Practice Free D-CSF-SC-23 Exam Online Questions
Which category addresses the detection of unauthorized code in software?
- A . PR.DS
- B . DE.DP
- C . PR.AT
- D . DE.CM
Assume that a DDoS attack has been occurring for 72 minutes.
What determines who talks to external stakeholders?
- A . Business Continuity Plan
- B . Communication Plan
- C . Business Impact Analysis
- D . Incident Response Plan
At what cyber kill chain stage do attackers use malware to exploit specific software or hardware vulnerabilities on the target, based on the information retrieved at the reconnaissance stage?
- A . Installation
- B . Reconnaissance
- C . Weaponization
- D . Delivery
A company implemented an intrusion detection system. They notice the system generates a very large number of false alarms.
What steps should the company take to rectify this situation?
- A . Re-evaluate the Baseline and make necessary adjustments to the detection rules
- B . Replace the intrusion detection system with an intrusion protection system
- C . Define how to identify and disregard the false alarms
- D . Consider evaluating a system from another vendor
What is used to ensure an organization understands the security risk to operations, assets, and individuals?
- A . Risk Management Strategy
- B . Risk Assessment
- C . Operational Assessment
- D . Risk Profile
Your data center uses a diesel generator as backup for two different power grids provided by your regional power company. During a period of unprecedented heat, you experience brown-outs on both grids simultaneously.
The diesel generator starts up but only runs for two minutes before it also shuts down, leaving your entire data center down until grid power can be restored. Further inspection reveals a clogged fuel filter.
Failing to schedule preventive service for the backup generator is a failure in which function?
- A . Recover
- B . Respond
- C . Detect
- D . Protect
Refer to the exhibit.
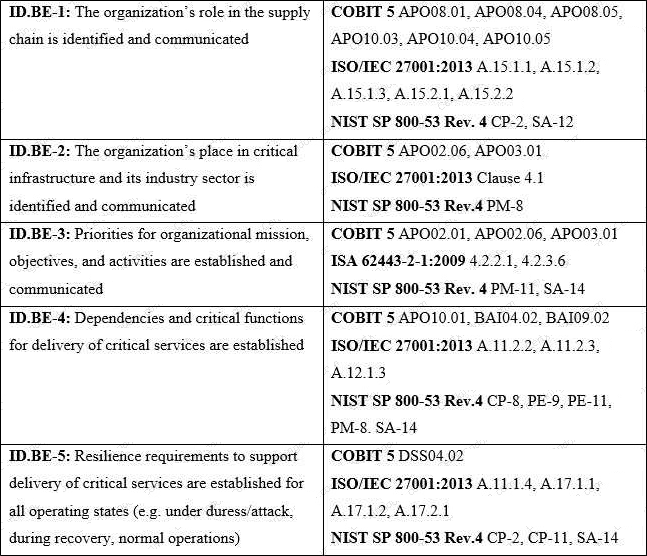
What type of item appears in the second column of the table?
- A . Subcategory
- B . Informative Reference
- C . Function
- D . Tier
What procedure is designed to enable security personnel to detect, analyze, contain, eradicate, respond, and recover from malicious computer incidents such as unauthorized changes to system hardware, software, or data?
- A . Emergency Analysis Plan
- B . Crisis Communication Plan
- C . Disaster Recovery Plan
- D . Incident Response Plan
You have completed a review of your current security baseline policy. In order to minimize financial, legal, and reputational damage, the baseline configuration requires that infrastructure be categorized for the BIA.
Which categorizations are necessary for the BIA?
- A . Mission critical and business critical only
- B . Mission critical, safety critical, and business critical
- C . Security critical, safety critical, and business critical
- D . Mission critical and safety critical only
The Disaster Recovery Plan must document what effort in order to address unrecoverable assets?
- A . RTO savings
- B . Recovery priority
- C . Recovery resources
- D . Recovery resources
