Practice Free FC0-U61 Exam Online Questions
A user is selecting software to use to prepare handouts for a presentation. The user would like the information to be easy to format and printer friendly.
Which of the following software types should the user select?
- A . Word processing
- B . Spreadsheet
- C . Text editor
- D . Visual diagramming
A
Explanation:
The software type that the user should select to prepare handouts for a presentation that are easy to format and printer friendly is word processing. Word processing is a type of software that allows users to create, edit, format, and print text documents, such as letters, reports, resumes, etc. Word processing software provides features such as fonts, styles, margins, alignment, bullets, numbering, tables, images, etc., that enable users to customize the appearance and layout of their documents. Word processing software also provides features such as spell check, grammar check, word count, etc., that enable users to improve the quality and accuracy of their documents. Word processing software can also support various file formats and printing options that enable users to save and print their documents easily and conveniently. Examples of word processing software include Microsoft Word, Google Docs, LibreOffice Writer, etc. Spreadsheet is not the software type that the user should select to prepare handouts for a presentation that are easy to format and printer friendly, but rather a type of software that allows users to create, edit, format, and print numerical data in rows and columns, such as budgets, invoices, charts, etc. Spreadsheet software provides features such as formulas, functions, graphs, pivot tables, etc., that enable users to perform calculations, analysis, or visualization on their data. Spreadsheet software can also support various file formats and printing options that enable users to save and print their data easily and conveniently. Examples of spreadsheet software include Microsoft Excel, Google Sheets, LibreOffice Calc, etc. Text editor is not the software type that the user should select to prepare handouts for a presentation that are easy to format and printer friendly, but rather a type of software that allows users to create, edit, or view plain text files, such as code, scripts, notes, etc. Text editor software provides features such as syntax highlighting, search and replace, indentation, etc., that enable users to manipulate text easily and efficiently. Text editor software does not provide features such as fonts, styles, images, etc., that enable users to customize the appearance or layout of their documents. Text editor software can also support various file formats but not printing options that enable users to save but not print their files easily and conveniently. Examples of text editor software include Notepad++, Sublime Text, Vim, etc.
Which of the following should be done first when working on a potential issue?
- A . Implement a solution.
- B . Escalate the issue.
- C . Research the issue.
- D . Gather information.
D
Explanation:
The first step when working on a potential issue should always be to gather information. This involves understanding the problem thoroughly by collecting data about the issue, such as symptoms, settings, and environmental conditions. Properly gathering information ensures that subsequent steps, such as research and resolution strategies, are based on a solid understanding of the problem, increasing the likelihood of an effective solution.
Reference: This approach is outlined in problem-solving methodologies within CompTIA IT Fundamentals, where gathering information is a critical first step before moving to diagnosis and resolution.
An administrator wants to block application traffic on specific ports from entering into the local area network.
Which of the following devices would be the best choice to perform this task?
- A . Router
- B . Firewall
- C . Switch
- D . Access point
B
Explanation:
To block application traffic on specific ports from entering a local area network (LAN), the most effective device is a firewall. A firewall serves as a security gatekeeper between your internal network and the outside world. It monitors incoming and outgoing network traffic based on predetermined security rules and can block specific traffic deemed unsafe or unauthorized. In this scenario, if the administrator wishes to prevent certain application traffic from entering the network, configuring the firewall to deny traffic coming through those specific ports would be an effective solution. This configuration helps in protecting the network against potential intrusions or harmful traffic that could exploit open ports.
Reference: Firewalls are covered extensively in CompTIA IT Fundamentals and other IT security documentation. These resources detail how firewalls can be configured to block specific types of traffic, a fundamental aspect of network security.
A user is trying to set up a new wireless access point.
Which of the following should the user do first?
- A . Change the SSID to a unique name.
- B . Change the default password.
- C . Enable WPA2 encryption.
- D . Enable the highest available wireless standard.
B
Explanation:
The first thing a user should do when setting up a new wireless access point is to change the default password. Default passwords are well-known and pose a significant security risk. Changing this ensures that unauthorized individuals cannot easily gain access to the access point’s management interface.
Joe, a developer, is writing a program in which he needs to store a number that changes over the duration of the program’s run.
Which of the following would Joe MOST likely use to accomplish this?
- A . Loop
- B . Variable
- C . Constant
- D . Function
B
Explanation:
A variable is a named memory location that can store a number or any other type of data that changes over the duration of the program’s run. A variable can be assigned a value, modified, or used in calculations or operations. A variable is different from a constant, which is a fixed value that does not change. A variable is also different from a loop, which is a control structure that repeats a block of code until a condition is met. A variable is also different from a function, which is a named block of code that performs a specific task and can be reused12.
Reference: = CompTIA IT Fundamentals (ITF+) Study Guide, 2nd Edition, Chapter 4: Software Development3; What is Variable? – Definition from Techopedia
Consider the following statements:
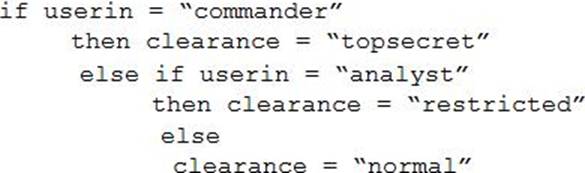
Given the input (userin) of “analyst”, to which of the following would the clearance variable be set?
- A . topsecret
- B . normal
- C . analyst
- D . restricted
D
Explanation:
Float is a data type that can store decimal or fractional numbers, such as 3.14, 0.5, or -2.75. Float would be the best data type to use for storing monetary values because monetary values often involve decimals, such as $1.99, 0.25,or-5.50. Integer is a data type that can only store whole numbers, such as 1, 0, or -2. Integer would not be suitable for storing monetary values that have decimals. The other options are not data types that can store numerical values.
Reference: CompTIA IT Fundamentals+ Study Guide: Exam FC0-U61, Second Edition, Chapter 4: Programming Concepts and Data Structures, page 146.
A game developer is purchasing a computing device to develop a game and recognizes the game engine software will require a device with high-end specifications that can be upgraded.
Which of the following devices would be BEST for the developer to buy?
- A . Laptop
- B . Server
- C . Game console
- D . Workstation
D
Explanation:
A workstation would be the best device for a game developer to buy if the game engine software requires high-end specifications and upgradability. A workstation is a computing device that is designed for professional or specialized applications that require high performance, reliability, and scalability. A workstation typically has more powerful components than a standard desktop computer, such as faster processors, larger memory, better graphics cards, and more storage options. A workstation can also be customized and upgraded to meet specific needs or preferences.
Reference: The Official CompTIA IT Fundamentals (ITF+) Study Guide (FC0-U61), page 26.
Which of the following is the best way to prevent malicious code from executing on a laptop based on attack signatures?
- A . Host-based firewall
- B . Antivirus
- C . Patching
- D . Network-based firewall
A user wants to prevent web history logging.
Which of the following features will allow the user to achieve this goal?
- A . Private browsing
- B . Pop-up blockers
- C . Bookmarks
- D . Accessibility
A
Explanation:
Private browsing is a feature available in most modern web browsers that allows users to surf the internet without storing web history, cookies, site data, or form information. This mode prevents the browser from keeping track of user activity, thus aiding in maintaining privacy and reducing digital footprints.
Reference: The utility and application of private browsing are discussed in the "Internet Services" section of CompTIA IT Fundamentals documentation, outlining its role in maintaining user privacy.
A database administrator has created a primary table and must ensure the date column in the table only accepts date values.
Which of the following does the administrator need to set?
- A . Schema
- B . Primary key
- C . Constrain!
- D . Permissions
