Practice Free D-ISM-FN-23 Exam Online Questions
Why is it important to deploy virtual machine (VM) storage migration in a data center environment?
- A . Enable efficient management of storage capacity across storage systems
- B . Improve the security of applications running inside VMs on the migrated storage system
- C . Reduce a company’s overall storage system capacity requirements
- D . Enable VMs to continue functioning even if the source data is lost due to a failure
Which process is represented in the graphic?
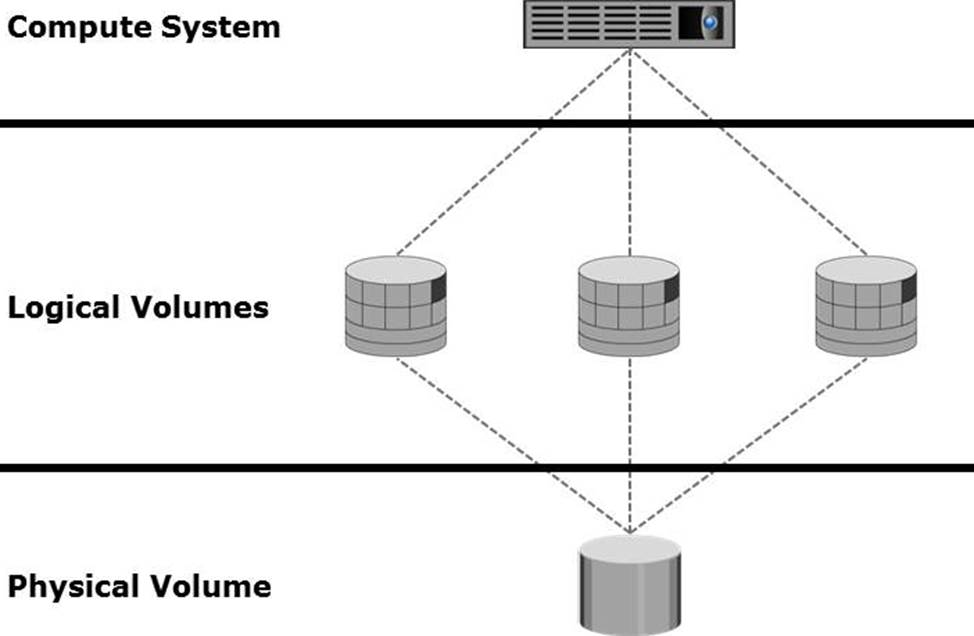
- A . Concatenation
- B . Partitioning
- C . Striping
- D . Shredding
What is used to implement a fully functional SAN?
- A . IPFC
- B . iSCSI
- C . VXLAN
- D . FCIP
Which type of Fibre Channel (FC) ports do the labels "X" and "Y" represent in the exhibit?
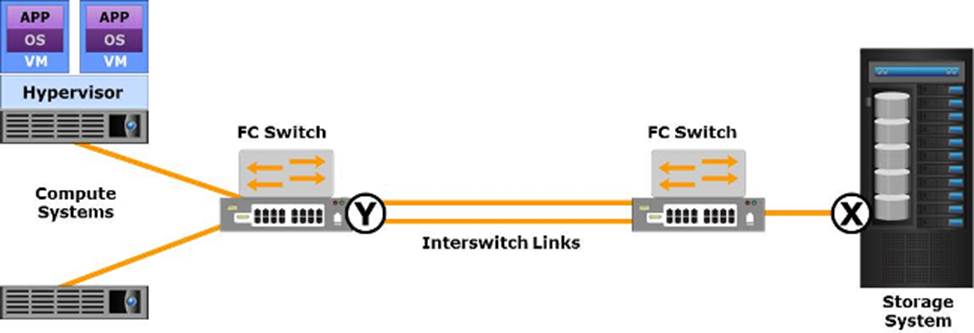
- A . X is an F_Port and Y is an E_Port
- B . X is an F_Port and Y is a G_Port
- C . X is a G_Port and Y is an N_Port
- D . X is an N_Port and Y is an E_Port
Which technology decouples the OS, applications, and user state from a physical compute system?
- A . Application virtualization
- B . Storage virtualization
- C . Thin client virtualization
- D . Desktop virtualization
What is an accurate statement about the Do-It-Yourself approach for building modern Infrastructure?
- A . Utilizes preconfigured preinstalled and prepackaged vendor ready solutions
- B . Combines the datacenter components into a single standalone computing platform managed by software
- C . Utilizes products and services from the vendors that provide specific functions with more configuration options
- D . Combines datacenter components into a distributed infrastructure platform managed by software
A company’s assets are continuously under attack.
To deploy a security control mechanism to protect these assets, what should be considered?
- A . Minimize the work factor
- B . Easy access to assets by authorized users
- C . Limited access to assets by unauthorized users
- D . Maximize the attack surface
In a data center, which type of connectivity is essential for disaster recovery?
- A . Intranet
- B . Dial-up
- C . Redundant internet connections
- D . Bluetooth
Which three parameters define information availability in a modern data center environment?
- A . Reliability – Accessibility – Timeliness
- B . Capacity – Availability – Security
- C . Confidentiality – Integrity – Availability
- D . Reliability – Integrity – Performance
What is used to track where objects and metadata are stored in an OSD system?
- A . Object storage database
- B . Object ID algorithm
- C . Object fingerprinting
- D . Globally unique identifier
