Practice Free D-CSF-SC-23 Exam Online Questions
What is a valid order of steps from the Incident Response Lifecycle?
- A . Preparation
Eradication
Containment
Analysis
Recovery - B . Containment
Detection
Analysis
Eradication
Prevention - C . Containment
Analysis
Detection
Eradication
Communication - D . Preparation
Detection
Containment
Eradication
Recovery
You have been asked by your organization to:
– Assist in developing an organizational understanding for managing cybersecurity risk to systems, people, assets, data, and capabilities
– Outline appropriate safeguards to ensure delivery of critical infrastructure services to limit or contain the impact of a potential cybersecurity event
– Define the appropriate activities to identify the occurrence of a cybersecurity event by enabling timely discovery
– Determine the appropriate business outcome by planning, communicating, analyzing, mitigating, and improving the process
– Identify the appropriate activities to maintain plans for resilience and restore capabilities or services impaired due to a cybersecurity incident
Based on these details, what would be the correct sequence of steps to take?
- A . Recover
Detect
Protect
Respond
Identify - B . Recover
Detect
Protect
Identify
Respond - C . Recover
Protect
Identify
Respond
Detect - D . Identify
Protect
Detect
Respond
Recover
Which document is designed to limit damage, reduce recovery time, and reduce costs where possible to the organization?
- A . Business Impact Analysis
- B . Business Continuity Plan
- C . Risk Assessment Strategy
- D . Incident Response Plan
Refer to the exhibit.
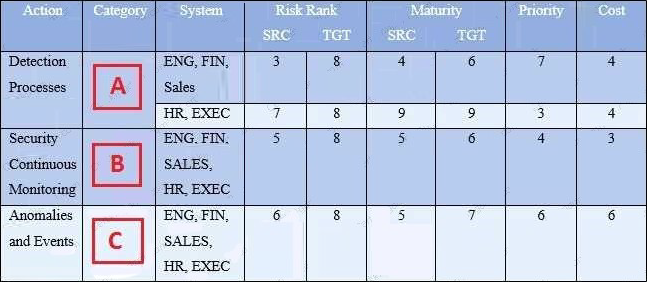
Your organization’s security team has been working with various business units to understand their business requirements, risk tolerance, and resources used to create a Framework Profile. Based on the Profile provided, what entries correspond to labels A, B, and C?

- A . Option A
- B . Option B
- C . Option C
