Practice Free D-PDD-DY-23 Exam Online Questions
A customer needs to use DD Retention Lock Compliance to ensure that data integrity is maintained.
Which PowerProtect DD systems meet the customer’s requirement?
- A . DD3300, DD6900, and DD9400
- B . DDVE, DD3300, and DD6900
- C . DD6900, DDVE, and DD9400
- D . DD9400, DDVE, and DD9900
In PowerProtect DD, in which folder are core files, logfiles, and upgrade packages located?
- A . /backup
- B . /ddvar
- C . /data/col1
- D . /var
DRAG DROP
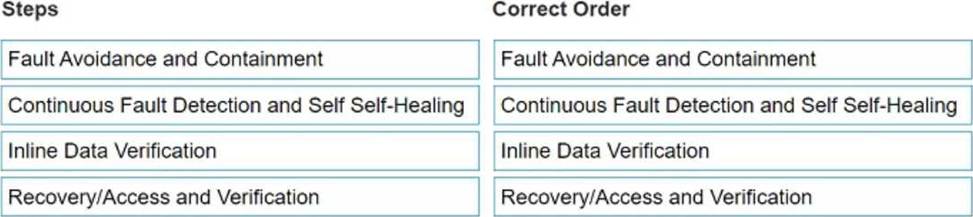
What is the correct order of operations for the Data Invulnerability Architecture (DIA) elements?

Explanation:
The correct order of operations for the Data Invulnerability Architecture (DIA) elements is as follows:
Fault Avoidance and Containment
Continuous Fault Detection and Self-Healing
Inline Data Verification
Recovery/Access and Verification
The Data Invulnerability Architecture (DIA) in Dell PowerProtect DD systems is designed to ensure data integrity and resiliency throughout the data storage process. Here’s how each element plays a role in this ordered sequence:
Fault Avoidance and Containment: This is the first layer of protection. DIA focuses on preventing faults before they occur and containing any potential issues, ensuring that faults do not propagate within the system. This stage is critical as it forms the foundational protection layer.
Continuous Fault Detection and Self-Healing: After implementing containment, the system continuously monitors for faults. It actively identifies and mitigates issues through self-healing mechanisms, addressing any detected errors autonomously to maintain data integrity.
Inline Data Verification: As data is written to storage, the inline data verification checks data integrity on the fly. This step ensures that any corruption or errors in data are detected immediately, enabling early intervention before data is permanently stored.
Recovery/Access and Verification: The final step ensures that, during data recovery, the integrity of the data is verified before it is accessed or restored. This stage completes the DIA cycle by confirming that data retrieved from storage is accurate and intact.
This ordered approach in DIA is designed to provide robust protection against data loss or corruption, making Dell PowerProtect DD appliances highly reliable for data protection needs.
What system role is required to create the second security officer for a PowerProtect DD?
- A . admin
- B . sysadmin
- C . limited-admin
- D . security officer
A customer’s Power Protect DD system is full. No data can be written or deleted from the system
Which two actions can the customer take to make capacity available on the system? (Select 2)
- A . Start file system cleaning
- B . Restart the file system
- C . Disable MTree replication
- D . Expire existing snapshots
- E . Remove core and autosupport files
An organization uses tape libraries in their current backup infrastructure. They have purchased a PowerProtect DD system and plan to use VTL to move from physical tape.
What is a consideration when configuring the tape size?
- A . Use multiple drives to write multiple streams
- B . Set retention periods for as long as possible
- C . Target multiple drives to write single stream
- D . Use larger tapes for multiple smaller datasets
The finance department requires PDFs older than 90 days to be archived through Cloud Tier into Azure Blob Storage. They want any PDFs older than 180 days archived into AWS S3.
Which data movement policy is used to archive files into Azure Blob Storage?
- A . App-driven
- B . Age-based
- C . Age-range
- D . Recall
How many cloud units are supported on a PowerProtect DD appliance when using Dell EMC Cloud Tier, and what is the maximum capacity for each unit?
- A . Two units, each up to half the active tier capacity
- B . Four units, each less than or equal to the active tier capacity
- C . Four units, each up to half the active tier capacity
- D . Two units, each less than or equal to the active tier capacity
Which command is used to restart the initial CLI configuration wizard?
- A . install config
- B . setup
- C . config setup
- D . config
Which is required to store and manage archive data on a single PowerProtect DD appliance to comply with regulatory standards?
- A . Dell EMC Cloud Tier
- B . Encryption for Data at Rest
- C . Retention Lock Governance
- D . Retention Lock Compliance
