Practice Free D-ISM-FN-23 Exam Online Questions
Which EMC product is a hyper-scale storage infrastructure that provides universal accessibility with support for object and HDFS?
- A . ECS Appliance
- B . XtremIO
- C . Data Domain
- D . Centera
In which stage of the business continuity planning lifecycle does an organization identify critical business processes and assign recovery priorities?
- A . Analyzing
- B . Establishing objectives
- C . Designing and developing
- D . Implementing
What is an accurate statement about cache vaulting?
- A . Only writes to the cache are stored in a mirrored location during a power failure
- B . Cache data in multiple locations is made coherent during a power failure
- C . Contents of cache is dumped to a set of physical storage drives during a power failure
- D . Seals the cache and rejects any further reads or writes during a power failure
Which of the following is a key characteristic of a modern data center?
- A . Limited scalability
- B . High latency
- C . Virtualization
- D . Single-point of failure
An organization is interested in a cloud service that provides middleware, development tools, and database management systems for application development and deployment.
Which cloud service model meets these requirements?
- A . Software as a Service
- B . Infrastructure as a Service
- C . Platform as a Service
- D . Application as a Service
What is the goal of a business continuity solution?
- A . Reduce the amount of investment in protecting an organization’s business-related data.
- B . Avoid a disaster in a data protection environment to control the loss of data.
- C . Ensure information availability that is required to conduct vital business operations.
- D . Eliminate security threats in a data protection environment for continuous access to data.
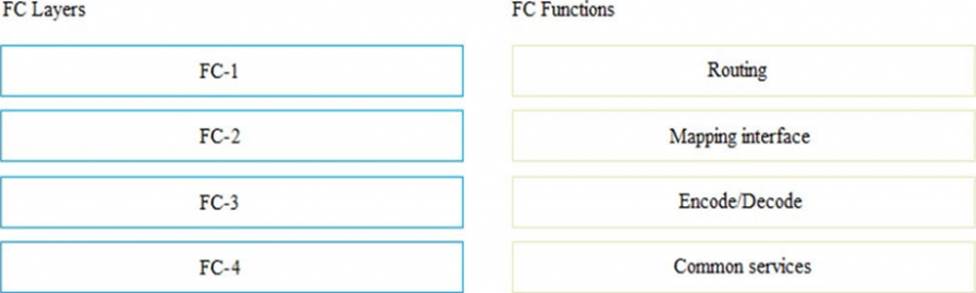
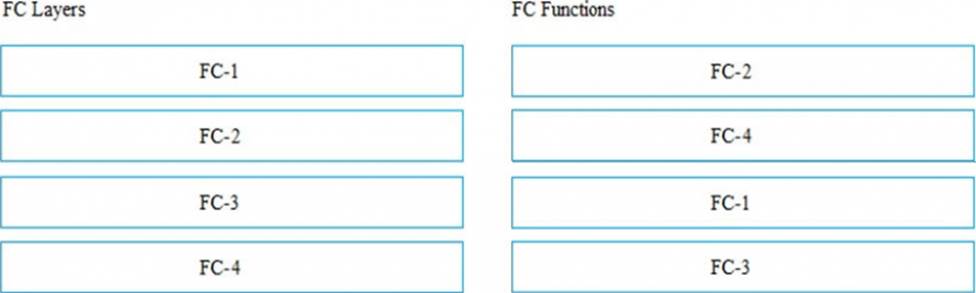
Match the Fibre Channel (FC) layers with their respective functions.
What is the significance of the CIA triad in storage security?
- A . It stands for Confidentiality, Integrity, and Availability, the three key principles of information security
- B . It is a type of malware targeting storage infrastructure
- C . It refers to a specific encryption algorithm used in storage
- D . It is a type of storage architecture
What accurately describes the flow control mechanism in an FC SAN?
- A . Both transmitting and receiving ports agree on the number of buffers available during port login
- B . Negotiation occurs between an E_Port and an F_Port, and between two N_Ports
- C . Credit value is incremented when a frame is transmitted and decremented upon receiving a response
- D . Receiver Ready (R_RDY) is sent from the receiving port if available credits reach zero
A system has three components and all three components need to be operational for 24 hours; Monday through Friday.
During a particular week, failure of component 3 occurred as follows:
– Tuesday = 8 AM to 1 PM
– Thursday = 5 PM to 10 PM
– Friday = 5 AM to 10 AM
What is the mean time between failures on component 3 for that week?
- A . 5 hours
- B . 35 hours
- C . 40 hours
- D . 51 hours
