Practice Free D-ISM-FN-23 Exam Online Questions
Which technique prevents compute systems from gaining unauthorized access to storage volumes in a shared storage environment?
- A . Fabric binding
- B . Zoning
- C . Concatenating metaLUNs
- D . LUN masking
In a compute-based storage area network (SAN), what is a function of the metadata manager?
- A . Holds cluster-wide mapping information and load balancing in a compute-based SAN.
- B . Performs the I/O operations on the local storage of a compute system as requested by a client.
- C . Provides an interface to the software-defined storage controller.
- D . Controls all data read and write operations in a compute-based SAN.
What is an advantage of performing incremental backups compared to cumulative backups for the same data?
- A . Requires more time to perform data backup
- B . Storage capacity needed for backups is significantly reduced
- C . Requires more storage capacity for backup
- D . Reduces restore time but requires a maximum of two copies
What is an accurate statement about unstructured data?
- A . Created using only specific client devices and consumes large volumes of storage space
- B . Difficult to extract information from data using traditional applications and requires considerable resources
- C . Organized in rows and columns within named tables to efficiently store and manage data
- D . Created only using a specific tool and needs a relational database to store the data
Which type of data protection is used to move primary data to lower cost storage and helps to enforce compliance requirement?
- A . Archive
- B . Deduplication
- C . Backup
- D . Replication
Which cloud computing characteristic enables consumers to use cloud services on heterogeneous thin or thick client platforms?
- A . Resource pooling
- B . High availability
- C . On-demand self-service
- D . Broad network access
Which operation is represented in the exhibit?
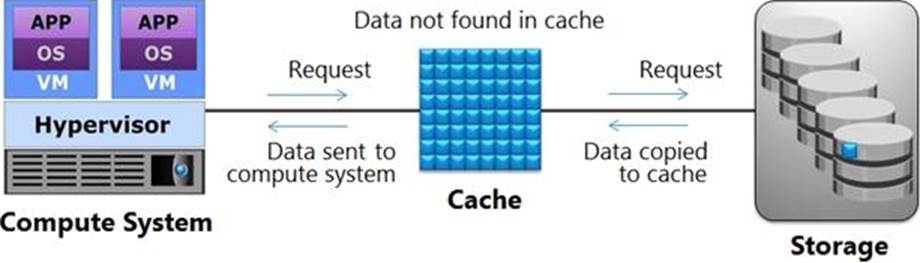
- A . Write-back Cache
- B . Read Cache Miss
- C . Write-through Cache
- D . Read Cache Hit
A customer wants 24×7 availability for a business application that uses a file system.
Which operation ensures a consistent replica of the file system?
- A . Unmount the file system prior to the creation of the replica
- B . Stop the application prior to the creation of the replica
- C . Flush the file system buffers after creation of the replica
- D . Flush the file system buffers before creation of the replica
In which data access method does the file system access an iSCSI storage system over a network?
- A . Block-based
- B . File-based
- C . Object-based
- D . Sector-based
Which LUN expansion technique provides both capacity expansion and performance improvement?
- A . Striped metaLUN
- B . Partitioned metaLUN
- C . Virtual metaLUN
- D . Concatenated metaLUN
