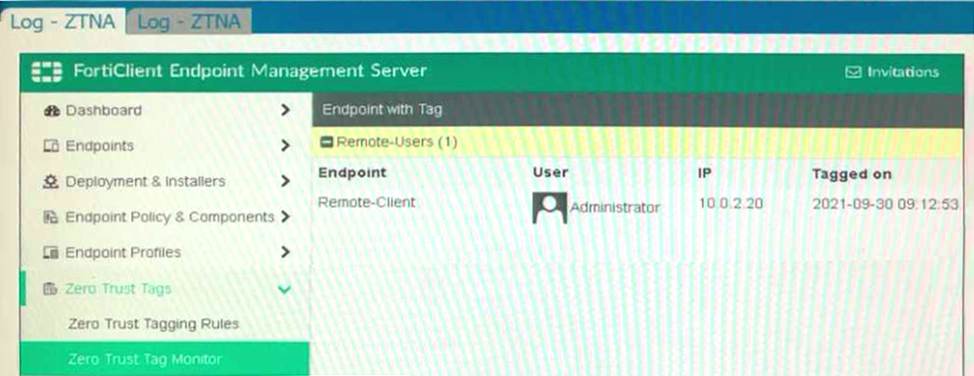
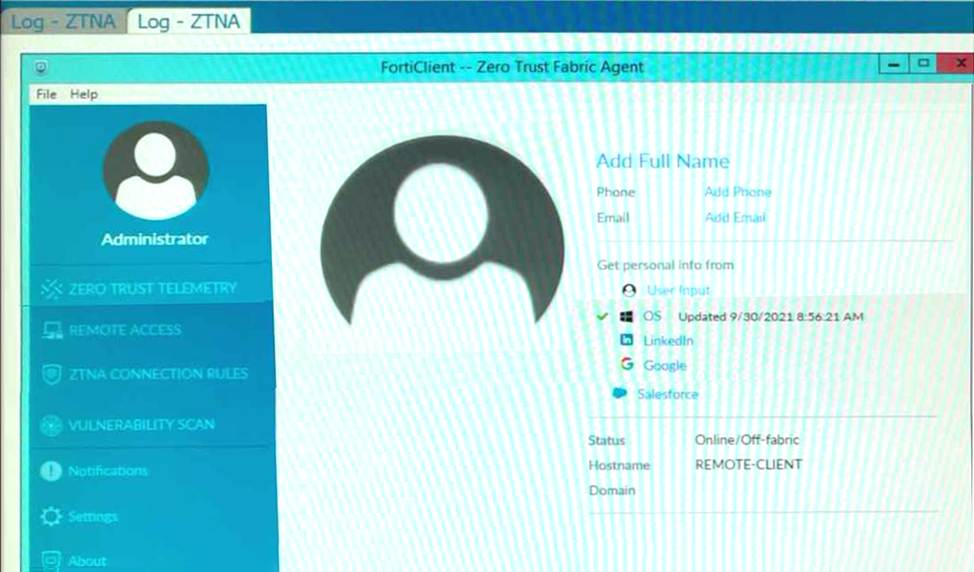
Which show the Zero Trust Tag Monitor and the FortiClient GUI status.
Remote-Client is tagged as Remote-Users on the FortiClient EMS Zero Trust Tag Monitor.
What must an administrator do to show the tag on the FortiClient GUI?
- A . Update tagging rule logic to enable tag visibility
- B . Change the FortiClient system settings to enable tag visibility
- C . Change the endpoint control setting to enable tag visibility
- D . Change the user identity settings to enable tag visibility
B
Explanation:
Based on the exhibits provided:
The "Remote-Client" is tagged as "Remote-Users" in the FortiClient EMS Zero Trust Tag Monitor. To ensure that the tag "Remote-Users" is visible in the FortiClient GUI, the system settings within FortiClient need to be updated to enable tag visibility.
The tag visibility feature is controlled by FortiClient system settings which manage how tags are displayed in the GUI.
Therefore, the administrator needs to change the FortiClient system settings to enable tag visibility.
Reference
FortiClient EMS 7.2 Study Guide, Zero Trust Tagging Section FortiClient Documentation on Tag Management and Visibility Settings
Which three features does FortiClient endpoint security include? (Choose three.)
- A . DLP
- B . Vulnerability management
- C . L2TP
- D . lPsec
- E . Real-lime protection
BDE
Explanation:
Understanding FortiClient Features:
FortiClient endpoint security includes several features aimed at protecting and managing endpoints.
Evaluating Feature Set:
Vulnerability management is a key feature of FortiClient, helping to identify and address vulnerabilities (B).
IPsec is supported for secure VPN connections (D).
Real-time protection is crucial for detecting and preventing threats in real-time (E).
Eliminating Incorrect Options:
Data Loss Prevention (DLP) (A) is typically managed by FortiGate or FortiMail.
L2TP (C) is a protocol used for VPNs but is not specifically a feature of FortiClient endpoint security.
Reference: FortiClient endpoint security features documentation from the study guides.
Refer to the exhibit.
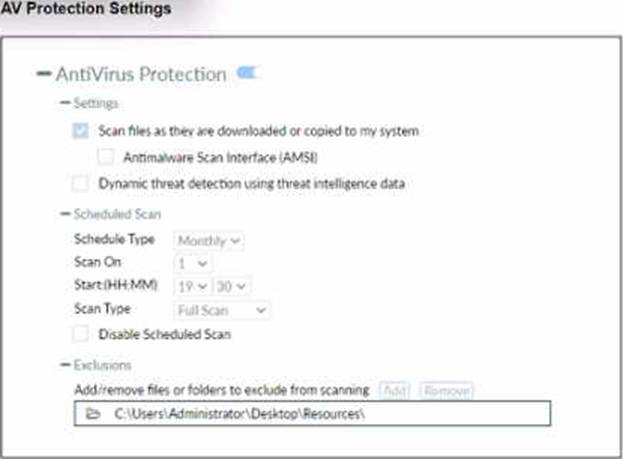
Based on The settings shown in The exhibit, which statement about FortiClient behaviour is Hue?
- A . FortiClient scans infected files when the user copies files to the Resources folder.
- B . FortiClient quarantines infected ties and reviews later, after scanning them.
- C . FortiClient copies infected files to the Resources folder without scanning them.
- D . FortiClient blocks and deletes infected files after scanning them.
A
Explanation:
Based on the settings shown in the exhibit, FortiClient is configured toscan files as they are downloaded or copiedto the system. This means that if a user copies files to the “Resources” folder, which is not listed under exclusions, FortiClient will scan these files for infections. The exclusion path mentioned in the settings, "C:UsersAdministratorDesktopResources", indicates that any files copied to this specific folder will not be scanned, but since the question implies that the “Resources” folder is not the same as the excluded path, FortiClient will indeed scan the files for infections.
Which statement about the FortiClient enterprise management server is true?
- A . It receives the configuration information of endpoints from ForuGate.
- B . It provides centralized management of multiple endpoints running FortiClient software.
- C . It enforces compliance on the endpoints using tags
- D . It receives the CA certificate from FortiGate to validate client certrficates.
An administrator configures ZTNA configuration on the FortiGate.
Which statement is true about the firewall policy?
- A . It redirects the client request to the access proxy.
- B . It uses the access proxy.
- C . It defines ZTNA server.
- D . It only uses ZTNA tags to control access for endpoints.
A
Explanation:
"The firewall policy matches and redirects client requests to the access proxy VIP" https://docs.fortinet.com/document/fortigate/7.0.0/new-features/194961/basic-ztna-configuration
