Practice Free D-ISM-FN-23 Exam Online Questions
Which file system uses a MapReduce framework to run applications and a NameNode for managing the file system?
- A . New Technology File System (NTFS)
- B . Hadoop Distributed File System (HDFS)
- C . Network File System (NFS)
- D . Common Internet File System (CIFS)
What kind of ML explicitly requires splitting the data into training and testing datasets before running an algorithm against that data?
- A . Deep Learning
- B . Unsupervised Learning
- C . Reinforcement Learning
- D . Supervised Learning
Which method automatically allocates a large capacity secondary cache using SSD and SCM?
- A . Cache provisioning
- B . Volatile cache
- C . Cache tiering
- D . Non-volatile cache
Which Fibre Channel (FC) interconnectivity option is represented in the graphic?
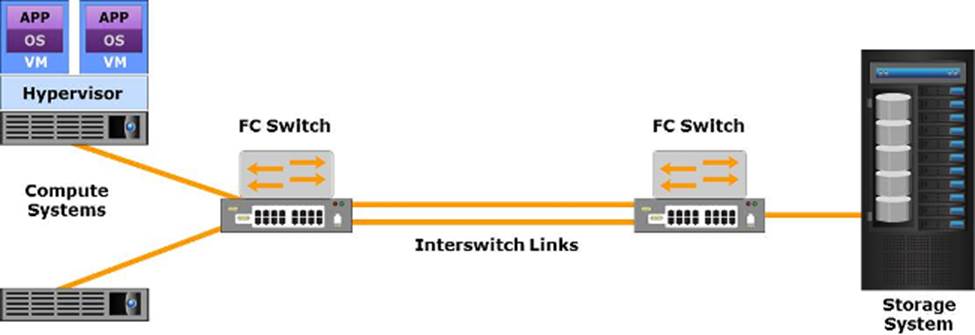
- A . FC-AL
- B . FCoE
- C . FC-SW
- D . Point-to-Point
Which method can an administrator use to establish a secure connection to a data center and perform management operations?
- A . Long distance VPN connection
- B . Remote access VPN connection
- C . Site-to-site VPN connection
- D . Intra-site VPN connection
What is an accurate statement about an FCoE environment?
- A . FC Forwarder must split an FC frame into two or more FCoE frames based on the Ethertype
- B . FCoE controller sends RSCNs to all nodes to provide access control
- C . FCoE ASIC encapsulates FCoE frames into FC frames based on FC-to-FCoE mapping
- D . FCoE network must be configured to support jumbo frames for optimal performance
An application generates 8400 small random I/Os at peak workloads with a read/write ratio of 2:1.
What is the disk load at peak activity for a RAID 5 configuration?
- A . 4800
- B . 11200
- C . 16800
- D . 22400
Why do organizations need a malware protection software?
- A . Secure critical applications by using strong credentials
- B . Prevent authorized modification of OS-sensitive areas
- C . Protect applications and the OS against trojan horse programs
- D . Prevent eavesdropping and tampering of application data
What is a specialized replication technique that enables moving data from one storage system to another within a data center without incurring downtime?
- A . VM-level backup
- B . Archive
- C . Migration
- D . Image-level backup
In an archiving environment, how is a content address created in a content addressable storage (CAS) system to store an object?
- A . From the metadata of an object.
- B . By using the logical address of the memory space.
- C . From the binary representation of an object.
- D . By using the physical address of the storage device.
